Network Security and Mitigation Strategies Answers
Edith Cowan University
Assessment 2: Report
Outcomes
The purpose of this assessment task is to apply the student’s understanding and knowledge gained from the weekly content in articulating and writing a report that:
- analyses contemporary network security issues and develops appropriate mitigation strategies, and
- evaluates a contemporary network for vulnerabilities.
Overview
Internet of Things (IoT) devices can be used to sense and share data from its surrounding environment for various purposes that can be useful for both humans and machines. These can be as simple as measuring the temperature of a room or more critical tasks such as monitoring the heart-rate of a sick patient in a hospital. The advances in hardware design, communication protocols, and computing technologies have created an ecosystem of a variety of IoT devices by numerous vendors and underlying infrastructure.
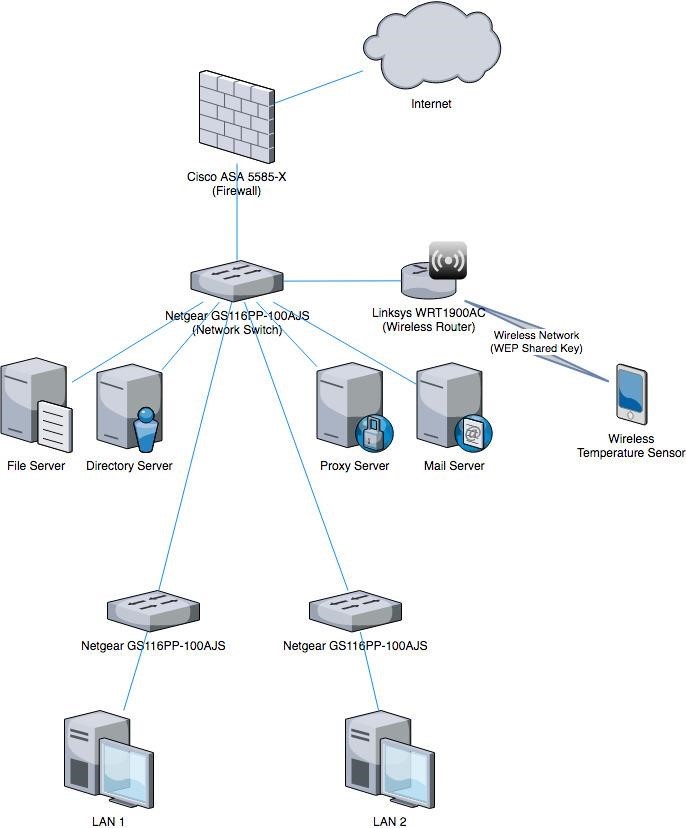
The network diagram provided (Figure 1 - see below) illustrates the various IoT devices integrated in a medium sized organisation’s IT network. Table 1 (see below) provides detailed specifications of the devices including hardware, software, and firmware details. Although the network is already secured with various defences, there are several problems that can lead to the organisation being compromised by cyber criminals.
Instructions
You have been hired as an external cyber security consultant to analyse the network for security issues and recommend solutions to mitigate these risks in the form of a technical report. The report is intended to be submitted to the management committee of the organisation. Therefore, highly technical concepts must be further described to a level understood by a novice audience.
Your report should consist of the following:
- Identify and contextualise two (2) security issues related to the IoT devices and two (2) security issues related to the IT infrastructure. You may consider aspects related to hardware, software, firmware, and protocols.
- Further support the above security issues by describing an actual attack that has occurred for both IoT and IT.
- Explain two vulnerabilities including the CVE that exist in this organisation.
- Propose and justify solutions to address the issues that you have identified in the task (1).
Please note that discussions related to security policies are beyond the scope of this assessment and therefore should be excluded from your report.
Marking Criteria
Each of the following criteria are worth 8 marks, with a total of 40 marks for the whole assessment.
- Identification of security issues (two for IoT and two for IT)
- Actual attacks described for IoT and IT
- Two vulnerabilities/CVE explained
- Solutions proposed and justified to address the four security issues identified
- Quality of report based on sources and referencing, depth of research, critique, and writing
Resources
- PDF/SVG/draw.io File
- Report template
Table 1
|
Device |
Details |
|
Cisco ASA 5585-X |
Used as the edge firewall for the organisation. Last software/firmware update unknown. |
|
Netgear GS116PP-100AJS |
Unmanaged network switch. |
|
Linksys WRT1900AC |
Wireless router using WEP shared key authentication. |
|
Wireless Temperature Sensor |
Custom built temperature sensor. Waterproof DS18B20 Digital temperature sensor connected to an ESP8266 board. Using MQTT to communicate to an Ubuntu desktop installed in LAN1. |
|
File Server |
Windows Server 2016 |
|
Directory Server |
Windows Server 2016 |
|
Proxy Server |
Ubuntu Server 16.04 LTS Squid proxy |
|
Mail Server |
Ubuntu Server 16.04 LTS Postfix 3.2 SquirrelMail 1.4.23 Apache 2 PHP 5 |
|
LAN 1 |
Various Desktop configurations 9 x Windows 10 PCs 1 x Ubuntu Desktop 18.10 running the MQTT broker software for the temperature sensor |
|
LAN 2 |
Various Desktop configurations 15 x Windows 10 PCs |
Report Template
The report should be properly word processed and formatted accordingly to a professional standard and suitable to the target audience. As a minimum, the report should have the following sections. You may add sub-headings or other content as required.
- Cover Page
- Table of Contents
- Introduction
- Security Issues
- Attack Scenarios
- Vulnerabilities
- Proposed Countermeasure(s)/Solution(s)
- References
- Appendices (as needed)
Question 1: Hubs are no longer in common use. Why is this and what have they been replaced with in organisations? What could a hub be used for in modern networking?
Question 2: What is a router used for? How is this different from what a switch is used for?
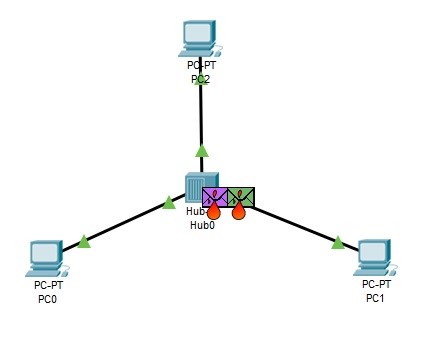
Question 3: Use Cisco Packet Tracer to connect three computers via a hub (see the following image) and configure them with static IP addresses.
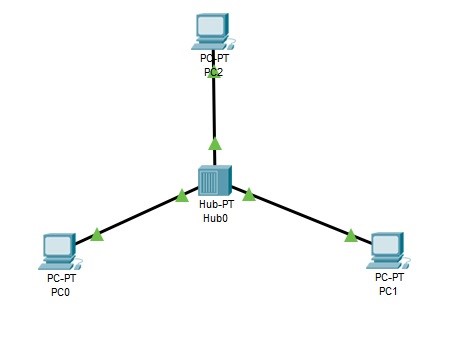
What happens when two PDUs are sent at the same time (as in the following image)?
Week-5
You have been asked to design a solution for connecting two buildings with a cabled connection. Your design will lead to a project where a buried cable will be run between these two buildings. The buildings are 120m apart from basement wall to basement wall. What solution would you choose? Why? What factors would you consider when coming to this conclusion?
Week-6
Question 1: What is the primary purpose of a VPN? What are the differences between a PPTP VPN, an L2TP VPN and an OpenVPN VPN?
Question 2: What is the difference between PaaS and IaaS in cloud computing? What kind of businesses are most likely to use each?
Question 3: What does the “Asynchronous” part of the ADSL protocol refer to? How does this function?
Question 4: How do most network firewalls tell the difference between different kinds of network traffic? (eg. how could a firewall know to block RDP connections but not HTTP connections?)
Diploma Universities Assignments
Laureate International Universities Assignment
Holmes Institute Assignment
Tafe NSW
Yes College Australia
ACC508 Informatics and Financial Applications Task 2 T2, 2019
ACC512 Accounting
ACC520 Legal Regulation of Business Structures Semester 2, 2019
ACCT20074 Contemporary Accounting Theory Term 2 Assessment 3
AERO2463 Computational Engineering Analysis : Assignment 4
B01DBFN212 Database Fundamentals Assessment 1
BE01106 - Business Statistics Assignment
BFA301 Advanced Financial Accounting
BFA504 Accounting Systems Assessment 3
BSB61015 Advanced Diploma of Leadership and Management
BSBADV602 Develop an Advertising Campaign
BSBCOM603 Plan and establish compliance management systems case study
BSBCOM603 Plan and establish compliance management systems Assessment Task 1
BSBCOM603 Plan and establish compliance management systems Assessment Task 2
BSBCOM603 Plan and establish compliance management systems Assessment Task 3
BSBFIM501 Manage Budgets And Financial Plans Assessment Task 1
BSBHRM602 Manage Human Resources Strategic Planning
BSBINM601 Manage Knowledge and Information
BSBWOR501 Assessment Task 3 Plan Personal Development Plan Project
BSBMGT517 Manage Operational Plan
BSBWHS521 Ensure a Safe Workplace For a Work Area
BSBWRK510 Manage employee relations
BUSS1030 Accounting, Business and Society
CAB202 Microprocessors and Digital Systems Assignment Help
CHC40213 Certificate IV in Education Support
CHCAGE001 Facilitate the empowerment of older people
CHCAGE005 Provide support to people living with dementia
CHCCCS023 Support independence and wellbeing
CHCCCS025 Support relationships with carers and families
CHCCOM005 Communicate and CHCLEG001 Work Legally Ethically
CHCDIS002 Follow established person-centred behaviour supports
CHCECE019 Early Childhood Education and Care
CHCHCS001 Provide home and community support services
COMP10002 Foundations of Algorithms
COMP90038 Algorithms and Complexity
COSC2633/2637 Big Data Processing
COSC473 Introduction to Computer Systems
CPCCBC5011A Manage Environmental Management Practices And Processes In Building And Construction
CPCCBC5018A Apply structural Principles Medium rise Construction
CSE3OSA Assignment 2019
ELEC242 2019 Session 2
ENN543 Data Analytics and Optimisation
ENN543 Data Analytics and Optimisation Semester 2, 2019
FINM202 Financial Management Assessment 3 Group Report
Forensic Investigation Case Assignment ECU University
HA2042 Accounting Information Systems T2 2019
HC1010 Holmes Institute Accounting For Business
HC2112 Service Marketing and Relationship Marketing Individual Assignment T2 2019
HC2121 Comparative Business Ethics & Social Responsibility T2 2019
HI5002 Holmes Institute Finance for Business
HI5003 Economics for Business Trimester 2 2019
HI5004 Marketing Management T1 2020 Individual Report
HI5004 Marketing Management T1 2020 Group Report
HI5004 Holmes Institute Marketing Management
HI5014 International Business across Borders Assignment 1
HI5014 International Business across Borders
HI5017 Managerial Accounting T2 2019
HI5017 Managerial Accounting T1 2019
HI5019 Tutorial Questions 1
HI5019 Strategic Information Systems for Business and Enterprise T1 2020
HI5019 Holmes Institute Strategic Information Systems T2
HI5019 T2 2019
HI5019 T1 2019
HI5020 Corporate Accounting T3 2019
HI5020 Corporate Accounting T2 2019
HI6005: Management and Organisations in a Global Environment
HI6006 Tutorial questions
HI6006 Competitive Strategy Individual T1 2020
HI6006 Holmes Institute Competitive Strategy
HI6006 Competitive Strategy T3 2019
HI6007 Statistics for business decisions
HI6007 Assessment 2 T1 2020
HI6007 T1 2019
HI6008 T2 2019
HI6008 Holmes Institute Research Project
HI6025 Accounting Theory and Current Issues
HI6026 Audit, Assurance and Compliance Assignment Help
HI6026 Audit, Assurance and Compliance
HI6027 business and corporate law tutorial Assignment T1 2021
HI6027 Business and Corporate Law T3 2019
HI6027 Business and Corporate Law T2 2019
HI6028 Taxation Theory, Practice and Law T2 2021
Hi6028 taxation theory, practice and law Final Assessment t1 2021
HI6028 Taxation Theory, Practice and Law T2 2019
HI6028 Taxation Theory T1 2019
HI6028 Taxation Law Holmes
HLTAAP001 Recognise healthy body systems
HLTWHS002 Follow safe practices for direct client care
HOTL5003 Hotel Property and Operations
HPS771 - Research Methods in Psychology A
HS2021 Database Design
ICTICT307 Customise packaged software applications for clients
IFN619 Data Analytics for Strategic Decision Makers
INF80028 Business Process Management Swinburne University
ISY2005 Case Assignment Assessment 2
ISYS326: Information Systems Security Assignment 2, Semester 2, 2019
ITAP3010 Developing Data Access Solutions Project
ITECH1103- Big Data and Analytics – Lab 3 – Working with Data Items
ITECH1103- Big Data and Analytics Assignment Semester 1, 2020
ITECH 5500 Professional Research and Communication
Kent Institute Australia Assignment
MA5830 Data Visualisation Assignment 2
MGMT7020 Project Management Plan
Mgt 301 Assessment 3
MGT215 Project Management Individual Assignment
MIS102 Data and Networking Assignment Help
MITS4002 Object Oriented Software Development
MITS5002 Software Engineering Methodology
MKT01760 Tourism Planning Environments Assessment 4
MKT01760 Tourism Planning Environments
MKT01906 International Tourism Systems
MKT5000 Marketing Management S2 2019
MNG03236 Report Writing SCU
MRE5003 Industrial Techniques In Maintenance Management Assignment 4
MRE5003 Industrial Techniques In Maintenance Management Assignment 3
MRE5003 Industrial Techniques In Maintenance Management
Network Security and Mitigation Strategies Answers
NIT2213 Software Engineering Assignment
NSB231 Integrated Nursing Practice Assessment Task 1
Science Literacy Assessment 4
SIT323 Practical Software Development T 2, 2019
SIT718 Using aggregation functions for data analysis
SITXCOM002 Show Social and Cultural Sensitivity
TLIL5055 Manage a supply chain
TLIR5014 Manage Suppliers
USQ ACC5502 Accounting and Financial Management
UTS: 48370 Road and Transport Engineering Assessment 2
CHCAGE001 Facilitate the empowerment of older people
CHCAGE005 Provide support to people living with dementia
CHCCCS011 Meet personal support needs
CHCCCS015 Provide Individualised Support
CHCCCS023 Support independence and wellbeing
CHCCCS025 Support relationships with carers and families
CHCCOM005 Communicate and work in health or community services
CHCDIS001 Contribute to ongoing skills development
CHCDIS002 Follow established person-centred behaviour supports
CHCDIS003 Support community participation and social inclusion
CHCDIS005 Develop and provide person-centred service responses
CHCDIS007 Facilitate the empowerment of people with disability
CHCDIS008 Facilitate community participation and social inclusion
CHCDIS009 Facilitate ongoing skills development
CHCDIS010 Provide person-centred services
CHCDIV001 Work with diverse people
CHCHCS001 Provide home and community support services
CHCLEG001 Work legally and ethically
CHCLEG003 Manage legal and ethical compliance
HLTAAP001 Recognise healthy body systems
HLTAID003 Provide First Aid
HLTHPS007 Administer and monitor medications
HLTWHS002 Follow safe work practices for direct client care
Assignment 2 Introduction to Digital Forensics
MGT603 Systems Thinking Assessment 1
MGT603 Systems Thinking Assessment 2
Hi5017 Managerial Accounting T1 2021
HI6028 Taxation Theory, Practice and Law T1 2021
OODP101 Assessment Task 3 T1 2021
ITNE2003R Network Configuration and Management Project
Australia Universities
ACT
Australian Catholic University
Australian National University
Bond University
Central Queensland University
Charles Darwin University
Charles Sturt University
Curtin University of Technology
Deakin University
Edith Cowan University
Flinders University
Griffith University
Holmes Institute
James Cook University
La Trobe University
Macquarie University
Monash University
Murdoch University
Queensland University of Technology
RMIT University
Southern Cross University
Swinburne University of Technology
University of Adelaide
University of Ballarat
University of Canberra
University of Melbourne
University of Newcastle
University of New England
University of New South Wales
University of Notre Dame Australia
University of Queensland
University of South Australia
University of Southern Queensland
University of Sydney
University of Tasmania
University of Technology Sydney
University of the Sunshine Coast
University of Western Australia
University of Wollongong
Victoria University
Western Sydney University
Year 11 - 12 Certification Assignment
Australian Capital Territory Year 12 Certificate
HSC - Higher School Certificate
NTCE - Northern Territory Certificate of Education
QCE - Queensland Certificate of Education
SACE - South Australian Certificate of Education
TCE - Tasmanian Certificate of Education
VCE - Victorian Certificate of Education
WACE - Western Australia Certificate of Education
Assignment Service Australia | CDR Writing Help | TAFE Assignment Help | Perth Assignment Help | Melbourne Assignment Help | Darwin Assignment Help | Adelaide Assignment Help | Assignment Help Victoria | Sydney Assignment Help | Canberra Assignment Help | Brisbane Assignment Help | CDR for Australian immigration | Course For Australian History


