VU21993 - Secure a networked personal computer Assessment Task 3
Assessment Task Instructions
Scenario: Migrating an insecure infrastructure to the cloud
Acme.meme is booming – their single web server and internal company file server are struggling to meet demand. The company also has been receiving feedback about poor security practices. To solve both issues, they’re migrating all services to the cloud and improving each service.
General requirements
Company policy now requires all accounts must use 10+ character passwords
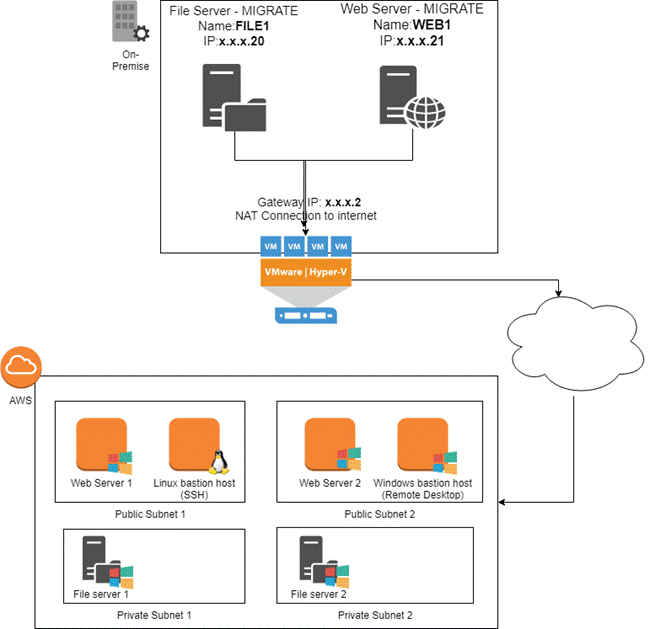
Phase 1 : Create the on-premise environment (Virtualisation using VMWare)
Company data: On Canvas in Session 12 (ITAdmin.zip, ACME_Website.zip)
General requirements:
Create two virtual machines running Windows Server 2019
Change the IP addresses to static (as documented in network diagram)
Servers should be named descriptively (change it from the default random name) (screenshot 1)
Enable VMWare Remote Access (VNC) on both VMs (screenshot 2)
On-premise File server:
Install and enable the File Server role
Create two users: ITAdmin (full access) and staff (limited user) (Screenshot 3)
Set up a single share named CompanyFiles (staff user has full access) (Screenshot 4)
Install updates (Screenshot 5)
Import the files from Canvas(ITAdmin.zip) into CompanyFiles
o Organise the files into folders: e.g. JPG files into Pictures, DOC files into Documents
On-premise Web server
Install and enable the Web server role
- Install updates
Empty the c:\inetpub\wwwroot folder and Import the data from Canvas(ACME_Website.zip)
Test it by opening Explorer and browsing to http://localhost (Screenshot 6)
When complete, back up your VM image using VMWare’s Export feature (screenshot 7)
Phase 2 : Create the secure cloud environment (AWS Cloud)
Networking requirements:
Create a network with two public subnets and two private subnets (Screenshot 8)
o Public subnets should be located in different Availability Zones (same for private subnets)
Network Access Control Lists must be used to enforce these subnet rules (Screenshot 9 and 10):
o Public subnet
Web traffic: allowed from anywhere into the public subnet
All servers are denied from sending SMTP traffic outbound
o Private subnet:
SSH/Remote Desktop traffic is only authorised to hosts in this subnet from Linux and Windows bastion hosts
all traffic is allowed between private subnet 1 and 2
General instance requirements:
All instances in a private subnet shouldn’t have a public IP address
All instances should be named descriptively, in AWS and in the Operating System
(How to rename Linux hosts: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/set-hostname.html )
Bastion Hosts (allows remote access to internal AWS network)
SSH/Remote Desktop traffic: only your IP is allowed to Linux/Windows bastion hosts
(e.g. if you are using a Swinburne PC, only that PC is allowed to connect to the bastion hosts)
Linux bastion host should use the Amazon Linux 2 AMI (t2.micro)
o Install ClamAV in command line mode (no GUI)
- Install all security updates
Windows Servers (two File servers and two Web servers)
Hosts should be based on a Windows Server 2019 Base AMI (t2.small)
o If you stop your instances, their public IPs could change (private IPs won’t) – watch for this.
For example: if you stop your bastion host and start it at home, the public IP will change
o Do not change any IP addresses for AWS resources - leave them dynamic
Only install the Windows Roles required (don’t install unnecessary roles on file/web server)
When finished creating and testing instances, go back and take several screenshots (#11-16) to show details for the instances, hostname/IPs, security groups, testing the web site/file server, etc.
Phase 3 : Preventative maintenance and troubleshooting
On the Linux and Windows bastion instances:
Check free disk space and free RAM (hint: look up df and free command in Linux) (Screenshot 17)
Perform a virus scan (screenshot 18)
- Use the Event Log or /var/log/message to record one of the warnings/errors found (screenshot 19)
Test communication by having the Linux bastion host ping Web server 1, and the Windows bastion host ping Web server 2? (screenshot 20)
Follow up questions
1. Describe the different security features, principles, and mechanisms you used to secure each layer in your cloud infrastructure:
VPC layer:
Instance layer:
OS layer:
Application layer:
2. Review this inbound Network Access Control List:
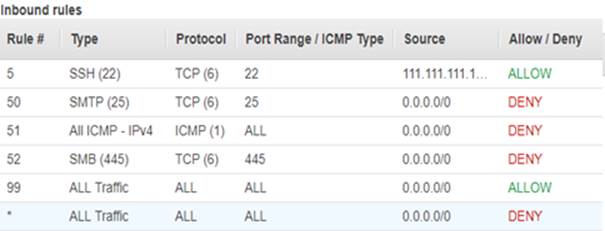
Answer the following questions:
o Can hosts in this subnet be pinged?
o Can my pc (111.111.111.111) SSH into hosts in this subnet?
o Can my laptop (2.2.2.2) SSH into hosts in this subnet?
3. This company is based 500km away from any town and no wired (fibre/cable/ADSL) infrastructure exists. What internet/NBN connection types are available to them?
4. Use the NBN address checker to identify which NBN connection technology is being implemented at 121 High street in either: Kew, Berwick, or Doncaster.


