Strategic Information Security
Organizational Background
The structure of an organization is crucial for them since it helps the organization to maintain their ethics. Here, two topics are discussed a particular organization such as security measures for the information systems and impact of organizational system change on it. The structure of an organization consists of task allocation, supervision as well as coordination which is directed towards the accomplishment of the objectives of the company. Here, a British multinational banking and financial service company are considered named Standard Chartered PLC. A banking organization is selected because security systems play a vital role in these type of organizations.
Standard Chartered
As it has been said earlier that it is a British multinational financial service and banking company. Headquarter of this organization is located in London (Standard Chartered Case Assignment, 2010). The CEO of this organization is Bill Winters who is an American banker and he is replaced by Peter Sands who was the former CEO of this bank. The company runs a more than twelve hundred branches and outlets across more than seventy countries. The employment is around eight seven thousand people all around the world. Despite the bank being located at the United Kingdom, ninety percent of the profits come from Middle East, Africa as well as Asia. Standard Chartered has a principal listing on the London Stock Exchange and is a component of the FTSE 100 Index. The company holds a market capitalization of roughly fifteen billion euro. The database is taken recently on twentieth January 2016 (AFRICA: Standard Chartered/First Africa, 2006). The band is divided into two sections like a Wholesale bank and Consumer bank. Wholesale bank services are for the global corporations, commodity traders, financial institutions and agribusiness whereas the consumer band only focus on the individuals. Consumer bank is like those normal banks. The bank provides other services such as credits cards, investment banking, wealth management and mortgage loans.
The main competitors of Standard Chartered Bank are ABN AMRO, Barclays Bank, RBS, JP Morgan and Chase, BNP Paribas, HSBC and so on. According to the latest research, Standard Chartered faced some serious issues and challenges which is a risk for the organization. The economy of the bank faced a downturn in most of the Asian countries (Suttle, 2010). The loss on bad loans almost doubled to four billion dollars with the regulatory cost increased by forty pieces to one billion dollars. Apart from recent news, the bank provides the customers with online facilities. Customers can transact money or do any type of operations from home by means of online banking.
Time Management Plan
Research Paper 1:
Generally, the hackers are the main problems of a bank. That is why strong security systems are installed in international based banks. One of the most commonly used security systems that Standard Chartered uses to protect hacking of accounts is online and mobile security (Amato et al., 2014). However, the organization also make use of CCTV cameras and security guards inside the bank premises from dangers of theft. Since the hackers are increased and the process of stealing money from the bank by the thieves was decreased, so Standard Chartered uses Information Security System to protect classified data and information from the hands of hackers. The information security management system or the ISMS is a set of policies related to the management of information security of a bank or IT-related threats.
The bank still needs some improvement for the development of security systems. The regulators of this organization need more Information Technology professionals so that the customers, as well as other bank members, can be well protected under latest technologies (Norman, 2007). It is easy for the hackers to hack security passwords such as numbers, letters or alphabets but if the IT specialists of the bank create passwords such as face recognition, fingerprint or voice recognition security system then they can make a strong security system. The hackers will dare to hack the system.
Research Paper 2:
The table below demonstrates a plan which will be used for the development of security systems of Standard Chartered.
Security Plans vs Time Management | Month 1 | Month 2 | Month 3 | Month 4 |
Plan 1 (Week 1) | Appointing a security officer. | Installing CCTV cameras. | Appointing anti-hacker professionals. | Installing new technology system inside the bank premises. |
Plan 2 (Week 2) | Assembling the security awareness team. | Determining the roles and responsibilities of the security awareness team. | Spreading security awareness throughout the organization by means of 5 days awareness session. | Making a security awareness program record. |
Plan 3 (Week 3) | Providing basic level physical training to all employees of the organization. | Providing intermediate level physical training to all the employees. | Providing expert level physical training to all the employees to defend from the robbery. |
Taking a physical examination of all the employees to determine how they have improved in defending themselves. |
|
Plan 4 (Week 4) | Installing and maintaining a firewall configuration for the protection of cardholder data. |
Telling the customers to install personal firewall software on mobile to protect their bank accounts from hackers when they use internet on streets. |
Maintaining a vulnerability management program which includes protection of all systems against malware. |
Implementing strong access control measures. It identifies and confirms access to components of the system. |
The time management plan based on the development of security system of the organization is a four-month plan. Each month has four plans per week.
Research Paper 3:
In this section, risk management, protection mechanisms, law and ethics as well as personnel and security are being discussed along with the necessary guidelines for the implementation. One of the best risk management procedure is machine learning which improves the accuracy of risk models by the identification of nonlinear or complex patterns in large data sets (Holmes, 2002). Based on protection mechanisms, banks use face recognition or fingerprint facilities which protects the accounts of the consumers from frauds. On the other hand, the bank has developed policies and procedures in order to help their consumers to reach the highest social and environmental standards. The standards and policies include anti-bribery and corruption policy, code of conduct, defense goods policy summary, HIV and AIDs policy speaking up policy, health and safety policy, anti-money laundering policy and equal opportunity, diversity and dignity policy.
The bank can make use of PRT Network Monitor. It is a network monitor for the specialist and it can be installed in two minutes. The most attractive feature of this product that it alerts before any emergencies occur. It also automatically discovers the network. The product fits into any budged and grows according to the needs of the bank. It detects who is using the network of the organization.
Work Breakdown Structure
The work breakdown Structure or WBS in banking based organizations is a deliverable arrange breakdown of a project into little components. The elements of a work breakdown structure may vary from product to data and service or any type of combinations. It also provides the required framework for estimating and controlling a detailed cost along with the guidance for a schedule control and development plan. The shape of a work breakdown structure looks like a tree which shows subdivisions of effort needed for achieving the objectives of an organization. The work breakdown structure of Standard Chartered is described below:
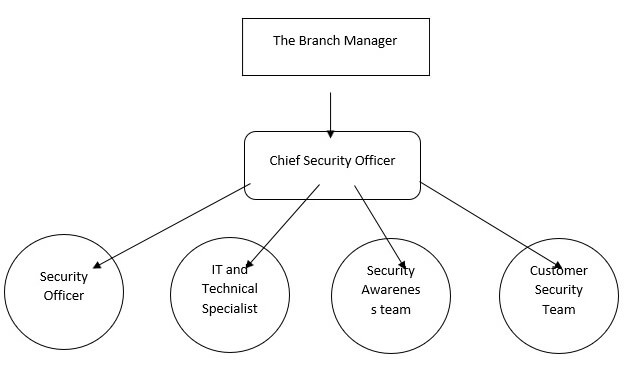
The above figure represents a work breakdown structure of the security department of an organization. Based on the above figure, like every bank, Standard Chartered also has branch manager (Integrating Process and Work Breakdown Structure with Design Structure Matrix, 2010). Under the branch manager head of the security department works and under the chief security officer, security officers, IT and technical specialist, security awareness team as well as customer security team works. Everyone has its own job.
Chief Security Officer
The chief security officer is the highest level executive who is directly responsible for the entire security function of an organization. The chief security officer is also responsible for the physical security requirements of the employees working in that particular company. He helps to force strong as well as secure connections between the departments.
Security Officer
The security officer has the most important role to play in a bank. The primary role of a security officer is to prevent crime inside bank premises. The presence of a security officer on the bank premises serves as a warning to the potential lawbreakers. The security officer also patrols throughout the corners of the bank premise and keep keen observation about any type of law-breaking actions.
IT and Technical Specialist
The fundamental role of IT and technical specialist is creating strong security system within the computer systems so that no hackers dare to hack and enter the system. They often act as an anti-hacker specialist and hack into the system of the hacker to locate the area of the hacker so that they can easily send a police force to that particular area to arrest the hacking team.
Security Awareness team
It is important to spread security awareness to each and every ear of the clients as well as employees. Therefore, security awareness team is responsible for that. The team spreads security awareness by means of leaflets or by announcing. They also recommend the clients about the do’s and don’ts of a security system.
Customer Security Team
The customer security team deals with security-related issues of the customer such as internet banking or SMS banking. Sometimes passwords of the customers get hacked. At that time customer security team look after that matter. If the hacker is strong, then the job is transferred to the IT and technical department where the anti-hacker specialist hacks the location of the cyber-criminal.
Task-Sequencing Approaches
Gantt chart:
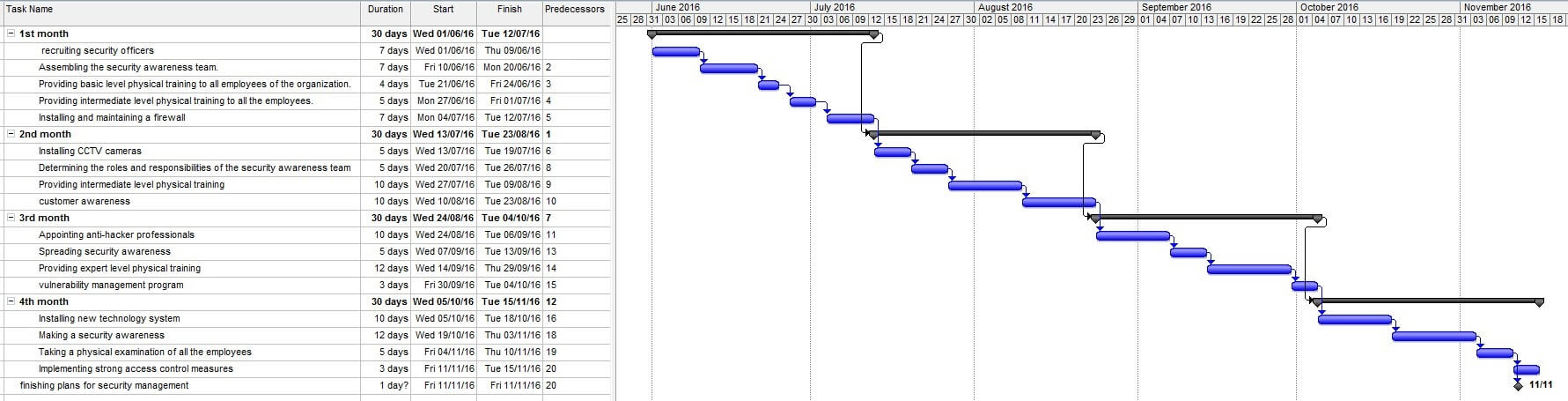
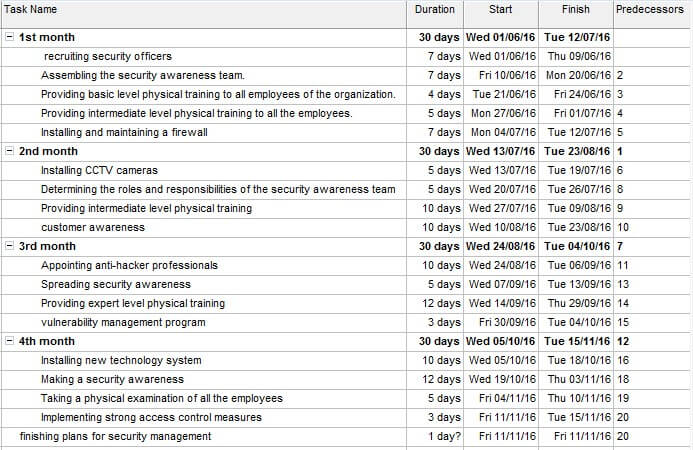
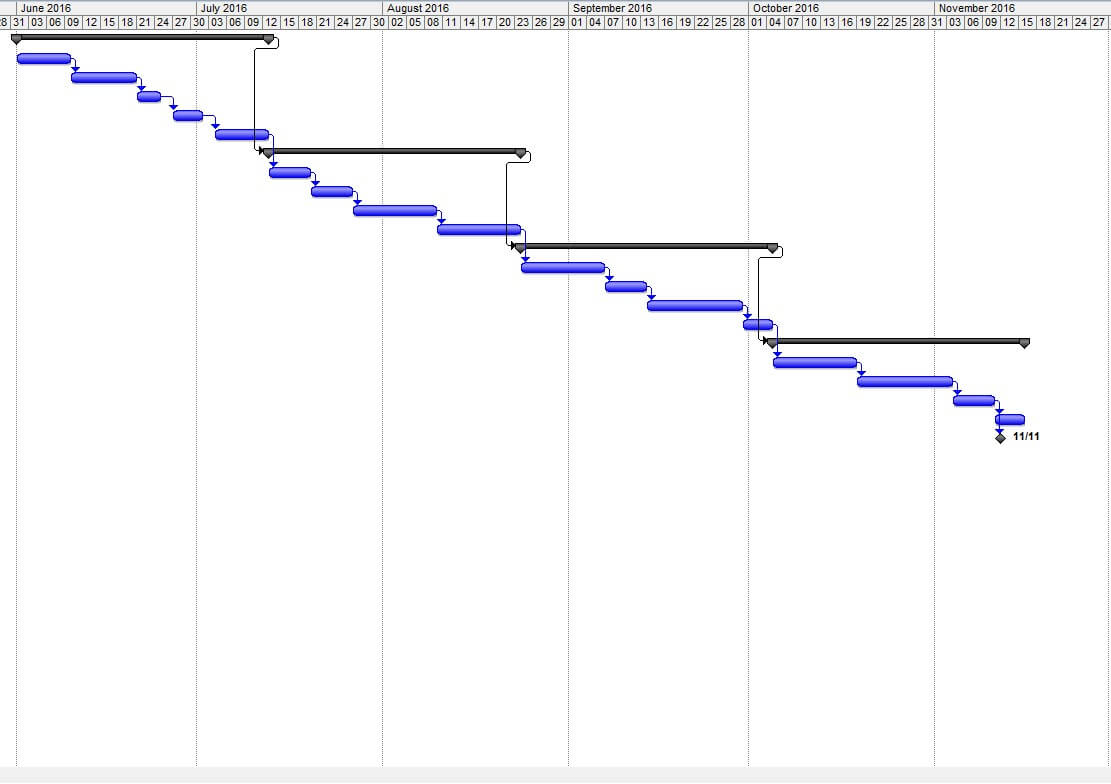
The above Gantt chart is the project plan and it’s planning procedure for four months.
References
AFRICA: Standard Chartered/First Africa. (2006). Africa Research Bulletin: Economic, Financial and Technical Series, 43(6), pp.17010A-17010B.
Amato, C., Pierro, A., Chirumbolo, A. and Pica, G. (2014). Regulatory modes and time management: How locomotors and assessors plan and perceive time. Int J Psychol, p.n/a-n/a.
Holmes, A. (2002). Risk management. Oxford, U.K.: Capstone Pub.
Integrating Process and Work Breakdown Structure with Design Structure Matrix. (2010). JACIII, 14(5), pp.512-522.
Norman, T. (2007). Integrated security systems design. Amsterdam: Elsevier Butterworth-Heinemann.
Standard Chartered Case Assignment. (2010). [Place of publication not identified]: Datamonitor Plc.
Suttle, P. (2010). Interim Report on the cumulative impact on the global economy of proposed changes in the banking regulatory framework. [Washington, D.C.]: Institute of International Finance.


