Securing system using IPTable firewall
Question
You are required to set up, configure, and test your firewall. You need to do research and reading to be able to complete this assignment.
You have to discuss the main use, limitations, and possible security holes of your firewall and write it in your report. You should test that following packages are installed on your machines: SSH and Webserver. Start the services and ensure that they are available for you to do experiment with IPTable Firewall. You should include screen shots in your answers to show the output of your results.
Important:
You need to save copies of all different configurations (for each part) that you have done. (You should include your firewall rules and the results (screen shots) in the report)
Configure your firewall to:
- Reject all Telnet packets.
- Allow Telnet remote connections.
- Deny ping.
- Reject all traffic coming to MySQL server.
- Block incoming traffic connection to your IP address of your virtual machine.
- Allow traffic coming to port 80 (inbound) but reject traffic going out (outbound) through port 80.
You then have to:
- a. discuss the advantages and disadvantages of firewalls with iptables and make suggestions to overcome the disadvantages in your report.
Submission
Scoring
You should submit your report on the Moodle. The length of the report should be no longer than 10 pages.
Question | Score | Description |
Content | ||
1 Denial of Telnet access | 5 | Show that Telnet packets are rejected |
2 Access of Telnet service | 5 | Show that Telnet packets are accepted |
3 Ping service denial | 5 | Deny ping |
4 Traffic to MySql | 10 | Show all traffic coming to MySql is rejected |
5 IP address access control | 10 | Demonstration of Blocking traffic connection to your IP address of your virtual machine |
6 Port 80 one way traffic | 10 |
Show that traffic coming to port 80 is allowed but rejected going out through port 80 |
Subtotal: | 45 | Subtotal for content |
Presentation | ||
Experiment setup in Kali | 15 | Report should show the details how you have tested in parts: 1,2,3,4,5,6 with real practical tests and/or with your gathered information |
IPTable advantages and disadvantages | 15 | Include advantages and disadvantages of firewalls with iptables and make suggestions to overcome the disadvantages in your report |
Report is comprehensive | 15 | Does report reflects understanding about the use of IPtables firewall |
Spelling, Grammar, Presentation, Style References | 10 | The report’s contents are appropriately written in English, with no spelling errors and grammar issues. The report is well presented, with diagrams, headings, tables and other visual aids. The report contains appropriate references and referencing style. |
Subtotal: | 55 | Subtotal for presentation |
Total: |
100 | |
Answer
What is Firewall and its use?
A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules.
A firewall can be hardware, software, or both.
A firewall is a crucial component of securing your network and is designed to address the issues of data integrity or traffic authentication (via stateful packet inspection) and confidentiality of your internal network (via NAT). Your network gains these benefits from a firewall by receiving all transmitted traffic through the firewall. Your network gains these benefits from a firewall by receiving all transmitted traffic through the firewall. The importance of including a firewall in your security strategy is apparent; however, firewalls do have the following limitations:
- A firewall cannot prevent users or attackers with modems from dialing in to or out of the internal network, thus bypassing the firewall and its protection completely.
- Firewalls cannot enforce your password policy or prevent misuse of passwords. Your password policy is crucial in this area because it outlines acceptable conduct and sets the ramifications of noncompliance.
- Firewalls are ineffective against nontechnical security risks such as social engineering, as discussed in Chapter 1, “There Be Hackers Here.”
- Firewalls cannot stop internal users from accessing websites with malicious code, making user education critical.
- Firewalls cannot protect you from poor decisions.
- Firewalls cannot protect you when your security policy is too lax.
Possible security holes for a firewall –
Here are some common firewall vulnerabilities that need to be on the lookout for listed in order of typical significance/priority:
- Password(s) are set to the default which creates every security problem imaginable, including accountability issues when network events occur.
- Anyone on the Internet can access Microsoft SQL Server databases hosted internally which can lead to internal database access, especially when SQL Server has the default credentials or an otherwise weak password.
- Firewall OS software is outdated and no longer supported which can facilitate known exploits including remote code execution and denial of service attacks and might not look good in the eyes of third-parties if a breach occurs and it’s made known that the system was outdated.
- Anyone on the Internet can access the firewall via unencrypted HTTP connections, as these can be exploited by an outsider who’s on the same network segment such as an open/unencrypted wireless network.
- Anti-spoofing controls are not enabled on the external interface which can facilitate denial of service and related attacks.
- Rules exist without logging which can be especially problematic for critical systems/services.
- Any protocol/service can connect between internal network segments which can lead to internal breaches and compliance violations, especially as it relates to PCI DSS cardholder data environments.
- Anyone on the internal network can access the firewall via unencrypted telnet connections. These connections can be exploited by an internal user (or malware) if ARP poisoning is enabled via a tool such as the free password recovery program.
- Any type of TCP or UDP service can exit the network which can enable the spreading of malware and spam and lead to acceptable usage and related policy violations.
- Rules exist without any documentation which can create security management issues, especially when firewall admins leave the organization abruptly.
{`
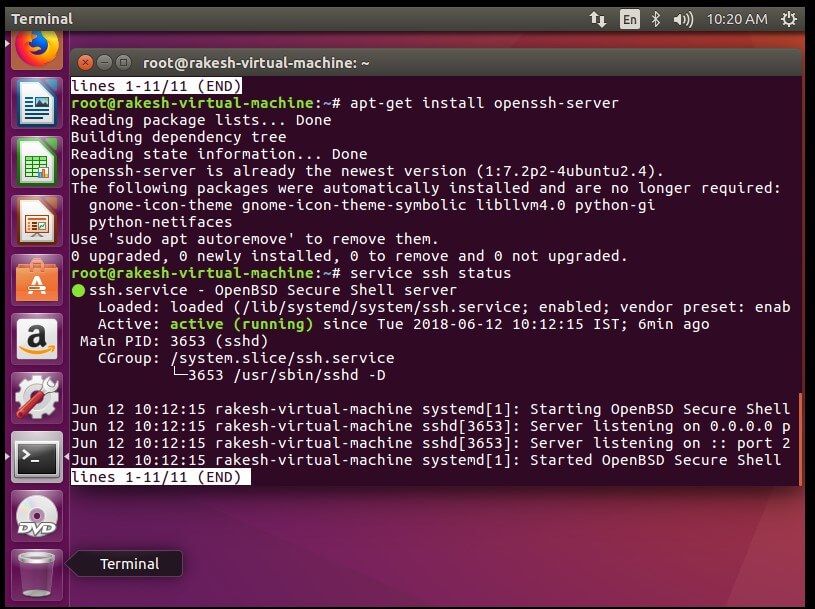
Installing SSH server –
Install ssh-server followed by this command:
#sudo apt-get install OpenSSH-server
Check the service is install and running properly:
#sudo service ssh status
`}
{`
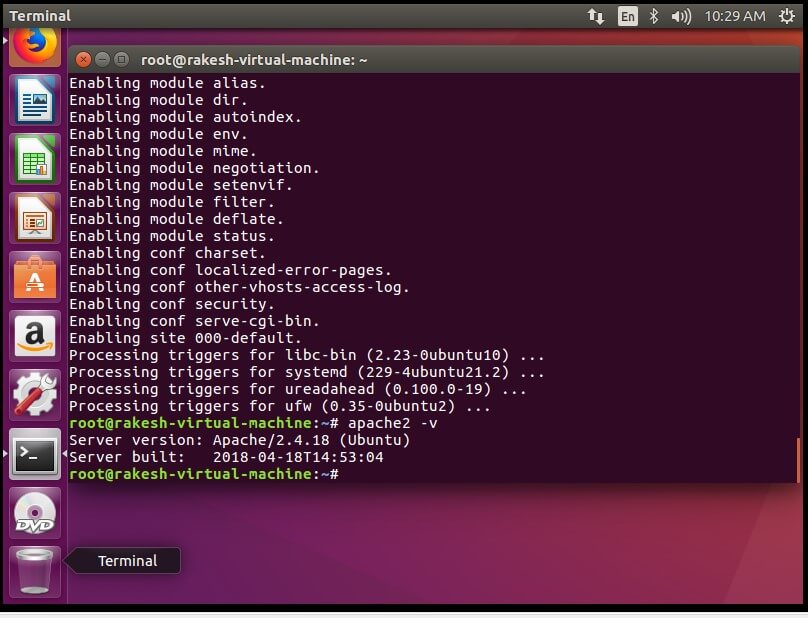
Installing Web-server (Apache) –
Install Apache server followed by this command :
#sudo apt-get install apache2
To check the installation and package run the command :
#apache2 -v
`}
{`
Start and Enable the Apache service –
#sudo systemctl start apache2.service
#sudo systemctl enable apache2.service
Installing (Firewall) IPTables persistent –
Installing an IP-Table firewall by following commands –
#sudo apt-get install iptables-persistent
`}
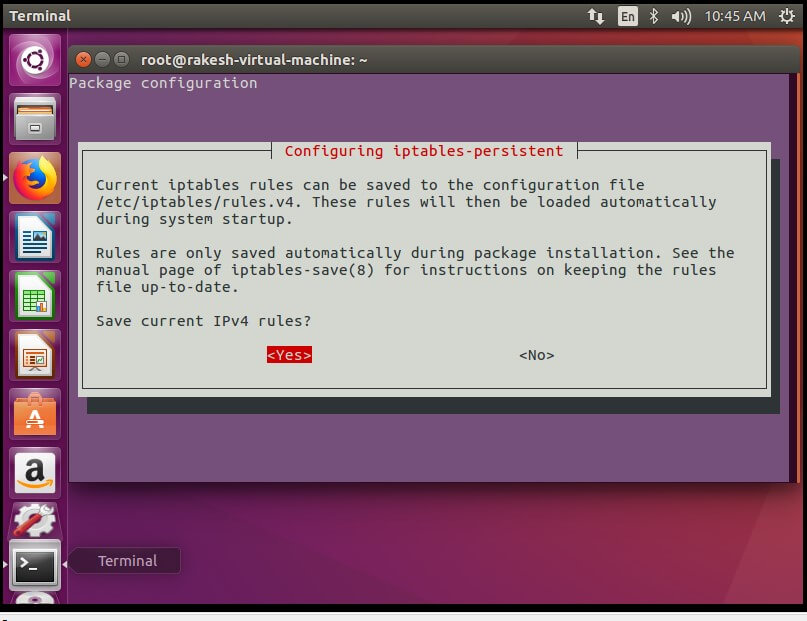
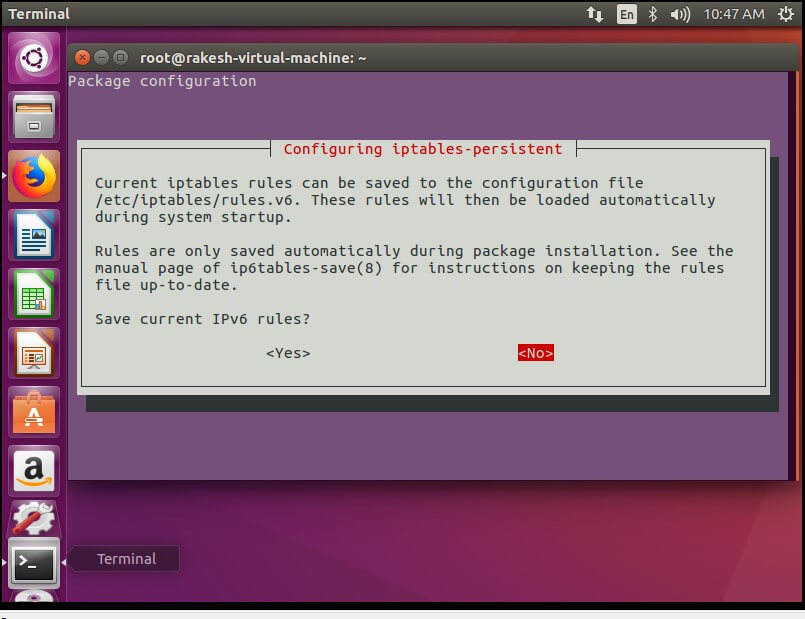
{`Here select IPv4 to < Yes >`}
{`
Select <No> to IPv6.
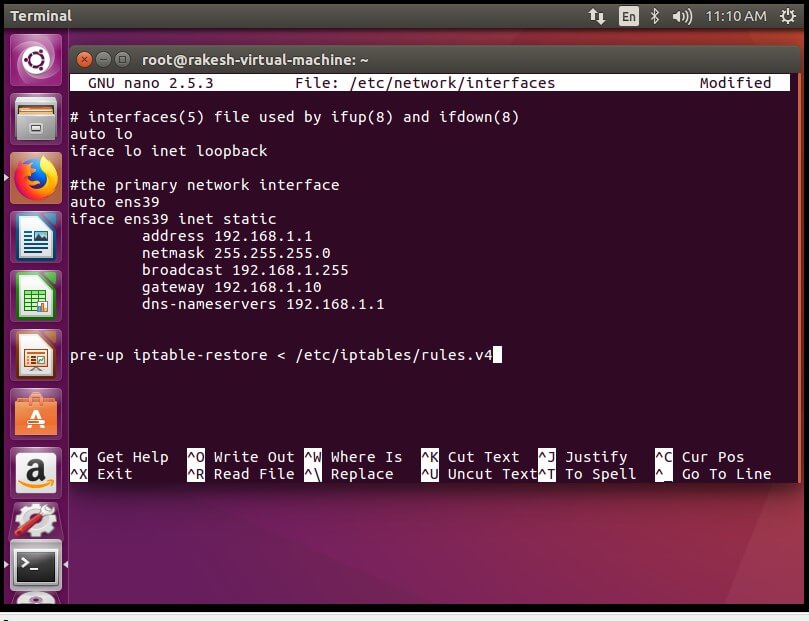
It will install the Firewall. Now make a static IP address and interface Id (ens39) entry in /etc/network/interfaces file. And to add any rules permanent to the IPTable, add the following line to the end of this file –
pre-up iptables-restore < /etc/iptables/rules.v4
Editing the interface file –
#sudo nano /etc/network/interfaces
`}
{`
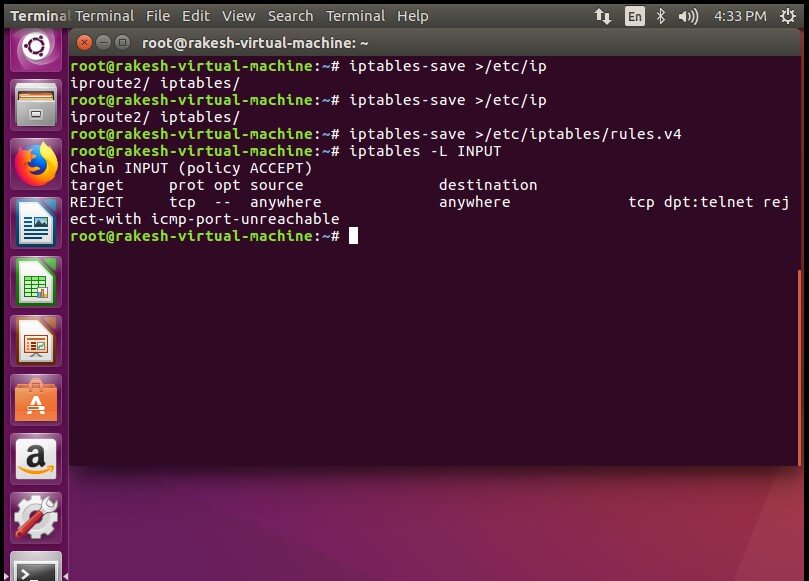
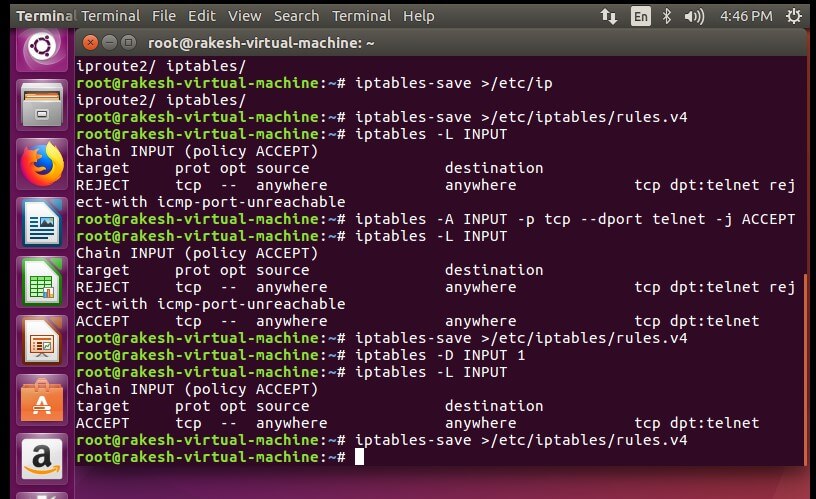
Rejecting all Telnet connection –
# sudo iptables -A INPUT -p tcp -dport telnet -j REJECT
`}
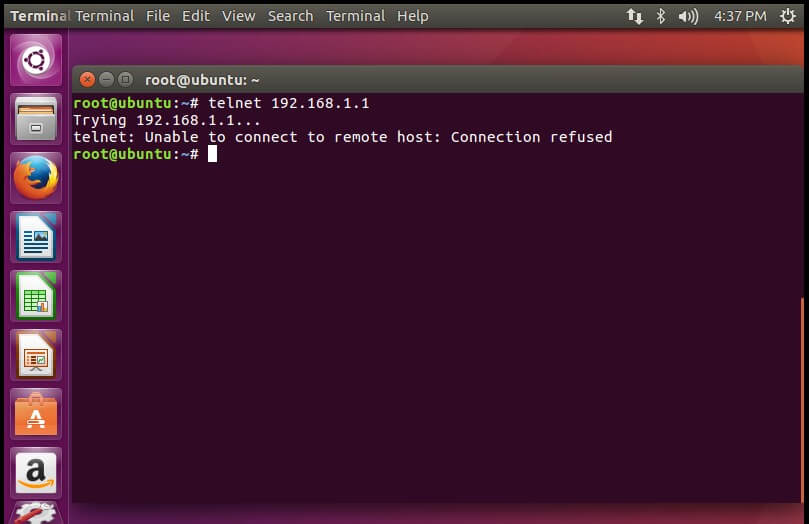
{`After adding rule a client is trying to connect and getting connection refuse massage– `}
{`
Allowing Telnet Remote Connect –
# sudo iptables -A INPUT -p tcp -dport telnet -j ACCEPT
`}
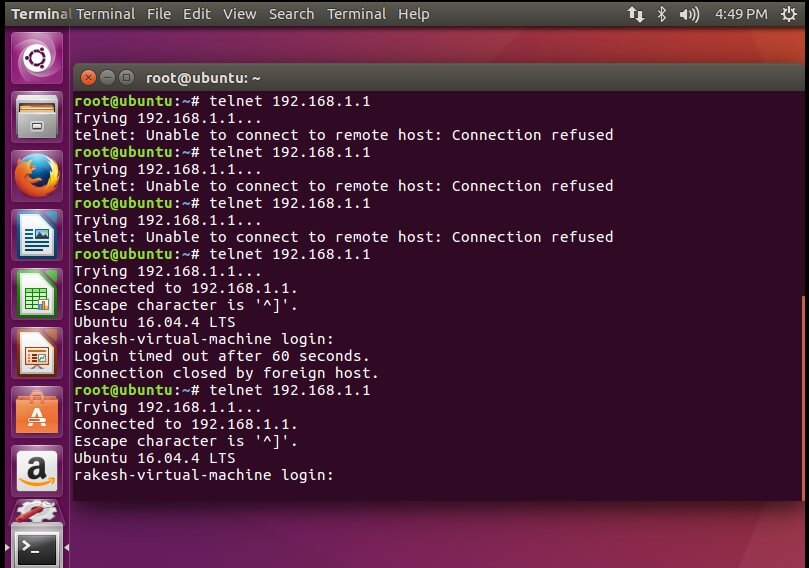
{`After allowing, host is able to connect with telnet connection –`}
{`
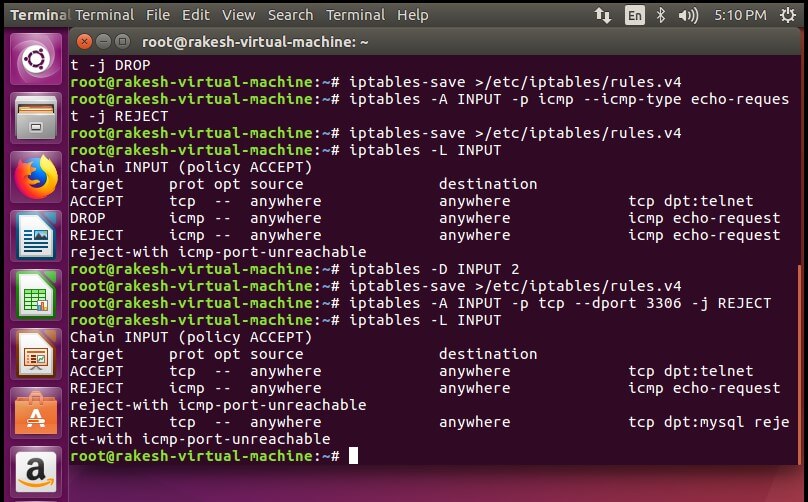
Deny ping –
#sudo iptables -A INPUT -p icmp –icmp-type echo-request -j REJECT
`}

{`
Reject all traffic coming to MySQL server –
#sudo iptables -A INPUT -p tcp –dport 3306 -j REJECT
`}
{`
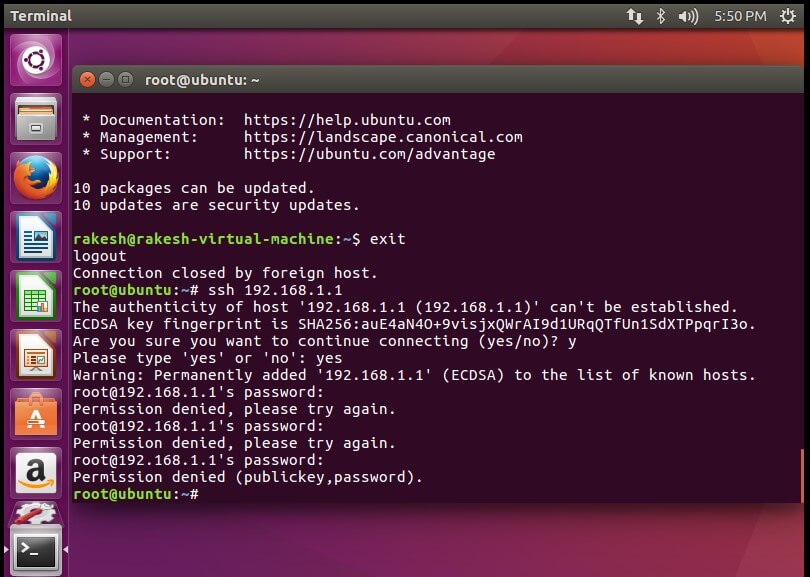
Block incoming traffic connection to your IP address of your virtual machine –
#sudo iptables -A INPUT -i ens33 -s 192.168.1.1 -j REJECT
`}
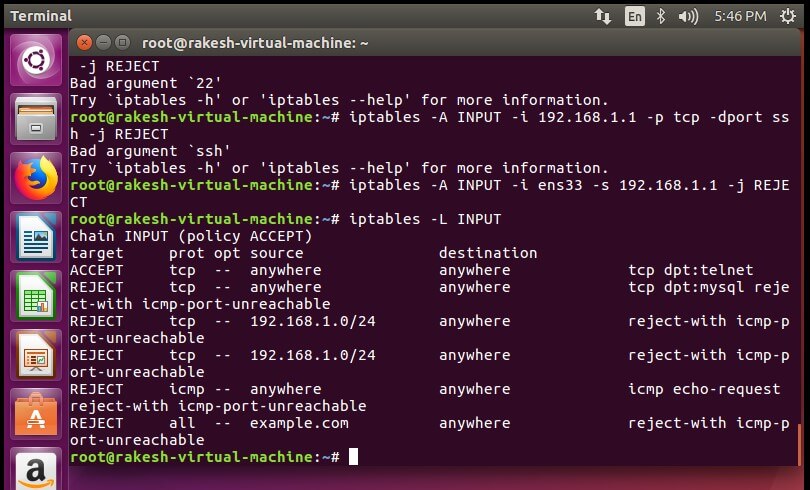
{`After that SSH is denied –`}
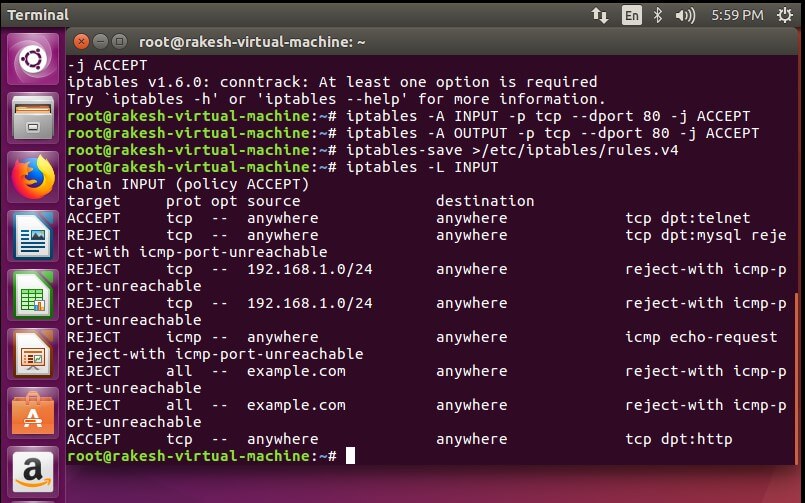
{`
Allow traffic coming to port 80 (inbound) but reject traffic going out (outbound) through port 80 –
#sudo iptables -A INPUT -p tcp -dport 80 -j ACCEPT
#sudo iptables -A OUTPUT -p tcp -dport 80 -j ACCEPT
`}