Dress2Go E-Commerce Website
Dress2Go Ecommerce Website
Task 1
Analyzed Websites are:
|
Website |
Screenshot |
Analysis Remark |
|
Amazon |
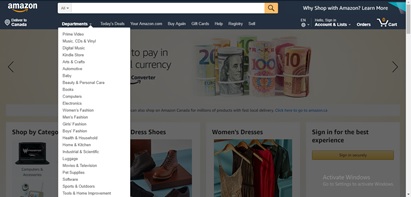
|
The categories are grouped under one navigation section. This is a major take-away from this website. |
|
The Iconic |
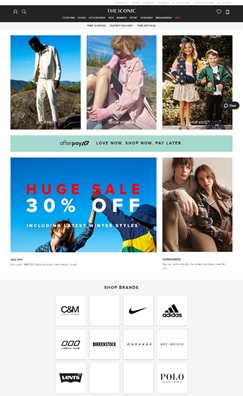
|
The major items of the website are exhibited on the home page, alongside discount offers. This enhances the business opportunities. |
|
Shop.Guess |
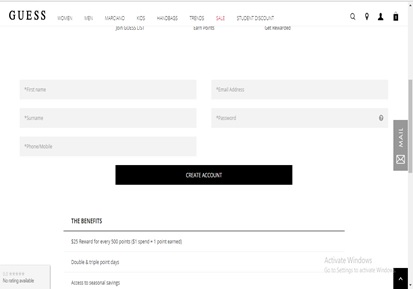
|
The basic details that are required to be taken as input from the customers in order for them to register can be the main lesson from this website. They kept it simple. |
|
Driza Bone |
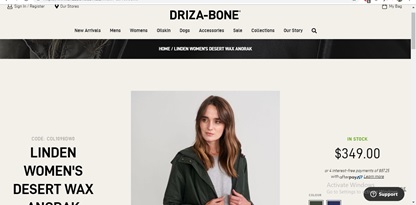
|
The product description are beautifully laid out in a tabular manner, side by side. |
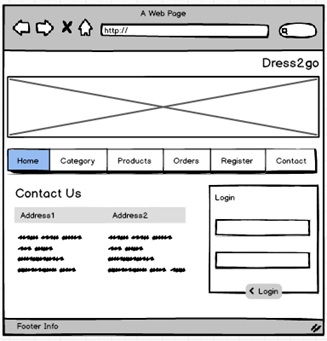
1.1 Interface Design
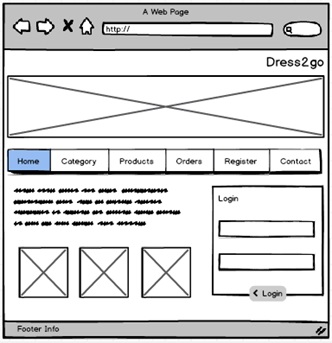
Home Page
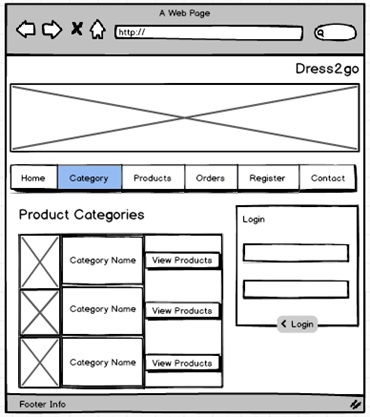
Category Page
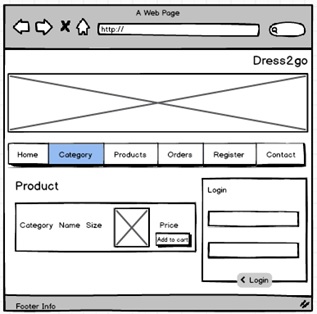
Product Page
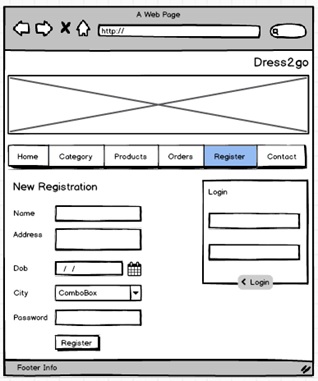
New User Registration
Contact Page
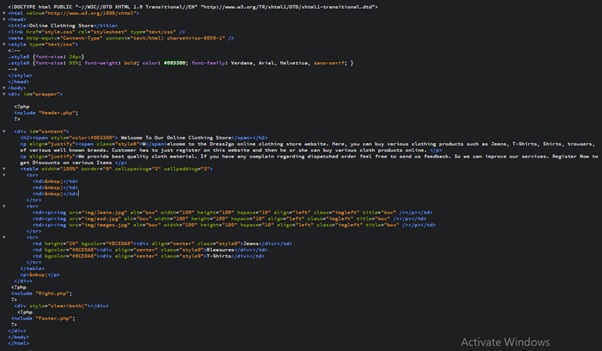
1.2 Scripting and Markup languages
HTML and CSS are utilized for site structure creation and designing. JavaScript is the client-side scripting language that is used for web rendering of real programming code and logic, intended to compose applets for use on the site. JavaScript is utilized to change the conduct and dynamic components of the site. HTML5 is utilized to plan content and henceforth organize the elements on the web, that it very well may be shown on an internet browser. HTML is the markup language that characterizes the structure of a page. JavaScript is a programming language utilized on client side. jQuery was also used in this project. It is a basic JavaScript library that could be useful to accelerate improvement. The use of CSS or Cascading Stylesheets assists in the process of designing the web layout with backgrounds, colors, margins and so on.
In the similar way that the web associates us, there are unique web dialects that stir together to make up the web and the sites it contains. HTML, CSS and JavaScript cooperate to shape the front-end designing of a site by applying code that influences components, style and logic of a site.
PHP has been used as the server-side scripting language to connect the website with the MySQL database. This makes the website even more dynamic. The main purpose of PHP are:
- PHP generates dynamic page content
- It assists in database connectivity.
- Allows to work on the database, by adding, modifying and deleting database contents.
- It helps to create and maintain site cookies.
- It helps to control user access.
- It encrypts sensitive data whenever required for security purposes.
Task 2
2.1 Development
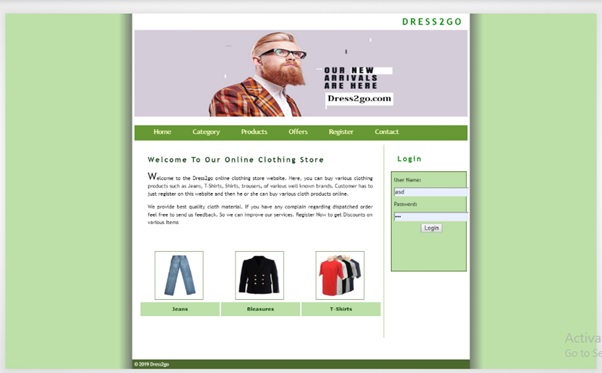
Home Page (index.php)
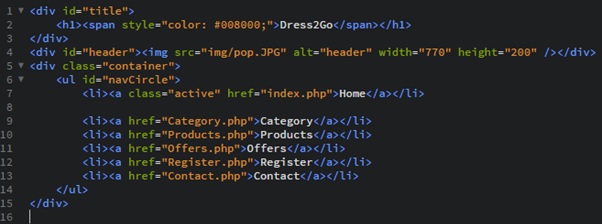
Navigation Menu (header.php)
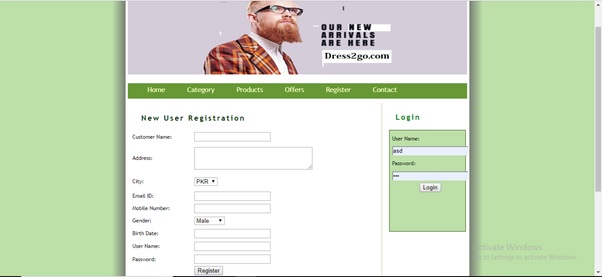
Login
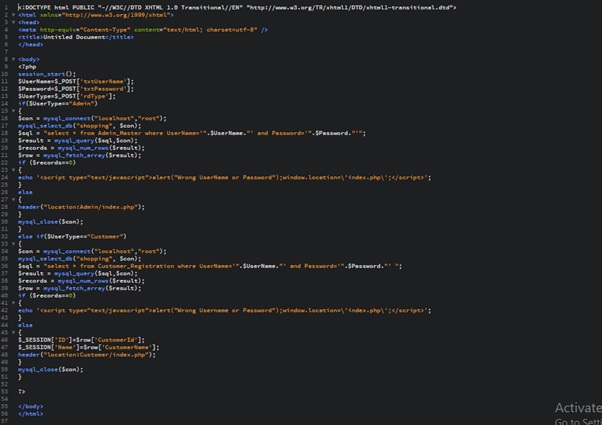

Register User (register.php)
And so on…
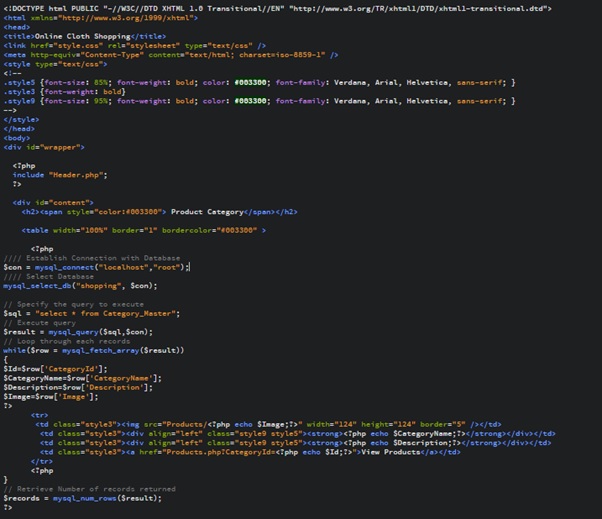
Categories (Category.php)

Products Description
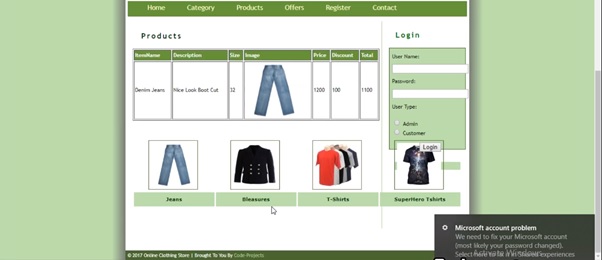
Contact
Task 3
3.1 Web Hosting Server
Godaddy.com can be used for the purpose of hosting the website and getting a domain for the Dress2go website.
The bandwidth requirement for the initial stages of the website’s launch should be somewhere around 4GB.
An initial storage capacity of 512 GB will help in the process of launching the website. This will not only allow to store the necessary elements for the system but will also allow in the robust and hassle-free execution of the website.
The need for a domain mail is also very crucial, such that the customers can write mail to the company domain directly.
3.2 Server Security
The following steps should be taken care of the security of the files and data that is uploaded on the server:
- SSH Authentication: SSH keys are sets of cryptographic keys, which are used to confirm to a SSH server as an option in contrast to the general secret key-based logins. A private and open key pair are generated preceding the validation phase. While the private key is held onto by the client, the open key is imparted to the other users who plan on accessing the system.
- Firewalls: This is a software tool, which controls the general administrator rights of the system. This makes sure that all sorts of external access to the system without the proper privileges are blocked out. This will help in keeping the Dress2go website safe from eligible hackers and improper access.
Server backups are necessary. A backup server empowers the backup of data, information, documents, applications and potentially databases on a represented considerable authority in an in-house or remotely hosted server. It consolidates equipment and programming advancements, which give backup and other recovery administrations to associated computers, related gadgets and or servers. The following will be followed in order to back up the site in consideration:
- A full back-up stores a duplicate copies of files and data as per the scheduled timings. Records are typically compressed to spare space, be that as it may, notwithstanding when packed full backups may devour a great deal of capacity.
- Incremental Backups are a smarter way to utilize the prospects of the back-up system. This assists the system by taking iterative backups after specific intervals. This ensures that only the updated states of the system are backed-up, hence saving up on backup storage space and time.
Bibliography
Bergsma, F., Dowling, B., Kohlar, F., Schwenk, J. and Stebila, D., 2014, November. Multi-ciphersuite security of the Secure Shell (SSH) protocol. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security (pp. 369-381). ACM.
Nafi, K.W., Kar, T.S., Hoque, S.A. and Hashem, M.M.A., 2013. A newer user authentication, file encryption and distributed server based cloud computing security architecture. arXiv preprint arXiv:1303.0598.
Olsson, M., 2013. Using PHP. In PHP Quick Scripting Reference (pp. 1-4). Apress, Berkeley, CA.
Suehring, S. and Valade, J., 2013. PHP, MySQL, JavaScript & HTML5 all-in-one for dummies. John Wiley & Sons.
Suguna, S. and Suhasini, A., 2014, February. Overview of data backup and disaster recovery in cloud. In International Conference on Information Communication and Embedded Systems (ICICES2014) (pp. 1-7). IEEE.


