World economic forum security related risks
| TLP WHITE |  |
|
|---|---|---|
 |
 |
Cyber-security risks in the
supply chain
For any modern organisation, physical supply chain management already presents numerous complex challenges in understanding exposure to risk. The added complexity of cyber-security risks only amplifies this, regardless of their position within a supply chain. This paper provides an introduction to cyber-security risks within the supply chain, drawing on recent examples to highlight the benefits of an inclusive approach. It concludes with non-technical mitigation advice and points the reader to international standards for information security and management.
Intentional targeting and collateral damage
| TLP WHITE strong cyber-security measures it has implemented through its ICT system, it has fallen victim |
|---|
to deliberate targeting or collateral damage.
The weakest link
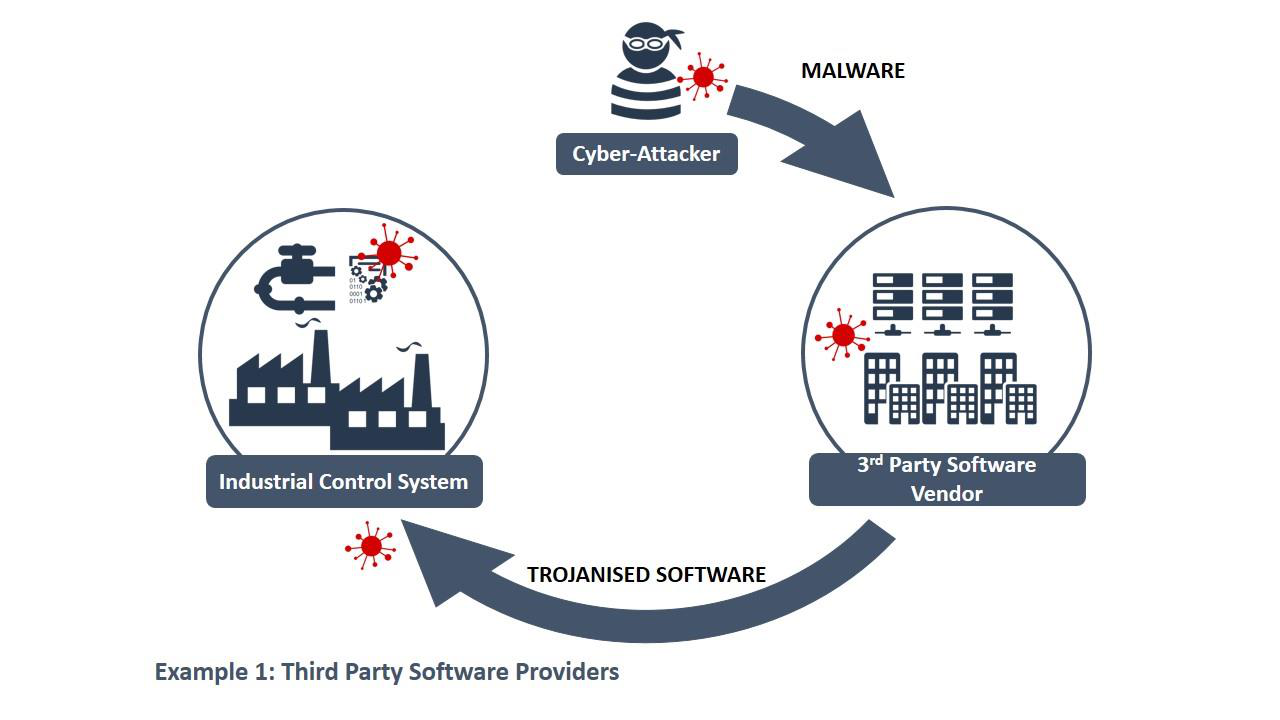
Identified in mid-2014, the cyber-espionage group known as Dragonfly (also known as Energetic Bear, Havex, and Crouching Yeti) has allegedly been targeting companies across Europe and North America, mainly in the energy sector, since 2011. There is some speculation that pharmaceutical producers were the true target.5 This group has a history of targeting companies through their supply chains, and in the latest campaign, Dragonfly was able to “trojanise” legitimate industrial control system (ICS) software. They were able to compromise the websites of the ICS software suppliers and replace legitimate files in their repositories with those that had malware added to them. The ICS software could then be downloaded from the suppliers’ websites and install the malware alongside the ICS software. The malware included additional remote access functionalities that could be utilised to take control of the systems where it was installed. Compromised software is very difficult to detect if it has been altered at the source, and so there is no reason for the target company to suspect it was not legitimate. This places great reliance on the supplier, as it is not feasible to inspect every piece of hardware or software in the amount of depth required to discover this type of attack.
 |
|---|
As well as cyber-espionage groups looking for commercially sensitive information, intellectual property, and critical vulnerabilities, cyber-criminals target supply chains as a means of targeting the broadest audience for their malware as possible. Identifying and compromising one strategically important element is an efficient use of resources and may result in a significant number of infections.
The Shylock banking Trojan is as a good example of this. Predominately focused on e-banking in the UK, Italy and the USA, those behind Shylock were disrupted and the threat from it reduced in July 2014 in a joint operation by law enforcement agencies and the cyber-security community.6 The Shylock attackers compromised legitimate websites through website builders used by creative and digital agencies and employed a redirect script sending victims to a malicious domain owned by the Shylock authors. From there, the Shylock malware was downloaded and installed onto the systems of those browsing the legitimate websites. The economy of effort makes this a very successful endeavour. By integrating a multitude of different features adopted from other malware, Shylock was capable of performing customisable ‘man-in-the-browser’ attacks, avoiding detection and protecting itself from analysis.7 Rather than compromising a number of legitimate sites individually, the attack
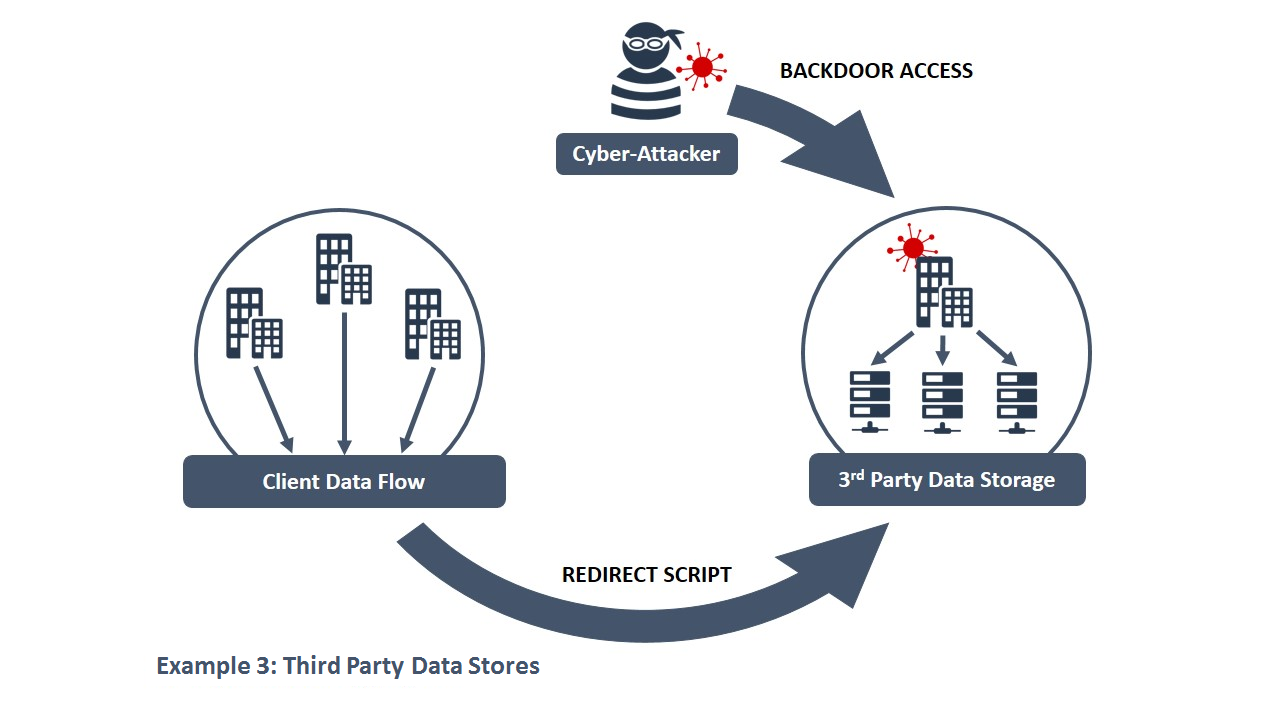
Many modern businesses outsource their data to third party companies which aggregate, store, process, and broker the information, sometimes on behalf of clients in direct competition. Such sensitive data is not necessarily just about customers, but could also cover business structure, financial health, strategy, and exposure to risk. In the past, firms dealing with high profile mergers and acquisitions have been targeted.8 In September 2013, a number of networks belonging to large data aggregators were reported as having been compromised. A small botnet was observed exfiltrating information through an encrypted channel from the internal systems to a botnet controller on the public Internet.9
| TLP WHITE compromise enables attackers to access valuable information stored via a third party and |
|---|
Example 4: Watering hole attacks
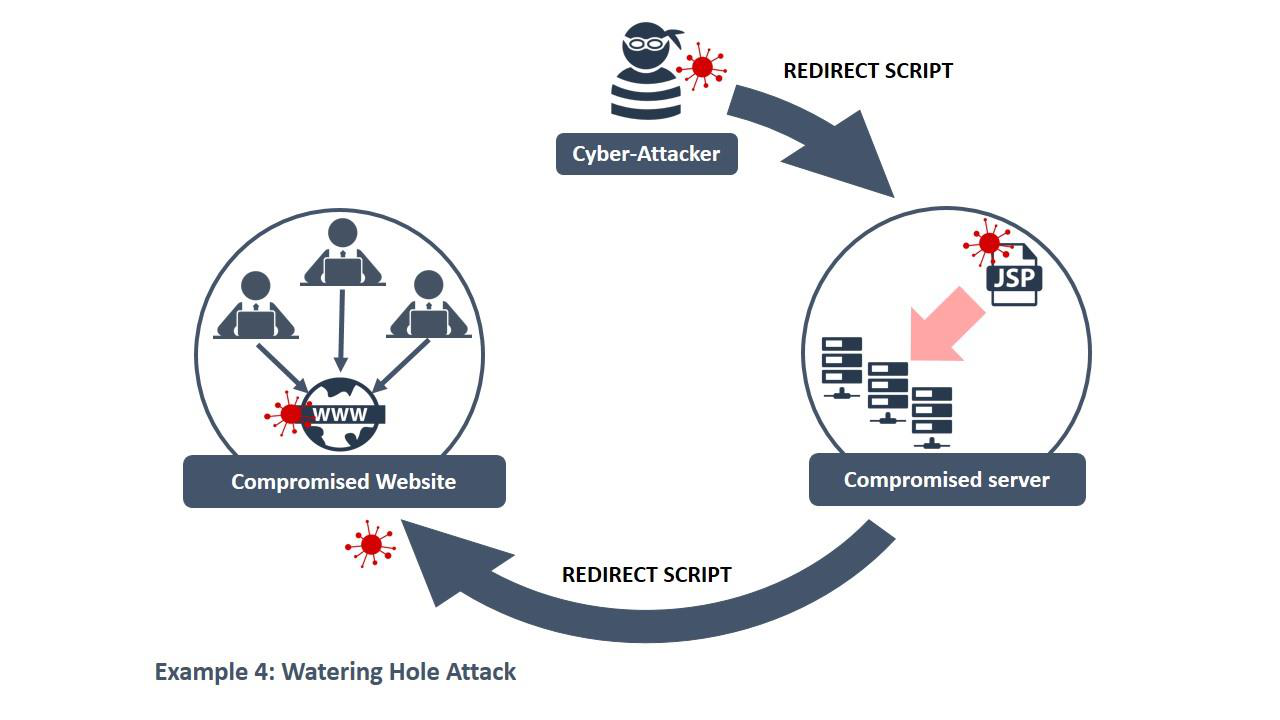
victims. Specifically targeted were the websites of a regional bank and a local government, along with websites relating to geopolitics, defence industry and education. Once these sites were accessed, the victims’ systems downloaded the malware which consisted of a RAT that would allow extensive control of the system. Victims included education institutions, defence and technology sector organisations, internet service providers, health sector organisations, utility sector organisations, and state and federal government networks.12
Mitigation advice
| TLP WHITE For small and medium sized organizations that are disproportionately exposed to cyber- |
|---|
security related risks, obtaining Cyber Essentials accreditation will contribute to their reputation as a well-defended partner in a supply chain16 and will provide a solid baseline to improve upon. For large enterprises, the 20 security controls17 combined with independent threat assessments will help identify cyber-security related risks to supply chains that provide demonstrable assurance of the processes and procedures of member organisations.18 Ideally this would be coupled with technological platforms that allow estate monitoring and the intake of threat intelligence. This will not only improve an organisation’s own supply chain risk management but also share threat intelligence with other organisations in the supply chain for a coordinated response. It is also important to get the basics right:
risks can be used throughout the supply chain.
It may seem a trivial point, but by implementing a common language with other members within its supply chain, an organisation can more easily anticipate, identify, communicate, and ultimately mitigate the risk posed by cyber-security related dependencies and vulnerabilities. The ISO standards are a framework for good security practice and, as such, are foundational. Once the standard is in place, it needs to be audited, maintained and then further technological and procedural steps taken to harden the environment often utilising perimeter defence technologies and logging and monitoring technologies such as security information and event management (SIEM). The importance here is not advocating the accreditation to international standards as these services can be commercially costly and as such can rule out their use in certain organisations. However, the importance is in their use by all firms in the same line of business: if the supplier and the supplied are both utilising and/or certified to the standard(s), then they share a common understanding of risk, information security and have a baseline set of measures in place that allows them to deal with the threat. Therefore, if both the supplier and supplied have a baseline level of security they are more resilient to the threat.
A CERT-UK PUBLICATION
COPYRIGHT 2015 ©