Well investigate the secure sockets layer ssl protocol
Wireshark Lab: SSL v8.0 |
 |
In this lab, we’ll investigate the Secure Sockets Layer (SSL) protocol, focusing on the SSL records sent over a TCP connection. We’ll do so by analyzing a trace of the SSL records sent between your host and an e-commerce server. We’ll investigate the various SSL record types as well as the fields in the SSL messages. You may want to review Section 8.6 in the text1. We are currently developing a Wireshark Lab that will cover TLS – whose treatment in the 8th edition of our text replaces the coverage of SSL.
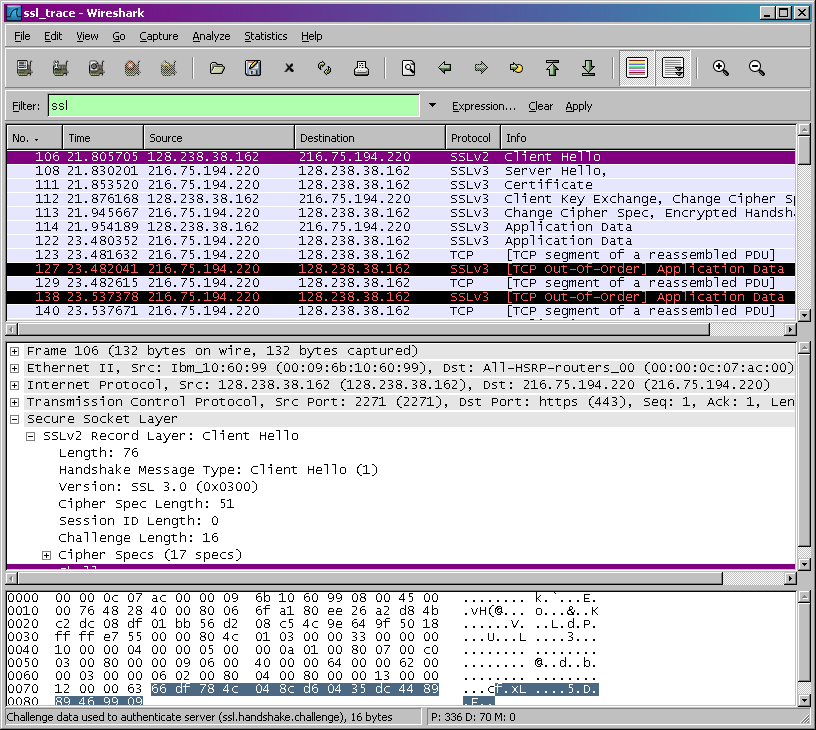
Your Wireshark GUI should be displaying only the Ethernet frames that have SSL records. It is important to keep in mind that an Ethernet frame may contain one or more SSL records. (This is very different from HTTP, for which each frame contains either one complete HTTP message or a portion of a HTTP message.) Also, an SSL record may not completely fit into an Ethernet frame, in which case multiple frames will be needed to carry the record.
Expand the ClientHello record. (If your trace contains multiple ClientHello records, expand the frame that contains the first one.) What is the value of the content type?
Does the ClientHello record contain a nonce (also known as a “challenge”)? If so, what is the value of the challenge in hexadecimal notation?
Does this record include a session ID? What is the purpose of the session ID?
Does this record contain a certificate, or is the certificate included in a separate record. Does the certificate fit into a single Ethernet frame?
In the encrypted handshake record, what is being encrypted? How?
Does the server also send a change cipher record and an encrypted handshake record to the client? How are those records different from those sent by the client?





