Virtual private network vpn management and ipsec tunneling technology
Running head: PROJECT PART 4: FINAL NETWORK DESIGN REPORT 1
PROJECT PART 4: FINAL NETWORK DESIGN REPORT
PROJECT PART 4: FINAL NETWORK DESIGN REPORT 2
Executive summary
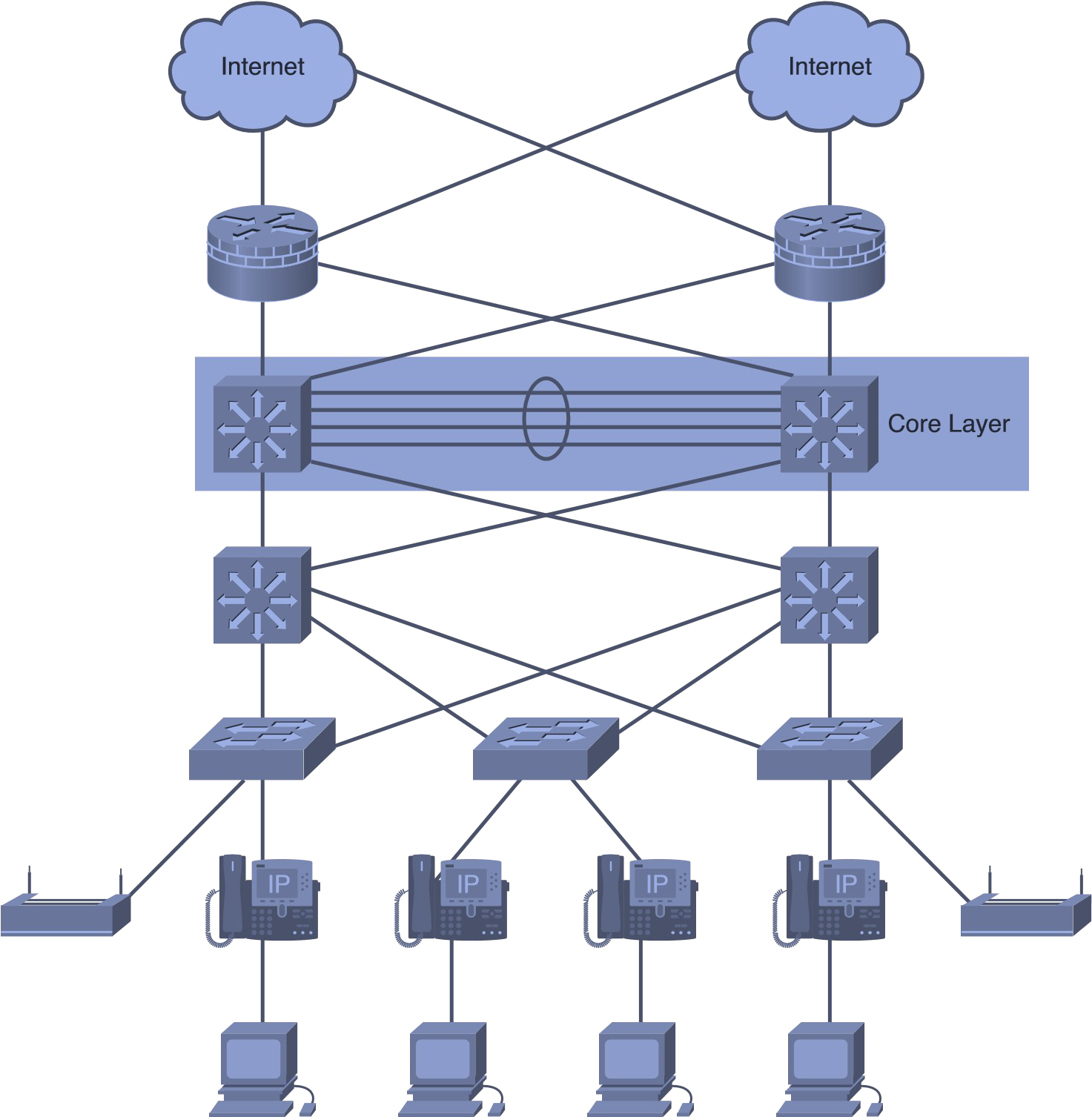
The corporation will have a Hierarchical network topology. The network design will help the company in achieving different goals. As shown in Figure 1 below, the network diagram has different layers, which will help increase the security besides the connection of the distribution layer devices critical in the provision of interconnection to all smaller local networks (Stewart, 2013). In addition, the topology has an access layer that is critical in offering connectivity of all network hosts and end devices.
Figure 1. Hierarchical Network topology
 |
|---|
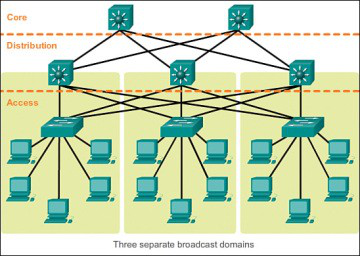
Figure 2. Cisco Enterprise Architecture
Source: Stewart (2013).
Determining project scope
The needs of the network will be detailed in this section. The topology created will help in the isolation of the departments, as seen in Figure 2. Because of the network architecture, it is critical to make sure the sales and accounting sections have been considered in the development of the network. The network is impacted by some factors, including the changes in the applications, improvement in efficiency, which will help deal with the routing protocol transformation, integration of new security features, and new network services besides relocation of servers to the new datacenter.
PROJECT PART 4: FINAL NETWORK DESIGN REPORT 6
PROJECT PART 4: FINAL NETWORK DESIGN REPORT 7
Network convergence
PROJECT PART 4: FINAL NETWORK DESIGN REPORT 8
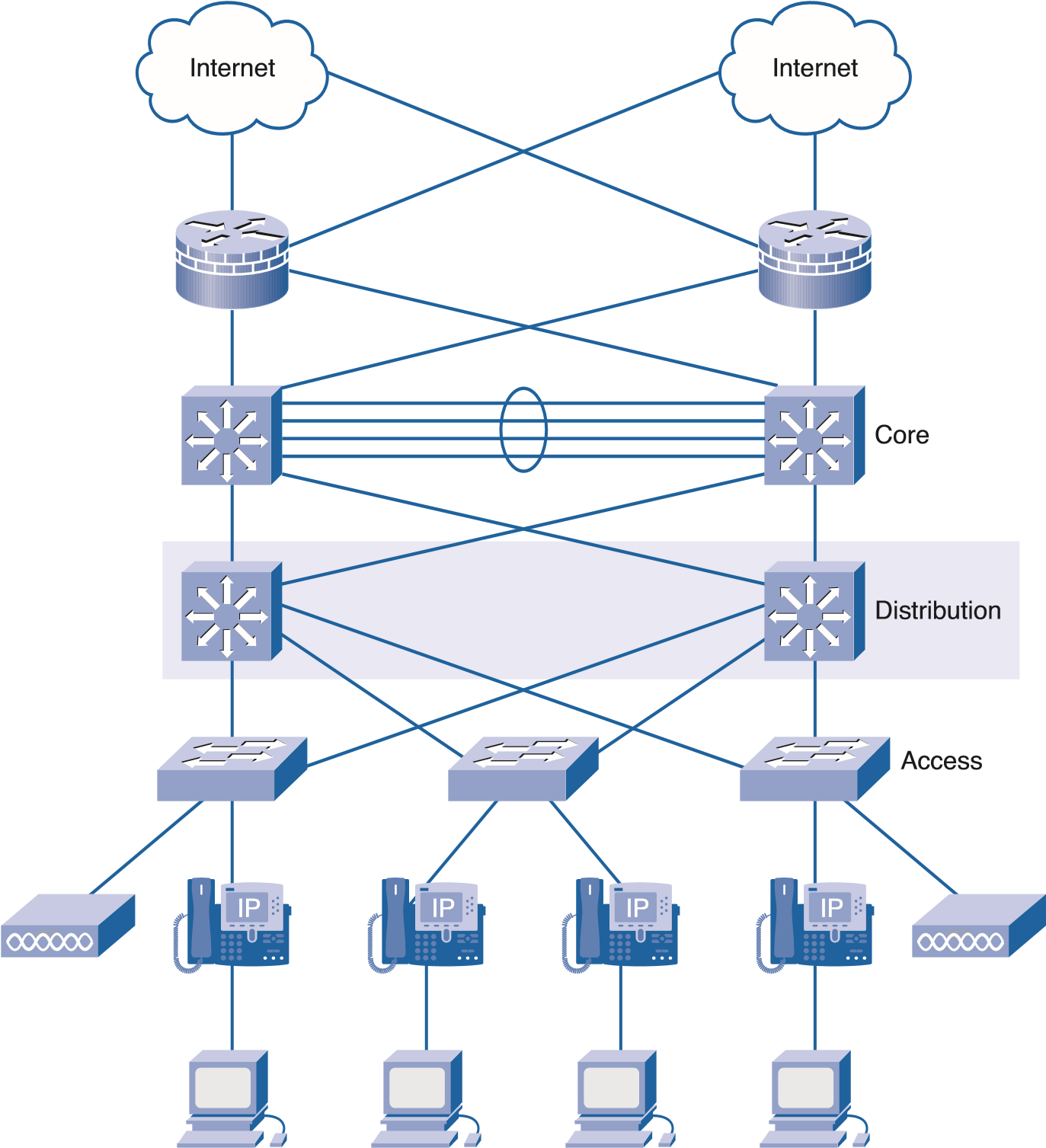
PROJECT PART 4: FINAL NETWORK DESIGN REPORT 9
The access layer in the campus infrastructure can use a three-layer switch technology to access the network. First, the access will be wireless besides physical. Second, the physical connection can use copper-wire ethernet for business computers and a wireless network for distance besides far-off device connections. Finally, this is the layer that will provide IP networks to telephones, cameras besides video conferencing.
PROJECT PART 4: FINAL NETWORK DESIGN REPORT 10
Source: Stewart (2013).
The network at the corporation will be used by a large number of people, which makes it critical to have more than one type of firewall protection. The software firewall will help secure the network's software besides hardware segments for efficiency (Mohammed, & UENO, 2018). The rationale for selecting the software firewall is the capabilities of the firewall to filter all content entering the network system, which will help reduce the infection of the operating system and other areas of the network.
PROJECT PART 4: FINAL NETWORK DESIGN REPORT 11
This is a major activity in ensuring the security of the network. All users of the internal network will have a Username besides a password. In addition, the company will use a biometric fingerprint scanner to provide authentication of users before employees accessing the system. In addition, only the network administrator will have access to all network user credentials. This will help in increasing the security of the network.
Supportive documentation
Part 3: Remote Access and VPNs
This section will cover the design and development of remote access controls and the VPNs within the corporation. The main purpose of this section is to offer the best practices using VPNs besides access controls, which will help maximize the security application in Tech corporation.
security is applied to all traffic within the VPN. Therefore, the workstations will not incur any overhead in terms of security-associated processing.
Furthermore, a VPN needs to be transparent in terms of application. Due to the VPN location in the transport layer, it is transparent to all its applications, eliminating the need for changes of the software on user server systems during the IPsec execution within a firewall (Ibrahim, 2017). the last rationale for the selection of IPsec is the use of basic knowledge in the use of the VPN. Unlike other VPNs, IPsec does not need the training of employees on how to use this security mechanism since the VPN offers security for every user when necessary. The IPsec VPN is also critical in offering services to offsite users and can also be applied in the setting up of virtual subnet in a firm's critical applications. All these features are critical to Tech Corporation since it has offsite workstations, customers who use the company network, thus making it more critical to use such a VPN.
PROJECT PART 4: FINAL NETWORK DESIGN REPORT 14
sending packets with no Port number assigned, thus enabling them to pass across the firewalls (Ibrahim, 2017). However, the selection of IPsec VPN will help in encapsulating the ESP packets in UDP packets will serve a great purpose in assigning UDP numbers on all data, which will help prevent the NAT firewall vulnerability from being exploited.
Recommended Remote Access
Remote access recommended for the Corporation is Point-to-Point. Customers of Tech Corporation are allowed to connect to the firm's servers, which necessitates access controls. The Point-to-Point protocol will help link the control protocols to allow communication between the host network and the client ((Mahmmod, Azeez, & Ahmed, 2020). In addition, this protocol
References
Ibrahim, L. (2017). Virtual private network (VPN) management and IPSec tunneling technology. The Middle East, 1.
Zhipeng, Z., Chandel, S., Jingyao, S., Shilin, Y., Yunnan, Y., & Jingji, Z. (2018, February). VPN: a boon or trap?: a comparative study of MPLs, IPSec, and SSL virtual private networks. In 2018 Second International Conference on Computing Methodologies and Communication (ICCMC) (pp. 510-515). IEEE.