The used and udio compression partions tral methods
A Project Report
on
CREDI-CRYPT: AN IMPROVISED ANTI-COUNTERFEITING
Mrs .V. REKHA ANDAL (M.E)
(ASST. PROFESSOR)

(approved by AICTE and Affiliated to JNTUH)
Mangalpally (V), Ibrahimpatnam (M), R.R.DIST-501510
COUNTERFEITING TECHNIQUE FOR CREDIT CARD TRANSACTION SYSTEM” is
being submitted by
TECHNOLOGY in Electronics and Communication Engineering, Jawaharlal Nehru Technological
University, Hyderabad during the academic year 2011-15.
We owe a great many thanks to many people who have helped and supported us throughout this project, which would not have taken shape without their co-operation. Thanks to all.
We express our profound gratitude to Sri CH. Venugopal Reddy, Secretary and indebtedness to our management, BHARAT INSTITUTE OF ENGINEERING & TECHNOLOGY, IBRAHIMPATNAM for their constructive criticism.
BY
K.ARCHANA (11E11A0406)
A.S.MARIA JASEENTHA
(11E11A0415) P.VARUN
KUMAR (11E11A0455)
3. ANALYSIS
3.1 Introduction
3.2 Software Requirement Specification
3.2.1 sofware reqirement
3.3 Content diagram of Project
3.4 Conclusion4. DESIGN
4.1 Implementation
4.2 Conclusion
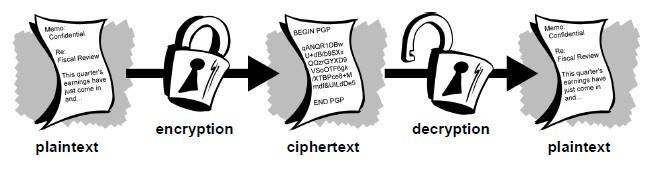
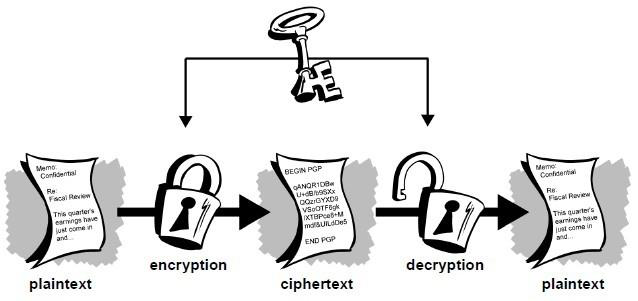
Data encryption is vital for e-commerce. Here we introduce a technique for hiding sensitive credit card information in an arbitrary background image without the sensitive data getting exposed in public domains. The paper also makes an attempt to combine Cryptographic and Steganographic technique to provide a reliable security solution for credit card transactions. The proposed technique utilizes a cryptographic code and Arithmetic Coding technique to hide data inside a cover image and then transmit it to the destination over the web network. The paper also provides an additional layer for enhanced security via the use of Hamming Code. A detailed study is made to compare our
| technique | with | other | prominent | techniques | like | DCT | and | DWT. |
|---|
1.INTRODUCTION
In general, each step of the encoding process, except for the very last, is the same. The encoder has basically just three pieces of data to consider: the next symbol that needs to be encoded, the current interval (at the very start of the encoding process, the interval is set to [0, 1]), but that will change) and the probabilities the model assigns to each of the various symbols.
The encoder divides the current interval into sub-intervals, each representing a fraction of the current interval proportional to the probability of that symbol in the current context. Whichever
Steganography gained importance in the past few years due to the increasing need for providing secrecy in an open environment like the internet. With almost anyone can observe the communicated data all around, steganography attempts to hide the very existence of the message and make communication undetectable.
1.3 OBJECTIVE OF THE PROJECT
The main objective of making Steganographic encoding difficult to detect
is to ensure that the changes to the cover image by the injection of the
embedded image is negligible. Many techniques are used to secure
information such as cryptography that aims to scramble the information
sent and make it unreadable while steganography is used to conceal the
information so that no one can sense its existence. In most algorithms
used to secure information both steganography and cryptography are used
together to secure a part of information.
2. LITERATION SURVEY
2.1 INTRODUCTION
There are a vast number of tools that are available for steganography. An important distinction that should be made among the tools available today is the difference between tools that do
steganography, and tools that do steganalysis, which is the method of detecting steganography and destroying the original message. Steganalysis focuses on this aspect, as opposed to simply
discovering and decrypting the message,because this can be difficult to do unless the encryption keys are known.A comprehensive discussion of steganography tools is beyond the scope of this
article. However, there are many good places to find steganography tools on the Net. One good place to start your search for stego tools is on Neil Johnson's Steganography and Digital Watermarking Web site. The site includes an extensive list of steganography tools. Another comprehensive tools site is located at the StegoArchive.com.For steganalysis tools, a good site to start with is Neil Johnson's Steganalysis site.Niels Provos's site, is also a great reference site, but is currently being relocated, so keep checking back on its progress.
Encryption and decryption
| suited | for | approximating | data | with | sharp |
|---|
The wavelet analysis procedure is to adopt a wavelet prototype function, called an analyzing wavelet or mother wavelet. Temporal analysis is performed with a contracted, high-frequency version of the prototype wavelet, while frequency analysis is performed with a dilated, low-frequency version of the same wavelet. Because the original signal or function can be represented in terms of a wavelet expansion (using coefficients in a linear combination of the wavelet functions), data operations can be performed using just the corresponding wavelet coefficients. And if you further choose the best wavelets adapted to your data, or truncate the coefficients below a threshold, your data is sparsely represented. This sparse coding makes wavelets an excellent tool in the field of data compression.
Other applied fields that are making use of wavelets include astronomy, acoustics, nuclear engineering, sub-band coding, signal and image processing, neurophysiology, music, magnetic resonance imaging, speech discrimination, optics, fractals, turbulence, earthquake-prediction, radar, human vision, and pure mathematics applications such as solving partial differential equations.
| transforms, a key advantage it has over Fourier transforms is temporal resolution: it captures both |
|---|
The discrete wavelet transform has a huge number of applications in science, engineering, mathematics and computer science. Most notably, it is used for signal coding, to represent a discrete signal in a more redundant form, often as a preconditioning for data compression. Practical applications can also be found in signal processing of accelerations for gait analysis, in digital communications and many others.
It is shown that discrete wavelet transform (discrete in scale and shift, and continuous in time) is successfully implemented as analog filter bank in biomedical signal processing for design of low-
| power | pacemakers | and | also | in | ultra-wideband | (UWB) | wireless |
|---|
The general idea behind it is that it doesn't decimate the signal. Thus it produces more precise information for the frequency localization. From the computational point of view the undecimated wavelet transform has larger storage space requirements and involves more computations.
In this research work, image is restored using fourier transform and wavelet transform.
| Two-dimensional DCT frequencies from the |
|
|---|
Disadvantage with DCT is that only spatial correlation of the pixels inside the single 2-D block is
considered and the correlation from the pixels of the neighboring blocks is neglected. Blocks cannot
2.4 PROPOSED SYSTEM
Cryptography :
Cryptography is the science of using mathematics to encrypt and decrypt
data. Cryptography enables you to store sensitive information or
transmit it across insecure networks (like the Internet) so that it
cannot be read by anyone except the intended recipient. While
cryptography is the science of securing data, cryptanalysis is the
science of analyzing and breaking secure communication. Classical
cryptanalysis involves an interesting combination of analytical
reasoning, application of mathematical tools, pattern finding, patience,
determination, and luck. Cryptanalysts are also called attackers.
Cryptology embraces both cryptography and cryptanalysis.
Strong Cryptography :
“There are two kinds of cryptography in this world:
cryptography that will stop your kid sister from reading your files, and
cryptography that will stop major governments from reading your files.
This book is about the latter.” PGP is also about the latter sort of
cryptography.
| conventional | cryptosystem | that | is | widely | employed | by | the | Federal |
|
|---|
Key management and conventional encryption:
Conventional encryption has benefits. It is very fast. It is especially
useful for encrypting data that is not going anywhere. However,
conventional encryption alone as a means for transmitting secure data
can be quite expensive simply due to the difficulty of secure key
distribution. Recall a character from your favorite spy movie: the
person with a locked briefcase handcuffed to his or her wrist. What is
in the briefcase, anyway? It’s probably not the missile launch
code/biotoxin formula/invasion plan itself. It’s the key that will
decrypt the secret data.
For a sender and recipient to communicate securely using conventional encryption, they must agree upon a key and keep it secret between themselves. If they are in different physical locations, they must trust a courier, the Bat Phone, or some other secure communication medium to
3.1 INTRODUCTION
After analyzing the requirements of the task to be performed, the next step is to analyze the problem and understand its context. The first activity in the phase is studying
the existing system and other is to understand the requirements and domain of the new
system. Both the activities are equally important but the first activity serves as a basis of
giving the functional specifications and then successful design of the proposed system.Understanding the properties and requirements of a new system is more difficult and requires creative thinking as well as understanding of existing system is also difficult.
MATLAB will be used extensively in the labs of "Signals and Systems" and "Digital Signal processing" courses.
MATLAB is an interactive program for numerical computation and data visualization; it is used extensively by control engineers for analysis and design. There are many different toolboxes available which extend the basic functions of MATLAB into different application areas; in these tutorials, we will make extensive use of the Control Systems Toolbox. MATLAB is supported on UNIX, Macintosh, and Windows environments; a student version of MATLAB is available for
| personal computers. For more information on MATLAB, contact the |
|---|
The Origin of MATLAB
MATLAB, which stands for MATrix Laboratory, is a software package
developed by Math-Works, Inc. to facilitate numerical computations as
well as some symbolic manipulation. The collection of programs
(primarily in FORTRAN) that eventually became MATLAB was developed in
the late 1970s by Cleve Moler, who used them in a numerical analysis
course he was teaching at the University of New Mexico. Jack little and
Steve Bangert later reprogrammed these routines in C, and added M-files,
toolboxes, and more powerful graphics (original versions created plots
by printing asterisks on the screen). Moler, little, and Bangert founded
Math Works in California in 1984. This beginner's guide provides an
overview of MATLAB, some of its capabilities and the resource of MATLAB
in the EE department. MATLAB is available on a number of computing
platforms such as Sun/HP/VAX workstations, 80x86 PCs, Apple Macintosh,
and several parallel machines. In the City U Electronic Engineering
Department, UNIX version of MATLAB 5.0 is available in the Image
Processing Lab and EDA center. The PC version of MATLAB 5.1 is available
in Microprocessor Lab. The information of this guide generally applies
to all these environments. The aim of MATLAB is to enable us to solve
complex numerical problems, without having to write programs in
traditional languages like C and FORTRAN. Thus, MATLAB
interprets commands like Basic does, instead of compiling source code
like C and FORTRAN require. By using the relatively simple
programming capability of MATLAB, it is very easy to create new commands
and functions in MATLAB. In addition, these developed MATLAB programs
(or scripts) can run without modification on different computers with
MATLAB. Today, MATLAB has evolved into a very powerful programming
environment by providing numerous toolboxes such as signal processing,
image processing, and controls, optimization, and statistics
computations.
The emphasis of this beginner's guide is on the basic MATLAB commands with investigation on some aspects of signal processing. It is intend to be used, while sitting at a computer terminal running MATLAB.
|
|---|
|
|
|---|
OTHER FEATURES
•High-level language for technical computing.•Development environment for managing code, files, and data.
•Functions for integrating MATLAB based algorithms with external applications and languages, such as C, C++, FORTRAN, Java, COM, and Microsoft Excel.
•Delivers floating point precision derivatives (better robustness).
•The classes allows for the use of MATLAB's sparse matrix representation to exploit occurring in the derivative calculation at runtime.
•Normally faster or equally fast as numerical differentiation.
• Support for if, then, else statements.
• Interface to constraint programming engine.
•Lack of library name conventions.
•Lack of object orientated features.
THE MAT LAB ENVIRONMENT
This document is a reference for the core tools you use to work with MATLAB. It provides an introduction to each tool. For more details about these tools, or for instructions on performing tasks in MATLAB using these tools, see the books Getting Started with MATLAB, Using MATLAB, or
| MATLAB | Graphics. |
|---|