The main finding includes all the clown images and related contents
Table of Content
Summary ………………………………………………………………………………………………………………………….2
Email evidence found ……………………………………………………………………………………………………….7
Report on findings …………………………………………………………………………………………………………….9
For this investigation, we have contacted by the client who has asked us to examine the image that they have acquire from the suspects’ computer. Clark is suspected of storing and sharing of clown contents that is illegal to have. His computer is forensically captured using FTK imager with logical acquisition done on the image.
All the investigation was done by __________ on date __________. The investigate image was downloaded and used from the authentic source, the university website. In the investigation process all the images and other contents that were obtained. To maintain the integrity Hash functionality is used time to time to keep the source and obtained files remain same and the integrity of the files will be maintained.
| Host OS | Ubuntu 18.6.0 |
|---|---|
| Forensics Software | Autopsy |
| Unzip Software | 7zip, WinRAR, Git-tool |
| Hardware used | HP pavilion |
| RAM | 6 GB |
| Hard Disk | 500 GB |
| Processor | 1.80 GHz |
| Other hardware Used | USB2.0 Kingston 16 GB |
| Documenting Application | Microsoft word 2010 |
| Function Used to Check integrity | SHA1, MD5 |
| Date | Time | Action | Motive |
|---|---|---|---|
| 12-10-2018 | 12:27:46 PM | Downloading of image 182.dd from website | To start the investigation |
| 12-10-2018 | 03:48:21 PM | Using hash function on the spited image | To check the integrity of the image files |
| 12-10-2018 | 04:01:11 PM | Combining the images with 7zip | To make a combined image from the spited images |
| 12-10-2018 | 04:47:27 PM | Create folder in the drive | To save the image file |
| 12-10-2018 | 05:01:24 PM | Using hash function on the image | To check the integrity |
Collection of Evidence –
Clown images searched:
| Access Date | Time | Image Location | Output |
|---|---|---|---|
| 2018-06-18 | 08:22:16 |  |
|
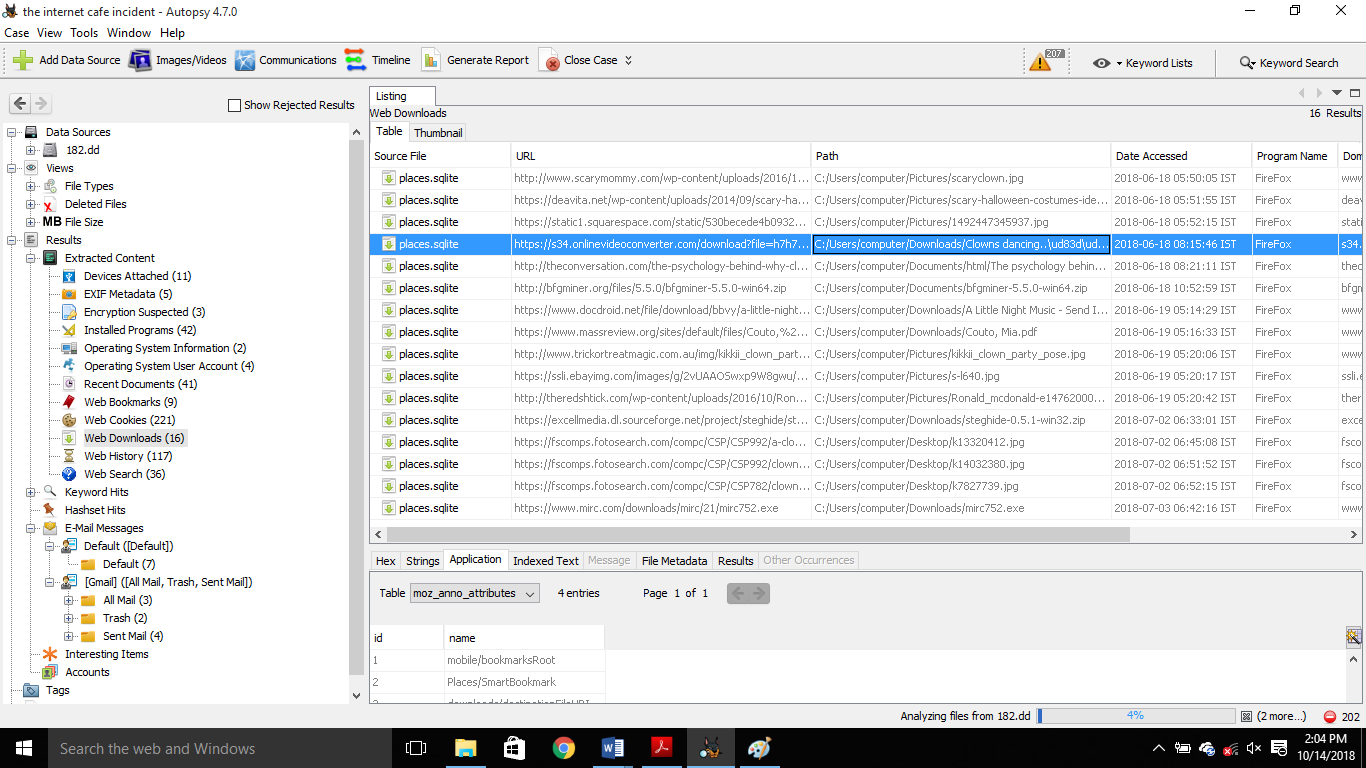
| 2018-07-02 | 09:12:32 | /img_182.dd/Users/computer/Desktop/k13320412.zip/k14032380.jpg |  |
| 2018-07-02 | 09:21:54 | /img_182.dd/Users/computer/Desktop/k13320412.zip/k14032380.jpg |  |
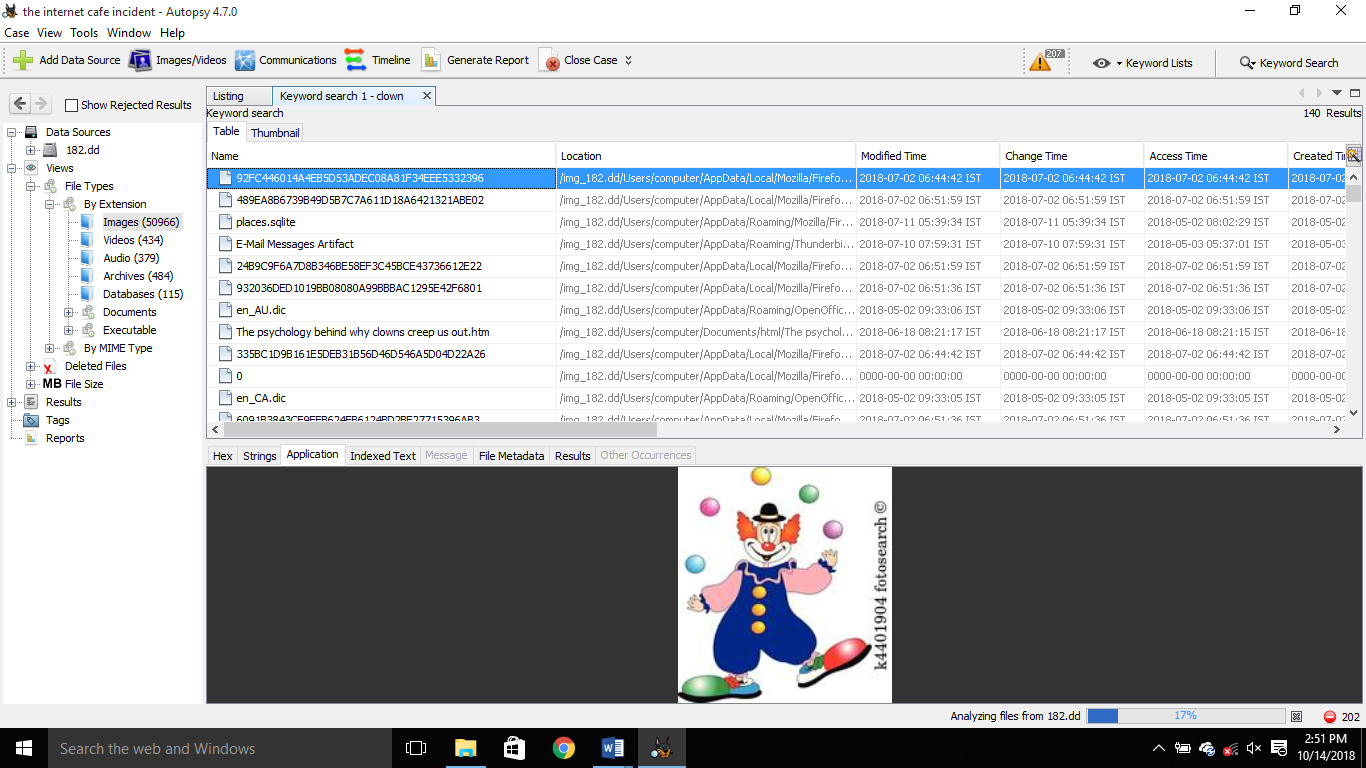
| 2018-06-19 | 07:50:08 | /img_182.dd/Users/computer/Desktop/k13320412.zip/kikkii_clown_party_pose.jpg |  |
| 2018-06-19 | 07:50:44 |  |
|
| 2018-07-02 | 09:22:16 | /img_182.dd/Users/computer/Desktop/k13320412.zip/k7827739.jpg |  |
| 2018-06-18 | 08:20:08 | /img_182.dd/Users/computer/Desktop/k13320412.zip/scaryclown.jpg |  |
| 2018-06-18 | 08:21:12 | /img_182.dd/Users/computer/Documents/html/The psychology behindwhyclownscreepusout_files/image-20160926-31853-1jvhtv4.jpg |  |
| 2018-06-18 | 08:21:56 | /img_182.dd/Users/computer/Desktop/k13320412.zip/ scary-halloween-costumes-ideas-Clown-blood-Halloween-party-costumes-e1410943909179.jpg |
 |
| Date & Time | To | From | Email massage | |||
|---|---|---|---|---|---|---|
| 2018-05-02 05:21:54 | kcent00@gmail.com | no-reply@accounts.google.com |
|
|||
| 2018-05-03 05:34:54 | kcent00@gmail.com | no-reply@accounts.google.com | ||||
| 2018-05-03 05:42:35 | kcent00@gmail.com | sassypenguin0@gmail.com | Sub-Recent data breach Clark, Chief |
|||
| 2018-05-12 20:44:45 | kcent00@gmail.com | privacy-noreply@policies.google.com | 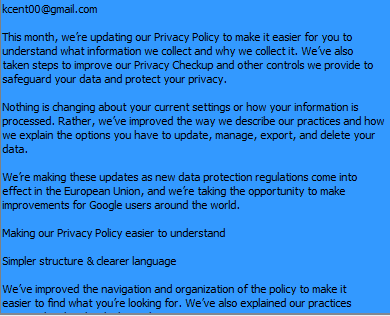 |
|||
| 2018-06-18 08:41:33 | kcent00@gmail.com | jazzasimpson0000@gmail.com | Sub-clowning about |
|||
| 2018-06-19 05:19:29 | sassypenguin0@gmail.com | kcent00@gmail.com | a hangover. Sorry I didn't stay out very late it has been a rough week. Are you interested in checking out a bar this weekend? |
|||
| 2018-07-02 07:50:09 | jazzasimpson0000@gmail.com | kcent00@gmail.com | ||||
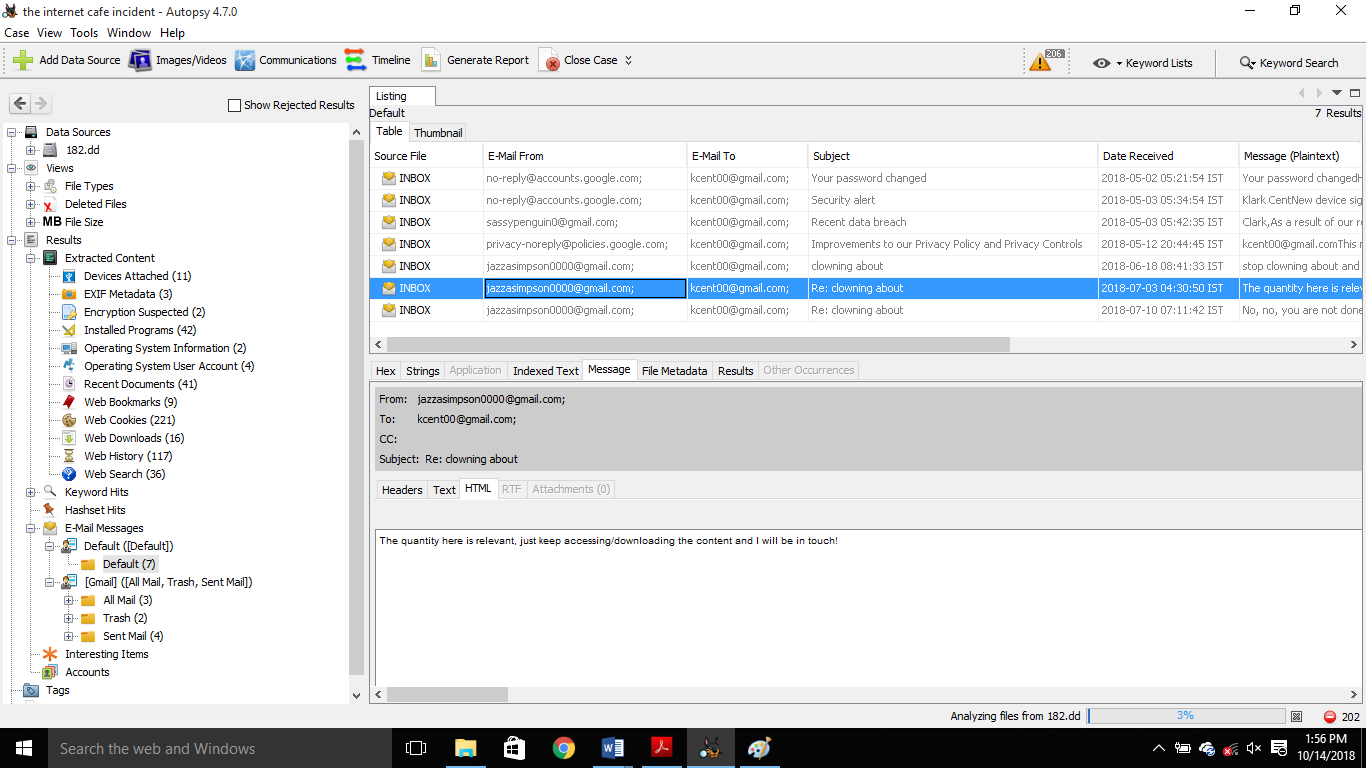
| 2018-07-03 04:30:50 | kcent00@gmail.com | jazzasimpson0000@gmail.com | Sub-Re-clowning about The quantity here is relevant, just keep accessing/ downloading the content and I will be in touch! |
|||
| 2018-07-09 08:54:08 | jazzasimpson0000@gmail.com | kcent00@gmail.com | Attachment – k13320412.zip |
|||
| 2018-07-10 07:11:42 | kcent00@gmail.com | jazzasimpson0000@gmail.com | Sub-Re: clowning about On 3/07/2018 7:00 AM, Jerry Simpson wrote: The quantity here is relevant, just keep accessing/downloading the content and I will be in touch! |
|||
| 2018-07-11 05:41:46 | sassypenguin0@gmail.com | kcent00@gmail.com | what to do...I will come by your office in a few minutes! >> Regards, |
End of findings
Email Evidence found in the image –
Evidence of downloading clown related contents found –
Hashing the images: MD5 checksum: 15f5d5224b4bed8a97b6fc0c2a7ecfbc
SHA1 checksum: e710298646c46ee8ff70a96cd4d28423fe274eeb
Started finding the clown related contents –
As the image is mounted and data source is been added I start founding clown contents.
Searching of clown images –
/img_182.dd/Users/computer/Pictures/scary-halloween-costumes-ideas-Clown-blood-Halloween-party-costumes-e1410943909179.jpg
/img_182.dd/Users/computer/Desktop/k13320412.zip/scary-halloween-costumes-ideas-Clown-blood-Halloween-party-costumes-e1410943909179.jpg
All the investigation is done on the provided image file 182.dd. after completing the investigation, I was successfully recovered all the clown contents from the image. There were I found many of the clown images and other related contents i.e. PDFs, Videos. These contents are also used to share with other persons via Emails. The browsing, searching and downloading of clown images and other contents were clearly found. And also, at the same timestamp that contents are saved in the drive of the user Clark. Based on the finding, it clearly proves that Clark is involve in accessing the clown contents and all the evidence refusing the statement of Clark that he said about his innocent. He offends the rules and found involve in illegal activities. He should be punished against the laws which should be penalized.
End of Report