Telnet port the web server and look the default page code

TestKingonline.com No Pass No Pay!
You have purchased a TestKingonline. Study Guide.
This study guide is a complete collection of questions and answers that have been developed by our professional & certified team. You must study the contents of this guide properly in order to prepare for the actual certification test. The average time that we would suggest you for studying this study guide is approximately 10 to 20 hours and you will surely pass your exam. We guarantee it!
©Copyrights 2005-2006 TestKingonline All Rights Reserved.
Table of contents
Topic 1, Ethics and Legal Issues (6
questions)............................................................................................... 4
Topic 2, Footprinting (17
questions).................................................................................................................. 6 Topic 3, Scanning (47 questions)
.................................................................................................................... 14
Topic 4, Enumeration (26 questions)
.............................................................................................................. 35
Topic 5, System Hacking (20
questions)........................................................................................................ 46 Topic 6, Trojans and Backdoors (13
questions)............................................................................................ 55
Topic 7, Sniffers (6 questions)
......................................................................................................................... 61 Topic 8, Denial of Service (17 questions)
...................................................................................................... 64
Topic 9, Social Engineering (8
questions)...................................................................................................... 71 Topic 10, Session Hijacking (6 questions)
..................................................................................................... 75
Topic 11, Hacking Web Servers (14
questions)............................................................................................ 78
Topic 12, Web Application Vulnerabilities (7
questions).............................................................................. 85
Topic 13, Web Based Password Cracking Techniques (1
question)......................................................... 88
Topic 14, SQL Injection (11 questions)
.......................................................................................................... 89
Topic 15, Hacking Wireless Networks (10
questions).................................................................................. 96
Topic 16, Virus and Worms (7 questions)
.................................................................................................... 100
Topic 17, Hacking Novell (6 questions)
........................................................................................................ 103
Topic 18, Hacking Linux (7
questions).......................................................................................................... 105 Topic 19, IDS, Firewalls and Honeypots (36
questions)............................................................................ 109
Topic 20, Buffer Overflows (8 questions)
..................................................................................................... 126Topic 1, Ethics and Legal Issues (6 questions)
QUESTION NO: 1
What is the essential difference between an ‘Ethical Hacker’ and a ‘Cracker’?A. Someone who is hacking for ethical reasons.
B. Someone who is using his/her skills for ethical reasons. C. Someone who is using his/her skills for defensive purposes. D. Someone who is using his/her skills for offensive purposes.
QUESTION NO: 4
What is "Hacktivism"?A. Hacking for a cause
B. Hacking ruthlessly
C. An association which groups activists
D. None of the aboveAnswer: A, B, C, D, E, F
QUESTION NO: 6
What are the two basic types of attacks?(Choose two.QUESTION NO: 1
You are footprinting Acme.com to gather competitive intelligence. You visit the acme.com websire for contact information and telephone number numbers but do not find it listed there. You know that they had the entire staff directory listed on their website 12 months ago but now it is not there. How would it be possible for you to retrieve information from the website that is outdated?A. Visit google search engine and view the cached copy.
©Copyrights 2005-2006 TestKingonline All Rights Reserved.
A. 18 U.S.C 1029 Possession of Access Devices
B. 18 U.S.C 1030 Fraud and related activity in connection with computers C. 18 U.S.C 1343 Fraud by wire, radio or television
D. 18 U.S.C 1361 Injury to Government Property
E. 18 U.S.C 1362 Government communication systems
F. 18 U.S.C 1831 Economic Espionage Act
G. 18 U.S.C 1832 Trade Secrets ActAnswer: C
QUESTION NO: 4
Which one of the following is defined as the process of distributing incorrect Internet Protocol (IP) addresses/names with the intent of diverting traffic?How would it be possible for you to retrieve information from the website that is outdated?
A. Visit google’s search engine and view the cached copy.
Explanation: Archive.org mirrors websites and categorizes them by date and month depending on the crawl time. Archive.org dates back to 1996, Google is incorrect because the cache is only as recent as the latest crawl, the cache is over-written on each
subsequent crawl. Download the website is incorrect because that's the same as what you see online. Visiting customer partners websites is just bogus. The answer is then Firmly, C, archive.orgQUESTION NO: 6
A Testkingonline security System Administrator is reviewing the network system log files. He notes the following:
- Network log files are at 5 MB at 12:00 noon.C. He should log the file size, and archive the information, because the router crashed. D. He should run a file system check, because the Syslog server has a self correcting file system problem.
E. He should disconnect from the Internet discontinue any further unauthorized use, because an attack has taken place.
©Copyrights 2005-2006 TestKingonline All Rights Reserved.
C. Message repudiation means a recipient can be sure that a message was sent from a particular person.
QUESTION NO: 8
How does Traceroute map the route that a packet travels from point A to point B?A. It uses a TCP Timestamp packet that will elicit a time exceed in transit message.
QUESTION NO: 9
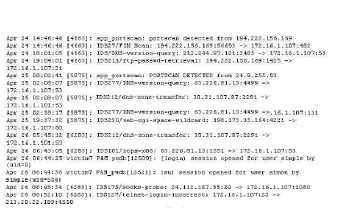
Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal? (Note: The student is being tested on concept learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dumo.)
05/20-17:06:45.061034 192.160.13.4:31337 -> 172.16.1.101:1
TCP TTL:44 TOS:0x10 ID:242
***FRP** Seq: 0XA1D95 Ack: 0x53 Win: 0x400
..
C. The attacker wants to avoid creating a sub-carrier connection that is not normally valid.
D. There packets were created by a tool; they were not created by a standard IP stack.
QUESTION NO: 11
A very useful resource for passively gathering information about a target company is:A. Host scanning
B. Whois search
C. Traceroute
D. Ping sweep©Copyrights 2005-2006 TestKingonline All Rights Reserved.
You immediately enter the following at Windows 2000 command prompt: Ping 0xde.0xad.0xbe.0xef You get a response with a valid IP address.
What is the obstructed IP address in the e-mail URL?Answer: A, B, C, D
Explanation: All of the tools listed are used for footprinting except Cheops.
Scanning should take
place on two distinct levels: network and host.QUESTION NO: 15
NSLookup is a good tool to use to gain additional information about a target network. What does the following command accomplish?Answer: D
Explanation: If DNS has not been properly secured, the command sequence displayed above will perform a zone transfer.
QUESTION NO: 17
Your lab partner is trying to find out more information about a competitors web site. The site has a .com extension. She has decided to use some online whois tools and look in one of the regional Internet registrys. Which one would you suggest she looks in first?A. LACNIC
B. ARIN
C. APNIC
D. RIPE
E. AfriNICQUESTION NO: 1
Doug is conducting a port scan of a target network. He knows that his client target network has a web server and that there is a mail server also which is up and running. Doug has been sweeping the networkbut has not been able to elicit any response from the remote target. Which of the following could be the most likely cause behind this lack of response? Select 4.A. UDP is filted by a gateway
B. The packet TTL value is too low and cannot reach the target C. The host might be down
D. The destination network might be down
E. The TCP windows size does not match
F. ICMP is filtered by a gatewayWhat does the first and second column mean? Select two.
A. The first column reports the sequence number
B. The second column reports the difference between the current and last sequence number
C. The second column reports the next sequence number
D. The first column reports the difference between current and last sequence numberA. The firewall is dropping the packets.
B. An in-line IDS is dropping the packets.
What can you infer from the above log?
©Copyrights 2005-2006 TestKingonline All Rights Reserved.
Bob has been hired to perform a penetration test on testkingonline.com. He begins by looking at IP address ranges owned by the company and details of domain name registration. He then goes to News Groupsand financial web sites to see if they are leaking any sensitive information of have any technical detailsonline.
A. To create a denial of service attack.
B. To verify information about the mail administrator and his address.
What should be the next logical step that should be performed?
A. Connect to open ports to discover applications.
A. A half-scan
B. A UDP scan
C. A TCP Connect scan©Copyrights 2005-2006 TestKingonline All Rights Reserved.
A. Idle Scan
B. Windows Scan
C. XMAS Scan
D. SYN Stealth ScanAnswer: C
D. A good security tester would not use such a derelict technique.
Answer: B
D. He is attacking an operating system that does not reply to telnet even when open.
©Copyrights 2005-2006 TestKingonline All Rights Reserved.
D. Nmap with the –sO (Raw IP packets) switch.
Answer: D
D. The ping command does not use ICMP but uses UDP.
Answer: A
D. The systems are running Windows.
Answer: D
QUESTION NO: 15C. Telnet to port 8080 on the web server and look at the default page code. D. Telnet to an open port and grab the banner.
Answer: D
QUESTION NO: 17
What port scanning method involves sending spoofed packets to a target system and then looking for adjustments to the IPID on a zombie system?A. Blind Port Scanning
B. Idle Scanning
C. Bounce Scanning
D. Stealth Scanning
E. UDP ScanningA. Null Scanning
B. Connect Scanning
C. ICMP Scanning
D. Idlescan Scanning
E. Half Scanning
F. Verbose ScanningAnswer: B
QUESTION NO: 20
Because UDP is a connectionless protocol: (Select 2)A. UDP recvfrom() and write() scanning will yield reliable results
B. It can only be used for Connect scans
C. It can only be used for SYN scans
D. There is no guarantee that the UDP packets will arrive at their destination E. ICMP port unreachable messages may not bereturned successfullyA. Nmap with the –sO (Raw IP packets) switch
B. Nessus scan with TCP based pings
C. Nmap scan with the –sP (Ping scan) switch
D. Netcat scan with the –u –e switchesAnswer: A
A. Windows 2000 Server running IIS 5
B. Any Solaris version running SAMBA Server C. Any version of IRIX
D. RedHat Linux 8.0 running Apache Web ServerAnswer: A