Hardware failure and its impact the protocol stacks
DATA AND NETWORKING
| MIS 102 |
|---|
Introduction..........................................................................................................................................2 Purpose of this report.....................................................................................................................2 Overview of this report...................................................................................................................2 Network disaster recovery plan.........................................................................................................3 1. Internet outage........................................................................................................................3 2. Malware attack:.......................................................................................................................3 3. Hardware failure and its impact in the protocol stacks:.....................................................4 4. Internet loss in particular department...................................................................................4 5. Power outage:.........................................................................................................................5 6. Password security breach:.....................................................................................................5 Precautions and post-planning to ensure the disaster does not occur again.............................6 Anticipation of a potential question by the client.............................................................................7 Network topology diagram.................................................................................................................8 References..........................................................................................................................................9
1
2
00315702T MIS102
An internet outage is a potential disaster in the plus fitness, this disaster has potentially affected the business process. So that, an organization should apply the following solution in order to resolve the issue of internet outage:
LTE fail over: According to (Hardy, 2017) the LTE failover is a potential solution for the internet outage as it helps the organization to resume the business. LTE failover use the data plan which is supported and backup by the internet service provider. So that, plus fitness should contact to their ISP to get the service of LTE failover.
3
00315702T MIS102
Organization has to do the immediate dusting in the hardware because dust can overheat the device which causes the hardware failure.
Devices can overheat sometime so that, organization should consider turning off the devices for a while.
00315702T MIS102
5. Power outage:
After analysing the e-book from (datto, 2020) the immediate recovery plan is described below: In addition, according to (swoop, 2020) while resetting the password users must use 8 characters which include the special characters and number which forms a strong password. Also, all the devices must have different password and the password must be random which cannot be predicted.
5
Organization should also consider establishing a cloud-based email system and applications because cloud-based system enables a user to sync the files and they can access those files from anywhere (datto, 2020).
In order to secure the passwords and secure the data organization has to add the cryptographic protocols into their network as these protocols establish a secure transport layer between devices so that passwords cannot be hacked (Kemmerer, 2020).
While making the disaster plan client will ask about the backup plans and its elements such as how many devices have to be backed up and for the data storage how much space is needed, because while taking the back up of important data secure database has to be purchased.
Client will also have question related the security and privacy of data while taking the backups. In addition, client will also address the question that is there any type of data which is bound by the federal regulations
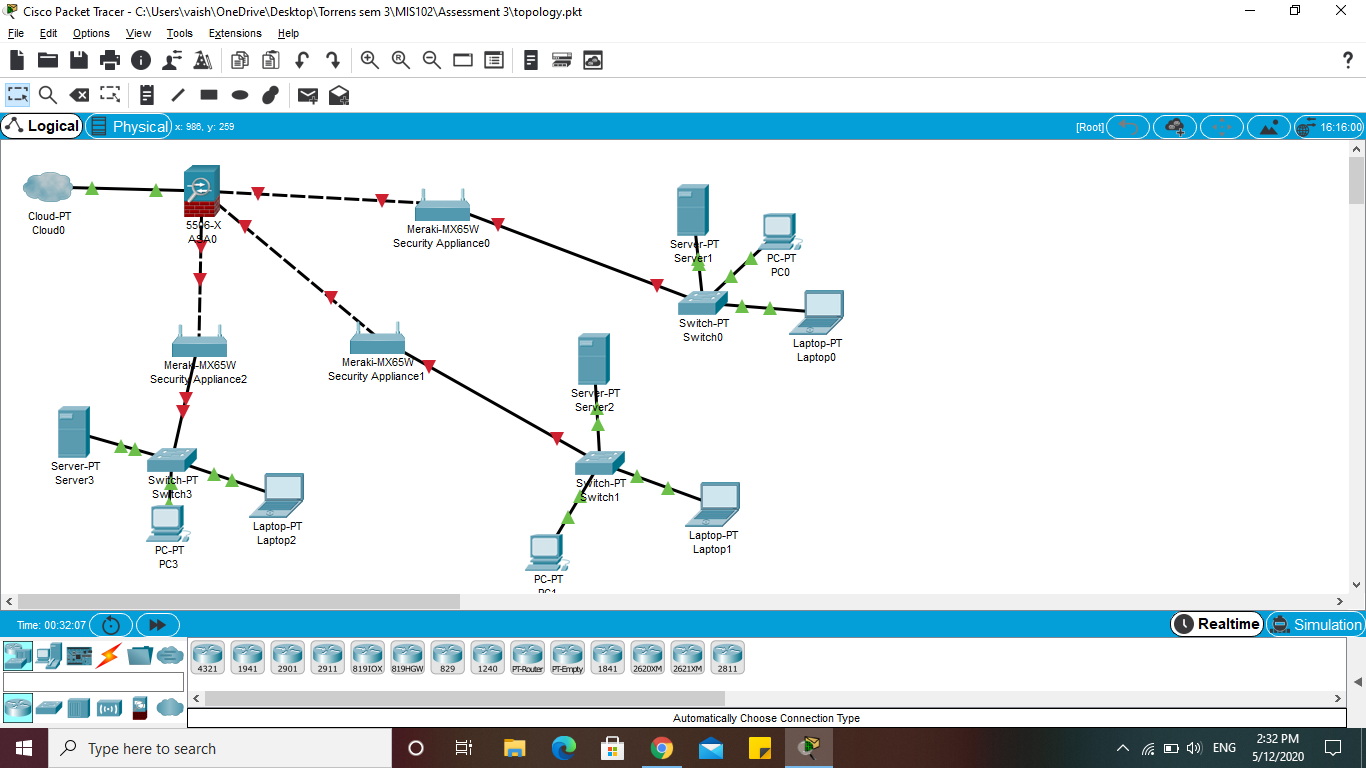
Following network topology is developed based on the organizational structure as they have branches in three major regions Australia, New Zealand, and Asia so that, three main routers are installed in the network. So that, data will first process through the firewall in order to get the secure data then according to the routing table router will route the data to the appropriate switch which are installed in each network. Then switch will analyse the mac addresses and from the switching table the data will send to the data to an appropriate device. For each branch server is installed in order to store the data and manage the system. Fiber optic cables are used in the network to get the best quality speed of internet.
Datto. (2020). THE BUSINESS GUIDE TO POWER OUTAGES [Ebook] (pp. 1-8). Retrieved from
Evans, M. (2018). An assessment of disaster recovery planning: A strategy for data security (pp. 15-35). LPA LAMBERT Academic publishing.
9
00315702T MIS102
Townsend, K. (2020). Backup or Disaster Recovery for Protection Against Ransomware? | SecurityWeek.Com. Retrieved 2 December 2020, from
(2020). Retrieved 4 December 2020, from





