File data and attributes run program files change read permission create folders
|
|---|
2 |
|---|
|
|
|
|---|---|---|
|
||
| |
|
||||||
|---|---|---|---|---|---|---|---|
|
|||||||
| |
|
||||||
| | |||||||
| | |||||||
| | |||||||
| Note: Users that are granted the Create
Permanent Shared Objects right can also create shared folders on the computer where the right is assigned |
|||||||
|
||||
|---|---|---|---|---|
| 1) |
|
|||
| 2) | 1) | |||
| 3) | 2) | |||
| 3) | ||||
|
4) |
|
||
| OR | 5) | |||
| 1) | 6) | |||
| 2) | 7) |
|
||
| 3) | ||||
|
||||
Subfolder 1 ------------ |
|
||||
|---|---|---|---|---|---|
| File 1 | File 2 |
|
|||||
|---|---|---|---|---|---|
Multiple Permissions (The Combination Rule)
If a user is assigned a permission for a Shared folder and
If the use user belongs to a group to which a different permission is
assigned,
Then the user’s effective permissions are the combination of the user and
group permissionsDeny overrides Allow
If you deny a shared folder permission to a user and
If you allow the same permission to a group the user belongs to
Then the user will not have that permission.

10 |
|---|
|
|||
|---|---|---|---|
Standard NTFS permissions
|
|
|---|---|
| Read and Execute | |
|
|
|
|---|
|
|---|
assign permissions for.
15 |
||||||||
|---|---|---|---|---|---|---|---|---|
Permission Inheritance
By default, permissions assigned for the parent folder are inherited at subfolder
and file level
|
|
|---|---|
| to Golden rule |
| Folders/Subfolders | Sharing folders/files |
Setting permissions |
||
|---|---|---|---|---|
| FAT | NTFS | FAT | ||
| YES | YES | YES (but limited) | ||
|
NO | NO | NO |
|
The Golden rule do not apply to encrypted files/folders
EFS is used to encrypt data stored on storage media or data in transit
|
|||
|---|---|---|---|
|
||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
|||
|---|---|---|---|
7

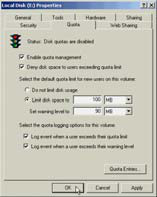
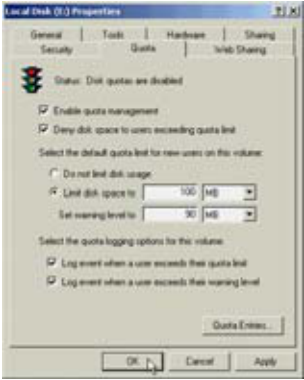
|
|---|
|
|---|
|
|||||
|---|---|---|---|---|---|
|
|||||
|---|---|---|---|---|---|
27 |
|||
|---|---|---|---|
9
|
|||
|---|---|---|---|
|
||||||||
|---|---|---|---|---|---|---|---|---|
10
|
|||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
33 |
|||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|