Entry will logged the windows event viewer the security log
| 250 | Part III: |
|
|---|
users with administrative privileges are allowed to make this type of connection. For these users, configuration locking alters only where the configuration settings are saved, and these users are the only ones who can make modifications in applicationHost.config and the root Web.config.
Figure 8-16 Application connection details in the Connect To Application dialog box.
After clicking Next, you will be prompted for credentials in the dialog box shown in Figure 8-17. As mentioned before, these can be Windows user or IIS Manager users credentials.
| Chapter 8: | 251 |
|---|
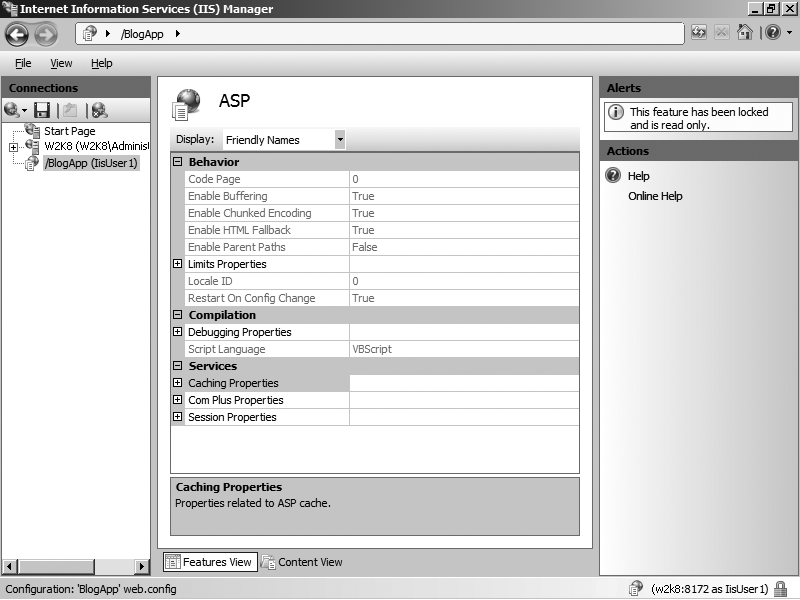
Figure 8-18 ASP feature shown as read-only in an application connection.
| 252 | Part III: | |
|---|---|---|
| Note | When using a different port than the default 8172, you will need to enter it in the |
Administration.config is the file that contains all the settings for IIS Manager and remote administration. Just as the IIS configuration system does, it uses configuration sections to organize the settings into logical units. The most important are <moduleProviders> and <modules>. The <moduleProviders> section contains the centralized list of features that a server administrator will get when using IIS Manager. In other words, it includes the list of features that will be used when a server connection is activated. The <modules> section contains the list of modules that will be enabled for delegated connections (site and application connections). If a feature is listed only in the <moduleProviders> section, only server connections will show that feature. To make that feature available for all the sites, you can add it in the <modules> list inside a location tag by using the special path “.” that denotes it should be available for everyone. Alternatively, you can add it in the name of the site if it should be available only for that site. The Feature Delegation page modifies the <modules> list when you change the delegation state.
One thing to mention is that the delegation for applications is stored in another Administration.config file in the parent site physical path.
■ The Web Management Service has not been started on the remote machine. As mentioned earlier in this chapter, the Web Management Service is responsible for listening for remote requests, and it must be running.
■ A firewall is blocking the client requests. Make sure that a firewall is not blocking the port that Web Management Service uses. By default, the service uses port 8172 and includes a Windows Firewall exception for it. However, if you change the port, you will need to create a firewall exception for it.
netsh http show sslcert
SSL Certificate bindings:
-------------------------■ The user or password is invalid. Whenever an invalid user or password is used to try to access the Web Management Service, an entry will be logged in the Windows Event Viewer in the Security Log. This will include all the details, as shown here.
An account failed to log on.
| 254 | Part III: | ||
|---|---|---|---|
| Logon Type: | |||
Failure Information:
Failure Reason: Unknown user name or bad password.Status: 0xc000006d
Sub Status: 0xc0000064Process:WMSvc
User=NT AUTHORITY\LOCAL SERVICETo correct this, you can go to the specific site or application level inside IIS Manager and use the IIS Manager Permissions feature to grant the delegated user permissions to log on.
Logging
You’ll find it useful to understand the activity of the Web Management Service’s logging functionality. By default, the log files are stored in the %SystemDrive%\Inetpub\Logs\ Wmsvc\ folder. Below this, you will find a folder named W3SVC1 that contains all the log files detailing the activity of the Web Management Service. The log file uses the World Wide