Depending the industry and the companys size and structure
Perspectives on transforming
cybersecurityIntroduction
“Hit or myth? Understanding the true costs and impact of cybersecurity programs” shows that more spending doesn’t necessarily lead to better protection.
“A new posture for cybersecurity in a networked world” explains how companies can use organizational structure and governance to enhance cybersecurity protections.
“Cyberrisk measurement and the holistic cybersecurity approach”. Comprehensive dashboards can accurately identify, size, and prioritize cyberthreats for treatment.
“Cybersecurity and the risk function”. Information technology, cybersecurity, and risk professionals need to work together to protect their organizations from cyberthreats.
“The board’s role in managing cybersecurity risks” lays out what cybersecurity data the board of directors should expect, and the questions it should ask.
“Asking the right questions to define government’s role in cybersecurity” provides a framework for how public policy makers can think about engaging constructively on cybersecurity.
5


J A N U A R Y 2 0 17
| xx | 18 | 27 |
|---|
EPLACE IMAGE
MARCH 2018 • RISK PRACTICE security in a networked world R i s k
© Matt Anderson Photography/Getty Images assets: Not all systems and
| es are using all kinds of ted technologies and techniques critical business assets. But the rtant factor in any cybersecurity s trust. It undergirds all the decisions make about tools, talent, and . Based on our observations, rust is generally lacking in many SEPTEMBER 2018 • RISK ons’ cybersecurity initiatives—in use of competing agendas. Senior |
|
critical importance to a company—must be at the | defenses, furthermore, are oft |
|---|---|---|---|
| heart of an effective strategy to protect against | the perimeter of business oper | ||
|
|||
| cyber threats. Because in an increasingly digitized | disjointedly across different pa | ||
| world, protecting everything equally is not an option. | |||
| website transactions present potential holes Insider threat: The human |
|||
information assets. We call the resilience,” a cross-functional |
|||
| an enterprise-wide basis, and | |||
value can help companies stop sophisticated cybercriminals.
After a long period of experimentation, leading enterprises are getting serious about adopting the public cloud at scale. Over the last several years, many companies have altered their IT strategies to shift an increasing share of their applications and data to public-cloud infrastructureFor all the resources devoted to improving
cybersecurity, threat levels continue to rise
faster than defense capabilities. The WannaCry
ransomware attack in May 2017 offers a
case in point. Hackers helped themselves to
tools stolen from intelligence agencies and1 For more, see Nagendra Bommadevara, James Kaplan, and Irina Starikova, “Leaders and laggards in enterprise cloud infrastructure adoption,”
October 2016, McKinsey.com. Also see Arul Elumalai, Kara Sprague, Sid Tandon, and Lareina Yee, “Ten trends redefining enterprise IT
Cyberrisk measurement and nuclear power station, affecting several parts 1 Cybersecurity and the risk confidentiality, integrity, and availability of systems and information. Some organizations may refer to this function as information security or
IT security. 1





Asking the right questions to define
government’s role in cybersecurity
of cybersecurity in the age of the
|
The board’s role in managing | © cherezoff/Getty Images | |||
|---|---|---|---|---|---|
|
|||||
|
|
118 | |||
| opening them up to new relationships with |
|
||
|---|---|---|---|
|
|||
| new business opportunities. But, as recent headlines have made clear, the very act of | Shifting gears in cybersecurity | ||
|
|||
| for connected cars |
|
||
| the age of the Internet of Things | |||
REPLACE IMAGE
fotomay/Getty Images
Cybersecurity is a critical but often misunderstood aspect of
|
|---|
data, and even about which data sets are Not all data are created with equal value.
most at risk. Perceptions become facts, trust The customer data associated with a bank’s
the reins on the cybersecurity budget until don’t have endless resources to protect all
the CIO or other cybersecurity leaders prove data at any cost, and yet most deploy one-
decide to overspend on new technologies (particularly in the wake of a recent security
without understanding that there are other, nontechnical remedies to keep data and other corporate assets safe.
Separating myths from facts
Based on our work with companies across industries and geographies, we’ve observed that business and cybersecurity leaders fall under the sway of four core myths when
discussing or developing protection programs for corporate assets.In our experience, a strong cybersecurity
strategy provides differentiated protection of the company’s most important assets,
utilizing a tiered collection of security
measures. Business and cybersecurity
leaders must work together to identify and protect the “crown jewels”—those corporate assets that generate the most value for a
company. They can inventory and prioritize assets and then determine the strength of cybersecurity protection required at each level. By introducing more transparency into the process, the business value at risk and potential trade-offs to be made on cost wouldThe business and cybersecurity teams at a healthcare provider, for example, might agree that protecting patient data is the first priority but that confidential financial data must
also be secured so as not to compromise
partner relationships and service negotiations. They could allocate resources accordingly.Without this shared understanding, business
2 Grand theft data, Intel Security, 2015, mcafee.com.
| 3 |
|
|---|
3.5
Well protected3.0
Healthcare
|
Industrial |
|---|
| 0 | 2 | 4 | 6 | 8 | 10 |
|---|
Note: Reflects responses from 45 companies in the Global 500 about their cybersecurity spending and capabilities.
1Companies’ cybersecurity maturity is rated on a scale of 1 to 4, with 4 being the most mature (highest-level talent and capabilities). 2Spending is rated on a scale of 1 to 10; no companies allocated more than 10% of their budget on security.
Myth 4: The more advanced our technology, the more secure we are
It is true that cybersecurity teams often
use powerful, cutting-edge technologies to protect data and other corporate assets.But it is also true that many threats can be mitigated using less-advanced methods.
released March 14, 2017—some two months before the ransomware worked its way into more than 230,000 computers across more than 150 companies.
Building a culture of resilience
Rather than perpetuate myths, business and cybersecurity leaders should focus on bridging the trust gaps that exist between them. We believe most companies can do that when technology and business leaders jointly train their attention on two main
issues of control: how to manage trade-offs associated with cybersecurity, and how to discuss cybersecurity issues and protocols more effectively.4 Patch management is the structured process of acquiring, testing, and installing code changes to an administered computer system.
5
regularly—for instance, cybersecurity spending
as a percentage of overall IT expenditures.
important to have a comprehensive, formal notes (Exhibit 3).
approval process for planning and reviewing
Hit or myth? Understanding the true costs and impact of cybersecurity programs July 2017 13
| 21 | 32 | 29 | 14 | 4 |
|---|
All other
industries
(n = 87)
Note: Executives polled included chief information security officers and other C-suite executives charged with making decisions about cybersecurity investments.
| EXHIBIT 3 Exhibit 3 |
|---|
Note: Executives polled included chief information security officers and other C-suite executives charged with making decisions about cybersecurity investments.
a robust cybersecurity program given the
potential effects on the bottom line if corporate assets are compromised. But each side is typically only getting half the story.Instead of reporting that “ten vulnerabilities were remediated,” for example, technology professionals can use visual aids and
outcomes-oriented language to help business leaders understand potential security threats and ways to address them. A status update might be better phrased in the following
manner: “Our cybersecurity team has patched a security hole in our customer-relationship-management system that could have given hackers access to millions of packets of our retail customers’ data, creating $100 million in financial damage.” Cybersecurity professionals could also clearly delineate and communicate levels of systems access for intended and
unintended users—a database administrator
As we mentioned earlier, technology leaders
Finding a common vocabulary is important not just for ensuring clear communication
between the C-suite and the cybersecurity function but also for raising awareness about potential cyberthreats and risks among
employees throughout the company. Members of the cybersecurity function should schedule frequent, regular check-ins with staff at
all levels to educate them about relevant
cybersecurity topics—how to recognize a
phishing email, for example—and to showcase the company’s security capabilities. The
cybersecurity team at one technology firm
conducts “road shows” to demonstrate
which systems are being scanned and
how they are being monitored. One online
retailer, meanwhile, includes details about
its cybersecurity efforts in existing financial
| 2 |
|
|---|
data breach and files a report with government affairs.
| 4 |
|---|
Typical response
•The security team engages
the communications group.Source: 2015 McKinsey Cyber Risk Maturity Survey
The C-suite and the cybersecurity function
can no longer talk past one another; security must be a shared responsibility across the
business units. It must be embedded in various business processes, with the overarching
goal of building a culture of resilience. The
companies that take steps now to build
greater trust between the business and the IT organization will find it easier to foster a resilient environment and withstand cyberthreats overneed to trust that their personal data is being the long term.
Copyright © 2017 McKinsey & Company. All rights reserved.
10
As the dangers mount, current approaches aren’t working. Cyberrisk management needs
a root-and-branch overhaul.
|
|
|---|
Paradoxically, most of the companies that fell prey to the likes of NotPetya and WannaCry would probably have said that they were well protected at the time of the attacks. Even when a company is not a primary target, it’s at risk of collateral damage from untargeted malware and attacks on widely used software and critical infrastructure. And despite all the new
defenses, companies still need about 99 days on
average to detect a covert attack. Imagine the damage an undetected attacker could do in that time.Growing complexity makes companies more
The number of vulnerable devices is increasing
dramatically. In the past, a large corporate network might have had between 50,000 and 500,000 end points; with the IoT, the system expands to millions or tens of millions of end points. Unfortunately,
many of these are older devices with inadequate
security or no security at all, and some are not even supported anymore by their maker. By 2020, the IoT may comprise as many as 30 billion devices, many of them outside corporate control. Already, smart cars, smart homes, and smart apparel are prone to malware that can conscript them for distributed denial-of-service attacks. By 2020, 46 percent of all Internet connections will be machine-to-machine, without human operators, and this number will keep growing.And of course, billions of chips have been shown to be vulnerable to Meltdown and Spectre attacks, weaknesses that must be addressed.
and incident-response processes. But what about third-party suppliers, which might be the weakest link of a company’s value chain? Or the hotshot
| 20 | 3 | |
|---|---|---|
approach that bring transparency and enable real-time risk management.
reduction and consistent coverage of their whole value chain, such as vendor risk management. The result is an inefficient system.
| |
|
| |
|---|---|---|---|
| cyberrisk on many levels. Data, infrastructure, | |||
| applications, and people are exposed to different | |||
|
|||
|
|||
To ready global companies for an age of all-encompassing connectivity, executives need a more adaptive, more thorough, and more collaborative approach to
must fine-tune business-continuity and crisis-management structures and processes to meet changes in the threat level.
| | |||
|---|---|---|---|
|
|||
| many companies distinguish between physical | |||
| |
|
||
A new posture for cybersecurity in a networked world March 2018 21
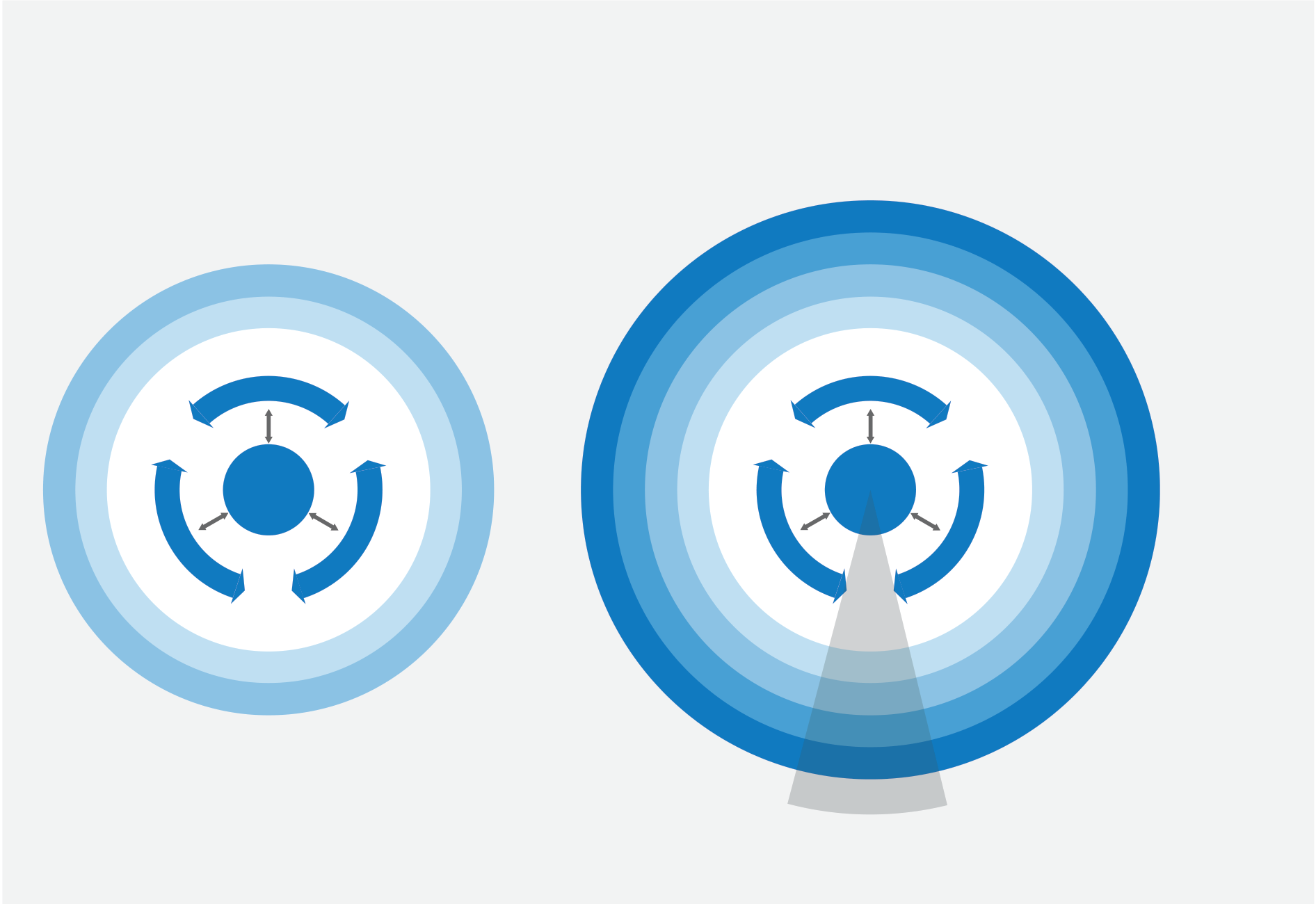
Exhibit 1 Exhibit 1 In a world where everything is connected, cybersecurity must be
comprehensive, adaptive, and collaborative.
Source: NIST; McKinsey analysis
A new posture for cybersecurity in a networked world 5
Building resilience, step by step
Successful cyberstrategies are built one step at aCybersecurity time, drawing on a comprehensive understanding of relevant business processes and the mind-set of prospective attackers. Three key steps are to prioritize assets and risks, improve controls and processes, and establish effective governance.
| People | ||
|---|---|---|
|
||
|
||
• Email, web-browser protections• Application-software security
| Applications |
|
|
|---|---|---|
Source: European Union Agency for Network and Information Security; The SANS Institute
Similarly, processes can be made more effective. The traditional focus on compliance—adhering to protocols, ticking boxes on checklists, and filing
cyberrisk. A state-of-the-art cybersecurity function should bridge the historical splits of responsibility
among physical security, information security, business continuity, and crisis management to minimize
conflicts of interest and duplication of processes. It should align its cybersecurity work with relevant
industry standards so that it can more effectively work with others to manage incidents. The organizational structure should clearly define responsibilities and relationships among corporate headquarters, regional teams, and subsidiaries. And it should establish strong architectures for data, systems, and security to ensure “security by design” and build long-term digital
resilience.
| 24 | | be led by a senior, experienced CSO with a direct | |
|---|---|---|---|
| | |||
|
|||
|
|||
| the ever-increasing number of alerts and incidents. | | be accountable for implementation of a portfolio | |
| And in a world where digital and analytical talent is | |||
| scarce, and cybersecurity skills even more so, they | |||
| | |||
|
|||
| remediation to the board and other stakeholders | |||
|
|||
|
|
|
|
| Most current security organizations are still driven | |||
| |
|
||
|
|||
| 7 | |||
McKinsey & Company 2018
Cybersecurity
1 Including forensics, intelligence, and response.
Source: McKinsey analysis
How one company built resilience
A global industrial company suffered substantial damages from a cyberattack, surprising its leaders, who had believed that its IT security processes and aby the CRO) highly standardized software architecture would not
|
|---|
McKinsey on Risk Number 5, March 2018
As companies shift to this new posture, special
thought must be given to the people who will make it happen. Ultimately, winning the war against cyberrisk is tantamount to winning the war for cybertalent.Cybersecurity functions need to attract, retain, and develop people who are nimble, innovative, and open-minded. No matter how refined the technology, it is the human factor that will win the war.
improving processes to manage vendor risk
Thomas Poppensieker is a senior partner in McKinsey’s Munich office, and Rolf Riemenschnitter is a partner in McKinsey’s Frankfurt office.
| 9 | |


J A N U A R Y 2 0 17
rotecting your critical
Top management must lead an enterprise-wide effort to find and protect critically important data, software,
world, protecting everything equally is not an option.
The digital business model is, however, entirely Our research and experience suggest that the next
in sophistication and complexity. Most large information assets. We call the approach “digital
otr Kaminski, Chris Rezek, Wolf Richter, and Marc Sorel enterprises now recognize the severity of the issue
likely to be targeted. Critical assets and sensitivity levels also vary widely across sectors. For hospital systems, for example, the most sensitive asset is typically patient information; other data such as
to operations. how the emergency room is functioning may even be
Critical risks, including the impact of various threats and the likelihood of occurrence, will be evaluated according to the dangers they pose to the business as
information that could be reconstructed a whole.
The business-back, enterprise-wide approach The key point is to start with the business problem, which requires a consideration of the whole
enterprise, and then to prioritize critical risks. This work should be conducted by an enterprise-wide team composed of key individuals from the business, including those in product development, and the cybersecurity, IT, and risk functions. The team’s main tasks are to determine which information
assets are priorities for protection, how likely it is that they will be attacked, and how to protect them.In order to function, the team must successfully engage the leaders of several domains. They need to work together to discover what is most important—no mean challenge in itself. The best way to get started is to found the team on the agreement that cyber risks will be determined and prioritized on an enterprise-wide “business back” basis. In other words, the team will first of all serve the enterprise.
The CISO must actively lead. In addition to
being a facilitator for the business’s point of view, the CISO should bring his or her own view of the company’s most important assets and risks. By actively engaging the business leaders and other stakeholders as full thought partners, the CISO will help establish the important
relationships for fully informed decision making on investments and resource allocation. The role of the CISO may thus change dramatically, and the role description and skill profile should be adjusted accordingly. Focus on how an information asset can be compromised. If an information asset is exposed by a system being breached, the
Go deeper where needed. The same level of analysis is not needed to quantify all risks.
Only for particularly high-impact or complex risks should the team invest in deeper analyses.
process, allowing focus on prioritizing risks. A flexible, scalable, and secure online application can be easy to use while managing all the inventory and mapping data, the rigorous risk and control evaluations, sector-specific methodologies, and rationales for each risk level. The platform can also support detailed data to be used when needed as the team undertakes analysis of the priority assets and gaps and makes the recommendations that will shape remediation initiatives.
In developing this approach for clients, McKinsey experts defined the following five key steps:
of assets to users, and current controls and
security measures protecting the systems
4
30 McKinsey on Risk
|
|---|
|
|---|
5
for their contributions to this article.
6
current tools are blunt instruments. A new method can yield better results.
Tucker Bailey, Brian Kolo, Karthik Rajagopalan, and David Ware
to solve it. Most prevention programs fall short either or misconduct. For these purposes, contractors and parties at their center.
by focusing exclusively on monitoring behavior or by Some leading companies are now testing a vendors are also considered employees; many of the
of safeguarding assets while also respecting can expose the company to external risks. However,
employees’ rights.
First, malicious insiders do not always seek to harm the organization. Often, they are motivated by self-interest. For example, an employee might use client information to commit fraud or identity theft, but the motive is self-enrichment rather than harm to the employer. In other cases, employees may be seeking attention, or have a “hero complex” that leads them to divulge confidential information. They might even think they are acting for the public good, but in reality they are acting for their own benefit. Understanding motive can help
companies shape their mitigation strategy.In a world of competing cyber-priorities, where needs always seem to outpace budgets, it can be tempting to underinvest in combating insider threat. The risk is not well understood, and the solution feels less tangible than in other cyber areas. Many executives have asked us, “Is this actually an important issue?
How much risk does it represent?”
| Insider |
|
Malicious |
|
Financial stress | 15 |
|---|---|---|---|---|---|
| threat |
1 Figures are approximate and may not sum, because of rounding.
Source: VERIS Community Database
In addition to being frequent, insider-threat breaches often create substantial damage. We have seen high-value events in which customer information was
stolen by both negligent and malicious insiders in financial services, healthcare, retail, and telecom in recent years. Some companies lost hundreds of millions of dollars. Pharmaceutical and medical-
products companies, as well as governments, have seen a significant rise in intellectual-property theft by malicious insiders.McK On Risk Number 6 2018
By the time negative behaviors are detected, the breach has often already occurred. The organization is already at a disadvantage, and it cannot deploy an active defense.
Monitoring for “divergence from normal behavior” creates a huge number of false positives, wasting much of the investigation team’s time.
| Exhibit 2 Exhibit 2 | |||||
|---|---|---|---|---|---|
| Typical approach | Prevention and | Event detection: | |||
| monitoring |
|
||||
analysis
| Pain points/risks | • Massive number of | • Bad behaviors can be | • Often a long backlog | |
|---|---|---|---|---|
|
|
|||
| • Huge volume of false |
|
|||
|
||||
|
|
|||
|
customized to risks,
actors, and actionsBeyond these issues, some organizations take this type of monitoring to an extreme, deploying military-grade software and conducting full-blown intelligence operations against their employees. Several recent news stories have highlighted the risks of overstepping the organization’s cultural and privacy norms. Best practices and necessary precautions in the defense industry may be seen as invasive at a bank or insurer.
Finally, to the extent that companies pursue insider threat, they often focus on malicious actors. While most cyber organizations know that negligence is an issue, many start and end their prevention efforts with half-hearted employee education and anti-phishing campaigns.
Microsegmentation
Rather than going immediately to wholesale monitoring, we believe that organizations should take a much more nuanced approach, tailored to their information assets, potential risk impacts, and workforce. The key to this approach is microsegmentation, which identifies
particular groups of employees that are capable of
doing the most damage, and then develops focused
interventions specific to those groups.To create a microsegmentation, the first step is to
understand the business capabilities or information most important to protect. Next, companies can use identity-and-access-management (IAM) records, as well as organizational and HR information, to
determine which groups and individual employees have access to those assets. These groups form the microsegments that are most important for the
program to focus on. For each segment, a company can then determine which types of insider threats are most likely to cause damage, and it can create differentiated strategies to monitor and mitigate insider events.creates a clearer understanding of risk; not all insider-threat events are created equal. Second, it allows organizations to identify a clear set of remediation actions, tailored to a particular group of employees.
While many programs focus on catching and responding to negative behaviors, it’s also vitally important to directly and assertively address the cultural issues that drive negligence and
Exhibit 3 shows an illustrative microsegmentation analysis for several kinds of information assets.
To combat negligence and co-opting, companies often conduct rudimentary cybersecurity trainings, as
well as phishing testing. Too often these focus only on behavior—educating employees on proper cyber-procedures—and miss the attitudes-and-beliefs part of the equation. Targeted interventions (such as periodic communications on cyber-impact) help employees see and feel the importance of “cyber-hygiene,” and
| Insider-threat actions they might take | |||||||||
|---|---|---|---|---|---|---|---|---|---|
| Very likely | Somewhat likely |
|
|||||||
| Employee | |||||||||
| populations | |||||||||
| Fraud/theft | Exposure | Destruction |
|
||||||
| Top assets | with access | ||||||||
Addressing the drivers of malicious behavior is an
even more personal task. The drivers vary for each
organization, and often for each microsegment. For instance, they might include personal financial stress, disgruntlement over lack of promotion, or flight risk due to poor management. Organizations that successfully address drivers of malicious behavior often begin by analyzing workforce trends (using satisfaction surveys, for example) to determine potential hot spots. They then design changes in process, governance, hiring, compensation, and so on, specific to the identified risk areas aligned to their microsegmentation strategy. For example, if an employee group has a high prevalence of “flight risks” due to disgruntlement over a manager, theorganization may require leadership coaching or even rotating the manager out of the group. If financial stress seems to be an issue, the organization may choose to provide free financial-planning help or to reevaluate its compensation model.
| Tenure |
|
Indicator: |
|
||
|---|---|---|---|---|---|
| Indicator: | |||||
|
Poor performance |
|
Bad manager | ||
| Turnover | Annual | ||||
| Rejected | |||||
| in role | internal- |
|
data | rate per | employer |
|
manager | survey | |||
which improves the anonymity of the analysis.
Microsegmented groups can be analyzed for
potential threats with reasonable precision of results. Investigations of specific individuals can be conducted only when there is reasonable suspicion of a threat and must be done in line with applicable law.DC, office, where Brian Kolo is a digital expert
and David Ware is an associate partner; Karthik
8 McKinsey on Risk Number 6, September 2018
40 McKinsey on Risk
solarseven/Getty Images
To survive in the age of advanced To survive in the age of advanced cyberthreats, use ‘active defense’
Businesses must consider themselves warned.
Rather than continue in a passive stance, organizations must adopt an “active defense” model: they should assume their firewalls will be penetrated. They should assume that encryption keys will be compromised, and that hackers will stay a step ahead of them in deploying malware in their infrastructure.
All it takes is one or two employees to
expose their credentials, and an attacker can decrypt them and make their way inside. Most organizations are not set up to thwart
|
|---|
5 Data breach digest: Perspective is reality, Verizon, 2017, verizonenterprise.com.
To survive in the age of advanced cyberthreats, use ‘active defense’ 2
of data breaches come from exploiting match that.
weak points in a company’s customer and
Shifting to an active-defense model Active defense allows organizations to engage and deflect attackers in real time by combining threat intelligence and analytics resources
within the IT function. The approach draws upon lessons the military community learned in defending itself in fluid attack environments like Afghanistan and Iraq. To ferret out and respond to risks faster, commanders began positioning operators, planners, and intelligence analysts in the same tent where they could feed special operations teams with ongoing, real-time
information. Integrated and more accurate
intelligence made it easier for units to track chatter, identify targets, and increase the6 2016 data breach investigations report, Verizon, 2016, verizonenterprise.com.
Few organizations have the budget to build
dedicated centers of this scale. But there are other ways to access needed capabilities. By realigning the existing budget, engaging outside resources, and forging information-sharing
partnerships, businesses can still mount a strong active defense. Success in doing so starts with understanding what’s involved. Here are the
central elements of an active-defense posture:• Anticipate attacks before they happen.
Anomaly-detection models work the other way around. Instead of looking for known attack signatures, they look for behavior that deviates from typical network patterns, such as an unusual spike in volume. Companies with an active-defense posture use both IDS and anomaly-defense systems to provide more comprehensive threat detection.
• Establish traps and alarms to contain attacks. Decoy servers and systems, known as deceptions, are another tool that companies can deploy as part of their active defense. Deceptions lure attackers into a dummy environment where they can
Entrance into the trap sets off an alarm, clients. Analysts informed their IT counterparts,
alerting the threat-operations center and all of whom worked together in an integrated
these environments with false information to ins for some of their high-net-worth accounts.
confuse attackers. Once intruders breach The threat center immediately activated a
the company to gather useful insights. and issued a communication to select high-
Companies can then use those repeat visits net-worth customers, encouraging them to
critical assets. Over the longer term, Knowing the core elements of an active-
businesses need to construct layers of defense model can help organizations realign
and sensitivity of those assets. Each layer structures, businesses can then determine
requires a specific key and authorization where it makes sense to acquire needed
technology spending. Otherwise, it can be change is critical. Shifting to an active-defense
tempting to try to protect everything and in posture requires leaders to recognize that
a profound difference. At one financial active-defense model must also recognize
institution, for instance, intelligence gathered that changes in traditional working practices
nature of some attacks and the prospect of state-sponsored intervention, companies
accustomed to keeping intrusion activity
closely guarded may need to open up and work more collaboratively with peers within and across their industries to share notes, best practices, and resources. Such collaboration can take place within industry associations like the Financial Services Information Sharing and Analysis Center, which shares threat
intelligence and incident information across nearly 7,000 financial-services institutions.Changes across the broader security ecosystem are also necessary. The best
Copyright © 2017 McKinsey & Company. All rights reserved.
As enterprises scale up their use of the public cloud, they must four critical practices.
rethink how they protect data and applications—and put in place four critical practices. After a long period of experimentation, leading enterprises are getting serious about adopting the public cloud at scale. Over the last several years, many companies have altered their IT strategies to shift an increasing share of their applications and data to public-cloud infrastructure and platforms.1 However, using the public cloud disrupts traditional cybersecurity2 models that many companies have built up over years. As a result, as companies make use of the public cloud, they After a long period of experimentation, leading enterprises are getting serious about adopting need to evolve their cybersecurity practices dramatically in order to consume public-cloud services the public cloud at scale. Over the last several years, many companies have altered their IT in a way that enables them both to protect critical data and to fully exploit the speed and agility that strategies to shift an increasing share of their applications and data to public-cloud infrastructure and platforms.1 However, using the public cloud disrupts traditional cybersecurity2 models that many 1 For more, see Nagendra Bommadevara, James Kaplan, and Irina Starikova, “Leaders and laggards in enterprise cloud infrastructure adoption,” companies have built up over years. As a result, as companies make use of the public cloud, they
1 For more, see Nagendra Bommadevara, James Kaplan, and Irina Starikova, “Leaders and laggards in enterprise cloud infrastructure adoption,” 1
|
47 |
|---|
While adoption of the public cloud has been limited to date, the outlook for the future is percent of their workloads in public-cloud platforms in three years, or plan to double their cloud of their workloads on public-cloud platforms; in contrast 80 percent plan to have more than 10
markedly different. Just 40 percent of the companies we studied have more than 10 percent penetration. We refer to these companies as “cloud aspirants” (Exhibit 1).3 They have concluded percent of their workloads in public-cloud platforms in three years, or plan to double their cloud
Web <2017> implementation scenarios. In some cases, using the public cloud also reduces IT operating costs.
<Public cloud> Exhibit 1 Web <2017>
Exhibit <1> of <4> <Public cloud> Exhibit 1
Exhibit <1> of <4>
Cloud aspirants: Nearly 80 percent of companies plan to have 10 percent or more of their Web <2017> Exhibit 1 <Public cloud> Exhibit <1> of <4> Exhibit 1 workloads in the public cloud or double their public-cloud use within three years. Cloud aspirants: Nearly 80 percent of companies plan to have 10 percent or more of their workloads in the public cloud or double their public-cloud use within three years.>= 2x
>= 2x
>= 2x
34
3
34
35
3
15
7
13
15
companies
17 11 20 Lorem ipsumcompanies 90 <2x <2x
40
40 20 30
Healthcare 16 Healthcare <2x Cloud skeptics: 22% 40 20 25 30 25 5 30
20
35
201Percentages may not sum to 100% due to rounding.
Source: McKinsey global cloud cybersecurity research, 2017
Interestingly, our research with chief information security officers (CISOs) highlights that they have moved beyond the question, “Is the cloud secure?” In many cases they acknowledge that cloud-service providers’ (CSPs) security resources dwarf their own, and are now asking how they can consume cloud services in a secure way, given that many of their existing security practices and architectures may be less effective in the cloud. Some on-premises controls (such as security logging) are unlikely to work for public-cloud platforms unless they are reconfigured. Adopting the public cloud can also magnify some types of risks. The speed and flexibility that cloud services provide to developers can also be used, without appropriate configuration governance, to create unprotected environments, as a number of companies have already found out to their embarrassment.
In short, companies need a proactive, systematic approach to adapting their cybersecurity capabilities for the public cloud. After years of working with large organizations on cloud cybersecurity programs and speaking with cybersecurity leaders, we believe the following four practices can help companies develop a consistent, effective approach to public-cloud cybersecurity:
|
3 | 49 |
|---|---|---|
|
The most effective approach is to reassess the company’s cybersecurity model in terms of two considerations: how the network perimeter is defined and whether application architectures need to be altered for the public cloud. The definition of the perimeter determines the topology and the boundary for the cloud-cybersecurity model. And choices regarding application architecture can guide the incorporation of security controls within the applications. These two key choices also inform one another. A company might opt, for example, to make its applications highly secure by adding security features that minimize the exposure of sensitive data while the data are being processed and making no assumptions about the security controls that are applied to a given environment.
Choosing a model for perimeter security
Among cloud aspirants, the following three models for perimeter design stand out (Exhibit 2):





