Malware Actions & Authentication Comparison Homework Answers
Your question:
Column A
Feature
A. Transport protocol
B. Authentication and authorisation
Separate
Unencrypted
Assignment Help Answers with Step-by-Step Explanation:
Malware is a broad term that encompasses various types of malicious software designed to harm or compromise computer systems and data. Two common actions that malware can perform are launching and evading. Let's differentiate between these actions using examples of malware:
1. Launch:
- Evading malware refers to the actions taken by malicious software to avoid detection or removal, allowing it to remain on a system undetected. Examples include:
- Rootkit: A rootkit is a type of malware that conceals its presence on a compromised system by modifying system files and processes. It actively evades detection by antivirus software.
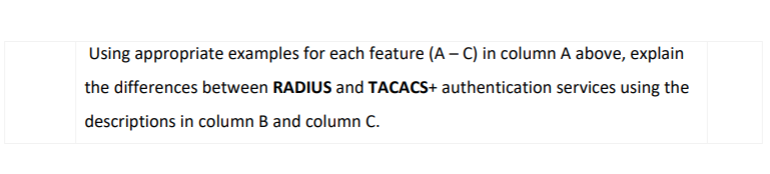
Let's examine the differences between RADIUS and TACACS+ authentication services based on the features listed in Column A:
A. Transport Protocol:
- TACACS+ employs the TCP protocol, which is connection-oriented and provides reliable data transmission. It is suitable for more complex authentication, authorization, and accounting tasks, often used in network infrastructure devices.
B. Authentication and Authorization:
- TACACS+ separates authentication and authorization, allowing for more granular control. Authentication is performed first, and then authorization decisions can be made independently. This allows for more fine-grained access control and is commonly used in environments where strict access policies are needed.
C. Communication:
- TACACS+ addresses this security concern by encrypting the communication between the client and the server, providing an additional layer of security for authentication and authorization data.
In summary, RADIUS and TACACS+ differ in transport protocols, how they handle authentication and authorization, and the level of encryption they provide. TACACS+ offers more flexibility in access control and enhanced security through encryption, making it suitable for environments with higher security requirements.





