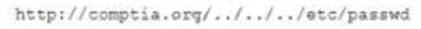Capturing visitors mac addresses and names
|
|---|
|
|---|
Containerization is a technique that creates a separate and secure space on the device for work-related data and applications. This way, personal and corporate data are isolated from each other, and IT admins can manage only the work container without affecting the user’s privacy. Containerization also allows IT admins to remotely wipe only the work container if needed, leaving the personal data intact.
Application whitelisting is a technique that allows only authorized applications to run on the device. This way, IT admins can prevent users from installing or using malicious or unapproved applications that might compromise the security of corporate data. Application whitelisting also allows IT admins to control which applications can access corporate resources, such as email servers or cloud storage.
Explanation:
Single-key or symmetric-key encryption algorithms create a fixed length of bits known as a block cipher with a secret key that the creator/sender uses to encipher data (encryption) and the receiver uses to decipher it.NEW QUESTION 3
- (Exam Topic 1)
A store receives reports that shoppers’ credit card information is being stolen. Upon further analysis, those same shoppers also withdrew money from an ATM in that store.
CompTIA Security+ Study Guide.
NEW QUESTION 4
- (Exam Topic 1)
A retail company that is launching @ new website to showcase the company’s product line and other information for online shoppers registered the following URLs:
* www companysite com* shop companysite com
* about-us companysite com contact-us. companysite com secure-logon company site com
Which of the following should the company use to secure its website if the company is concerned with convenience and cost?
|
|---|
Answer: D
Explanation:
The technique of gaining access to a dual-homed multifunction device and
then gaining shell access on another networked asset is an example of
pivoting. References: CompTIA Security+ Study Guide by Emmett Dulaney,
Chapter 8: Application, Data, and Host Security, Enumeration and
Penetration Testing
NEW QUESTION 7
- (Exam Topic 1)
A network engineer and a security engineer are discussing ways to
monitor network operations. Which of the following is the BEST
method?
A. Disable Telnet and force SSH.
B. Establish a continuous ping.
NEW QUESTION 8
- (Exam Topic 1)
A Chief Information Officer is concerned about employees using
company-issued laptops lo steal data when accessing network shares.
Which of the following should the company Implement?
A. DLP
B. CASB
C. HIDS
D. EDR
E. UEFI
Passing Certification Exams Made Easy
visit - https://www.surepassexam.com
Answer: C
Explanation:
MDM software is a type of remote asset-management software that runs from a central server. It is used by businesses to optimize the functionality and security of their mobile devices, including smartphones and tablets. It can monitor and regulate both corporate-owned and personally owned devices to the organization’s policies.The other options are not correct because:
A. Enable the remote-wiping option in the MDM software in case the phone is stolen. This option may address the company’s concern about data loss, but itmay not address the employees’ concern about personal data loss. Remote wiping can erase both work and personal data on the device, which may not be desirable for employees.
A. SSO
B. MFA
C. PKI
D. OLPAnswer: A
NEW QUESTION 11
- (Exam Topic 1)
A company reduced the area utilized in its datacenter by creating virtual networking through automation and by creating provisioning routes and rules through scripting. Which of the following does this example describe?A. laC
B. MSSP
C. Containers
D. SaaSPassing Certification Exams Made Easy
visit - https://www.surepassexam.com
Answer: C
Explanation:
To prevent such a breach in the future, the BEST control to use would be
Password complexity.
CompTIA Security+ Certification Exam
An analyst is working on an email security incident in which the target opened an attachment containing a worm. The analyst wants to implement mitigation techniques to prevent further spread. Which of the following is the BEST course of action for the analyst to take?
Explanation:
Network segmentation is the BEST course of action for the analyst to
take to prevent further spread of the worm. Network segmentation helps
to divide a network into smaller segments, isolating the infected
attachment from the rest of the network. This helps to prevent the worm
from spreading to other devices within the network. Implementing email
content filtering or DLP solution might help in preventing the email
from reaching the target or identifying the worm, respectively, but will
not stop the spread of the worm. References: CompTIA Security+ Study
Guide, Chapter 5: Securing Network Infrastructure, 5.2 Implement Network
Segmentation, pp. 286-289
NEW QUESTION 14
- (Exam Topic 1)
Which of the following is the MOST secure but LEAST expensive data
destruction method for data that is stored on hard drives?
A. HTTPS://.comptia.org, Valid from April 10 00:00:00 2021 - April 8 12:00:00 2022 B. HTTPS://app1.comptia.org, Valid from April 10 00:00:00 2021-April 8 12:00:00 2022 C. HTTPS:// app1.comptia.org, Valid from April 10 00:00:00 2021-April 8 12:00:00 2022 D. HTTPS://.comptia.org, Valid from April 10 00:00:00 2021 - April 8 12:00:00
Answer: A
Passing Certification Exams Made Easy
visit - https://www.surepassexam.com
Answer: B
Explanation:
When selecting an encryption method for data that needs to remain
confidential for a specific length of time, the longevity of the
encryption algorithm should be considered to ensure that the data
remains secure for the required period. References: CompTIA Security+
Certification Exam Objectives - 3.2 Given a scenario, use appropriate
cryptographic methods. Study Guide: Chapter 4, page 131.
Additionally, SMS messages can be compromised if a user's phone is
lost, stolen, or infected with malware. In contrast, TOTP (Time-based
One-Time Password), HOTP (HMAC-based One-Time Password), and token keys
are more secure as they rely on cryptographic algorithms or physical
devices to generate one-time use codes, which are less susceptible to
interception or unauthorized access. Reference: 1. National Institute of
Standards and Technology (NIST). (2017). Digital Identity Guidelines:
Authentication and Lifecycle
Management (NIST SP 800-63B).
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-63b.pdf
NEW QUESTION 18
- (Exam Topic 1)
A bad actor tries to persuade someone to provide financial information
over the phone in order to gain access to funds. Which of the following
types of attacks does this scenario describe?
A. Dumpster diving
B. Shoulder surfing
C. Information elicitation
D. Credential harvesting
Answer: A
visit - https://www.surepassexam.com
A. An international expansion project is currently underway.
B. Outside consultants utilize this tool to measure security
maturity.
C. The organization is expecting to process credit card
information.
D. A government regulator has requested this audit to be completed
Answer: B
Explanation:
Vulnerability scanning is a proactive security measure used to identify
vulnerabilities in the network and systems. References: CompTIA
Security+ Study Guide 701, Chapter 4
Answer: C
Explanation:
Running a vulnerability scan is the final step to be performed prior to
promoting a system to production. This allows any remaining security
issues to be identified and resolved before the system is put into
production.
To protect the company’s website from malicious web requests over SSL, a decryption certificate is needed to decrypt the SSL traffic before it reaches the WAF. This allows the WAF to inspect the traffic and filter out malicious requests.
NEW QUESTION 25
- (Exam Topic 1)
After a hardware incident, an unplanned emergency maintenance activity
was conducted to rectify the issue. Multiple alerts were generated on
the SIEM during this period of time. Which of the following BEST
explains what happened?
|
|---|
C. An error in the correlation rules triggered multiple alerts.
A. Establish chain of custody.
B. Inspect the file metadata.
NEW QUESTION 27
- (Exam Topic 1)
Which of the following BEST describes the team that acts as a referee
during a penetration-testing exercise?
A. White team
B. Purple team
C. Green team
D. Blue team
E. Red team
Answer: C
Explanation:
When hosting applications in the public cloud, there is a risk of shared
tenancy, meaning that multiple organizations are sharing the same
infrastructure. This can potentially allow one tenant to access another
tenant's data, creating a security risk. References: CompTIA Security+
Certification Exam Objectives (SY0-701)
NEW QUESTION 30
- (Exam Topic 1)
Which of the technologies is used to actively monitor for specific file
types being transmitted on the network?
Passing Certification Exams Made Easy
Answer: D
Explanation:
Data loss prevention (DLP) is a technology used to actively monitor for
specific file types being transmitted on the network. DLP solutions can
prevent the unauthorized transfer of sensitive information, such as
credit card numbers and social security numbers, by monitoring data in
motion..
NEW QUESTION 32
- (Exam Topic 1)
Which of the following uses six initial steps that provide basic control
over system security by including hardware and software inventory,
vulnerability management, and continuous monitoring to minimize risk in
all network environments?
A. ISO 27701
B. The Center for Internet Security
C. SSAE SOC 2
D. NIST Risk Management Framework
|
|---|
NEW QUESTION 33
- (Exam Topic 1)
A systems administrator is considering different backup solutions for
the IT infrastructure. The company is looking for a solution that offers
the fastest recovery time while also saving the most amount of storage
used to maintain the backups. Which of the following recovery solutions
would be the BEST option to meet these requirements?
A. Mantraps
B. Security guards
C. Video surveillance
D. Fences
E. Bollards
F. Antivirus
Answer: AB
|
|---|
A - a mantrap can trap those personnal with bad intension(preventive), and kind of same as detecting, since you will know if someone is trapped there(detective), and it can deter those personnal from approaching as well(deterrent) B - security guards can sure do the same thing as above, preventing malicious personnal from entering (preventive+deterrent), and notice those personnal as well (detective)
NEW QUESTION 36
- (Exam Topic 1)
Which of the following environment utilizes dummy data and is MOST to be
installed locally on a system that allows to be assessed directly and
modified easily wit each build?
A. Production
B. Test
C. Staging
D. Development
B. The system was quarantined for missing software updates.
C. The software was not added to the application whitelist.
NEW QUESTION 38
- (Exam Topic 1)
A security researcher is tracking an adversary by noting its attacks and
techniques based on its capabilities, infrastructure, and victims. Which
of the following is the researcher MOST likely using?
A. The Diamond Model of Intrusion Analysis
B. The Cyber Kill Chain
C. The MITRE CVE database
D. The incident response process
Passing Certification Exams Made Easy
visit - https://www.surepassexam.com
Explanation:
Identification is the first step in the incident response process, which
involves recognizing that an incident has occurred. Containment is the
second step, followed by eradication, recovery, and lessons learned.
NEW QUESTION 40
- (Exam Topic 1)
Certain users are reporting their accounts are being used to send
unauthorized emails and conduct suspicious activities. After further
investigation, a security analyst notices the following:
• All users share workstations throughout the day.
A. Brute-force
B. Keylogger
C. Dictionary
D. Rainbow
Answer: B
Explanation:
To verify that a client-server (non-web) application is sending
encrypted traffic, a security analyst can use OpenSSL. OpenSSL is a
software library that provides cryptographic functions, including
encryption and decryption, in support of various security protocols,
including SSL/TLS. It can be used to check whether a client-server
application is using encryption to protect traffic. References:
NEW QUESTION 42
- (Exam Topic 1)
A network analyst is investigating compromised corporate information.
The analyst leads to a theory that network traffic was intercepted
before being transmitted to the internet. The following output was
captured on an internal host:
Explanation:
ARP poisoning (also known as ARP spoofing) is a type of attack where an
attacker sends falsified ARP messages over a local area network to link
the attacker's MAC address with the IP address of another host on the
network. References: CompTIA Security+ Certification Exam Objectives -
2.5 Given a scenario, analyze potential indicators to determine the type
of attack. Study Guide.
NEW QUESTION 43
- (Exam Topic 1)
A company was compromised, and a security analyst discovered the
attacker was able to get access to a service account. The following logs
were discovered during the investigation:
Which of the following MOST likely would have prevented the attacker from learning the service account name?
|
|---|
NEW QUESTION 45
- (Exam Topic 1)
A junior security analyst is reviewing web server logs and identifies
the following pattern in the log file:
References: CompTIA Security+ Study Guide: Exam SY0-701, Chapter 4: Securing Application Development and Deployment, p. 191
NEW QUESTION 46
- (Exam Topic 1)
A security administrator is setting up a SIEM to help monitor for
notable events across the enterprise. Which of the following control
types does this BEST represent?
Passing Certification Exams Made Easy
visit - https://www.surepassexam.com
Answer: E
Explanation:
ISO 27001 is an international standard that outlines the requirements for an Information Security Management System (ISMS). It provides a framework for managing and protecting sensitive information using risk management processes. Acquiring an ISO 27001 certification assures customers that the organization meets security standards and follows best practices for information security management. It helps to build customer trust and confidence in the organization's ability to protect their sensitive information.A. RAT
B. PUP
C. Spyware
D. KeyloggerAnswer: C
NEW QUESTION 49
- (Exam Topic 1)
A grocery store is expressing security and reliability concerns regarding the on-site backup strategy currently being performed by locally attached disks. The main concerns are the physical security of the backup media and the durability of the data stored on these devices Which of the following is a cost-effective approach to address these concerns?A. Enhance resiliency by adding a hardware RAID.
Based on these definitions, the best option that is a cost-effective approach to address the security and reliability concerns regarding the on-site backup strategy
Increased flexibility and scalability of backup storage by choosing from various storage classes and tiers that match the performance and availability requirements of the backup data.
NEW QUESTION 50
- (Exam Topic 1)
A security architect is implementing a new email architecture for a company. Due to security concerns, the Chief Information Security Officer would like the new architecture to support email encryption, as well as provide for digital signatures. Which of the following should the architect implement?
visit - https://www.surepassexam.com
|
|---|
CompTIA Security+ Study Guide, Sixth Edition (SY0-701),
Guards are physical security personnel who monitor and control access to a facility. Guards can prevent unauthorized or malicious individuals from entering a facility and plugging in a remotely accessible device.
NEW QUESTION 52
- (Exam Topic 1)
Which of the following are the MOST likely vectors for the unauthorized
inclusion of vulnerable code in a software company’s final software
releases? (Select TWO.)
A. A service-level agreement
B. A business partnership agreement
C. A SOC 2 Type 2 report
D. A memorandum of understanding
Answer: C
A. Page files
B. Event logs
C. RAM
D. Cache
E. Stored files
F. HDD
Passing Certification Exams Made Easy
Explanation:
In a forensic investigation, volatile data should be collected first, based on the order of volatility. RAM and Cache are examples of volatile data. References: CompTIA Security+ Study Guide 701.NEW QUESTION 55
- (Exam Topic 1)
The security team received a report of copyright infringement from the IP space of the corporate network. The report provided a precise time stamp for the incident as well as the name of the copyrighted files. The analyst has been tasked with determining the infringing source machine and instructed to implement measures to prevent such incidents from occurring again. Which of the following is MOST capable of accomplishing both tasks?NEW QUESTION 56
- (Exam Topic 1)
During a security assessment, a security finds a file with overly permissive permissions. Which of the following tools will allow the analyst to reduce the permission for the existing users and groups and remove the set-user-ID from the file?A. 1s
B. chflags
C. chmod
D. lsof
E. setuid
A. Vulnerabilities with a CVSS score greater than 6.9.
B. Critical infrastructure vulnerabilities on non-IP protocols.
NEW QUESTION 58
- (Exam Topic 1)
Which of the following describes a maintenance metric that measures the average time required to troubleshoot and restore failed equipment?A. RTO
B. MTBF
C. MTTR
D. RPO
visit - https://www.surepassexam.com
If the help desk has received calls from users in multiple locations who are unable to access core network services, it could indicate that a network outage or a denial-of-service attack has occurred. The network team has identified and turned off the network switches using remote commands, which could be a containment measure to isolate the affected devices and prevent further damage.
The next action that the network team should take is to initiate the organization’s incident response plan, which would involve notifying the appropriate stakeholders, such as management, security team, legal team, etc., and following the predefined steps to investigate, analyze, document, and resolve the incident.
According to CompTIA Security+ SY0-701 Exam Objectives 1.5 Given a scenario, analyze indicators of compromise and determine the type of malware:“An incident response plan is a set of procedures and guidelines that defines how an organization should respond to a security incident. An incident response plan typically includes the following phases: preparation, identification, containment, eradication, recovery, and lessons learned.”
NEW QUESTION 60
- (Exam Topic 1)
A company is required to continue using legacy software to support a
critical service. Which of the following BEST explains a risk of this
practice?
A. Cellular
B. NFC
C. Wi-Fi
D. Bluetooth
Answer: B
Explanation:
A Raspberry Pi device connected to an Ethernet port could be configured
as a rogue access point, allowing an attacker to intercept and analyze
network traffic or perform other malicious activities. References:
CompTIA Security+ SY0-701 Exam Objectives: Given a scenario, implement
secure network architecture concepts.
NEW QUESTION 63
- (Exam Topic 1)
A security engineer is reviewing the logs from a SAML application that
is configured to use MFA, during this review the engineer notices a high
volume of successful logins that did not require MFA from users who were
traveling internationally. The application, which can be accessed
without a VPB, has a policy that allows time-based tokens to be
generated. Users who changed locations should be required to
reauthenticate but have been Which of the following statements BEST
explains the issue?
A. OpenID is mandatory to make the MFA requirements work
B. An incorrect browser has been detected by the SAML application
C. The access device has a trusted certificate installed that is
overwriting the session token D. The user’s IP address is changing
between logins, bur the application is not invalidating the token
Answer: D
SMB uses TCP port 139 and 445. Blocking these ports will prevent external attackers from exploiting the vulnerability in SMB protocol on Windows systems. Blocking TCP ports 139 and 445 for all external inbound connections to the DMZ can help protect the servers, as these ports are used by SMB protocol. Port 135 is also associated with SMB, but it is not commonly used. Ports 143 and 161 are associated with other protocols and services.
NEW QUESTION 65
- (Exam Topic 1)
Which of the following involves the inclusion of code in the main
codebase as soon as it is written?
A. Data custodian
B. Data owner
C. Data protection officer
D. Data controller
Answer: C
B. Data owner is a role that determines the classification and usage of data within an organization. A data owner does not have direct access to the seniormanagement team, as they are more involved in business functions than data protection compliance.
D. Data controller is a role that determines the purposes and means of processing personal data within an organization. A data controller does not have directaccess to the senior management team, as they are more involved in data processing activities than data protection oversight.
|
|---|
A. Phishing
B. Vishing
C. Smishing
D. Spam
Answer: C
Answer: B
Explanation:
To determine the total risk an organization can bear, a technician
should review the organization's risk tolerance, which is the amount of
risk the organization is willing to accept. This information will help
determine the organization's "cloud-first" adoption strategy.
References: CompTIA Security+ Certification Exam Objectives
(SY0-701)
NEW QUESTION 71
- (Exam Topic 1)
The Chief Information Security Officer (CISO) has decided to reorganize
security staff to concentrate on incident response and to outsource
outbound Internet URL categorization and filtering to an outside
company. Additionally, the CISO would like this solution to provide the
same protections even when a company laptop or mobile device is away
from a home office. Which of the following should the CISO choose?
A. CASB
B. Next-generation SWG
C. NGFW
D. Web-application firewallAnswer: B
A. Authentication protocol
B. Encryption type
C. WAP placement
D. VPN configurationAnswer: C
Security: WAP placement determines how vulnerable wireless devices are to eavesdropping or hacking attacks from outside or inside sources. WAPs should be placed in locations that minimize exposure to unauthorized access and maximize encryption and authentication methods.
NEW QUESTION 73
- (Exam Topic 1)
Hackers recently attacked a company's network and obtained several unfavorable pictures from the Chief Executive Officer's workstation. The hackers are threatening to send the images to the press if a ransom is not paid. Which of the following is impacted the MOST?A. SLA
B. BPA
C. NDA
D. MOUAnswer: A
visit - https://www.surepassexam.com
• The account was accessed from a hostile, foreign nation, but the employee has never traveled to any other countries.
Which of the following can be implemented to prevent these issues from reoccuring? (Select TWO)
NEW QUESTION 77
- (Exam Topic 1)
The Chief Technology Officer of a local college would like visitors to
utilize the school's WiFi but must be able to associate potential
malicious activity to a specific person. Which of the following would
BEST allow this objective to be met?
A. Requiring all new, on-site visitors to configure their devices to
use WPS
B. Implementing a new SSID for every event hosted by the college that
has visitors C. Creating a unique PSK for every visitor when they arrive
at the reception area D. Deploying a captive portal to capture visitors'
MAC addresses and names
Answer: A
Explanation:
Based on these definitions, the best security solution to mitigate the
risk of future data disclosures from a laptop would be FDE. FDE would
prevent unauthorized access to the data stored on the laptop even if it
is stolen or lost. FDE can also use TPM to store the encryption key and
ensure that only trusted software can decrypt the data. HIDS and VPN are
not directly related to data encryption, but they can provide additional
security benefits by detecting intrusions and protecting network traffic
respectively.