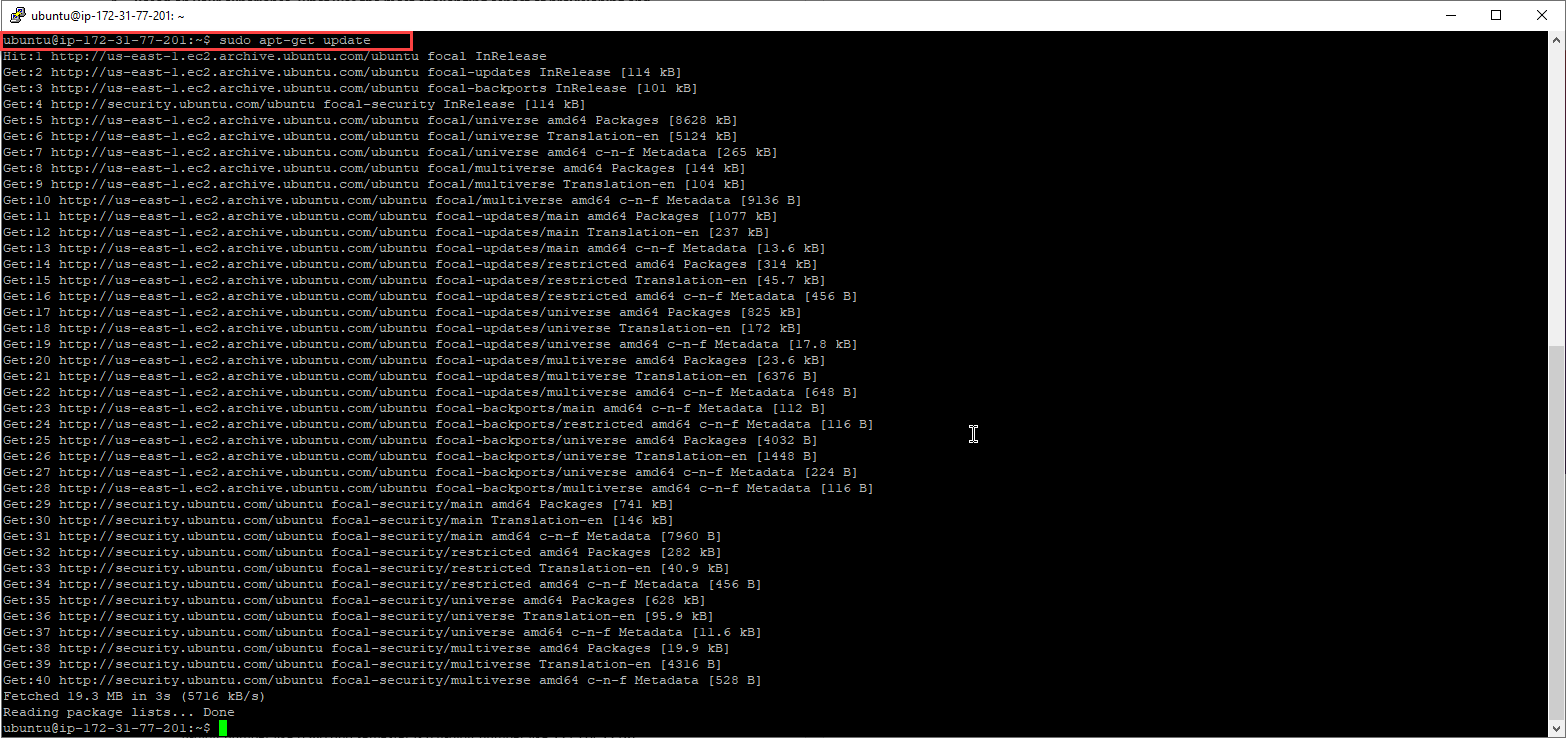
And update the ubuntu server using sudo apt-get update and sudo apt-get upgrade
Week 1 Project Template Godfred Onnomah
CMIT 495 Current Trends and Projects in Computer Networks and Security
2. Provide a detailed overview of the steps required to provision (create) and launch an AWS
Ubuntu-based server virtual instance. The steps may be listed in bullet points or complete
Export/print your completed file as a PDF and upload to your LEO/Assignments folder.
|
Godfred Onnomah |
|---|
Export/print your completed file as a PDF and upload to your LEO/Assignments folder.
Export/print your completed file as a PDF and upload to your LEO/Assignments folder.
|
Godfred Onnomah |
|---|
The benefits of virtualization in disaster recovery are to consider quicker recuperation of IT resources that accommodate improved business revenue and continuity. The more seasoned frameworks are unequipped for recuperating inside a couple of hours, and by and large, organizations experience any longer downtime, which brings about income misfortune.
Easier IT management:
Export/print your completed file as a PDF and upload to your LEO/Assignments folder.
1 Link: https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html
The apt-get update command on the Ubuntu server, when entered, will return a large amount of information from the internet about the packages and the updates that could be suggested. This command should be one of the first commands that a user runs in any Linux/Ubuntu system after a new installation. There are three different lines that are returned after running the apt-get update command. The lines start with either hit, in, or get. The hit line shows the user that there is no change in the package version. The in line is showing the user of the system that the package is being ignored for various reasons. The get line tells the user that there is a new version of the package available and will download the information onto the server, but not the package itself. Not only should a user run the apt-get update command after a new installation, as an organization, it should be performed weekly to ensure the system is up to date. The apt-get upgrade command within the Ubuntu server will be used when an upgrade to a package is needed. This can be used to upgrade the packages that the apt-get update command
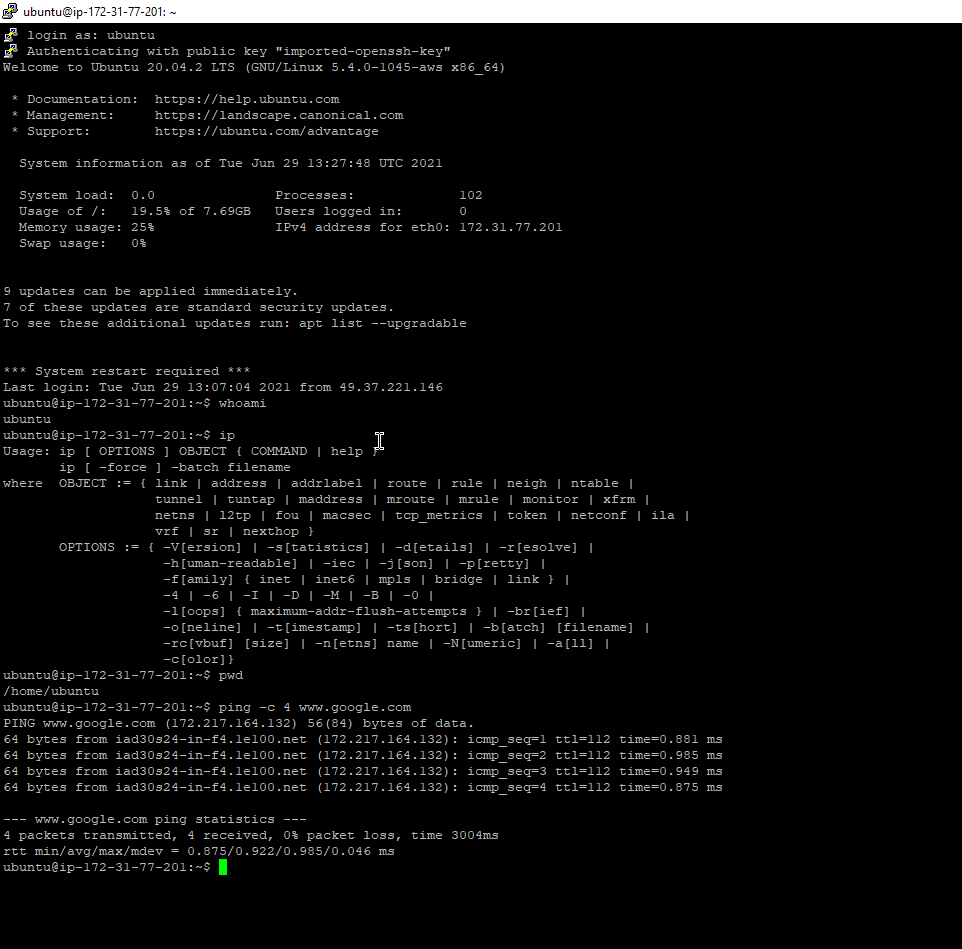
downloaded the information for. The apt-get upgrade command is the most convenient manner used to upgrade any and all packages in need of an upgrade within the system This command does not remove any packages that are already installed, it just updates the ones that are already there and ready to be upgraded. The apt-get upgrade command should be executed after the apt-get update command to install the proper upgrades to the system.8. After successfully deploying the Ubuntu Server operating system updates and upgrades, reconnect to the AWS EC2 console, and if needed login again via an SSH client (Note: SSH session inactivity timeout is short). Instructions to SSH are provided by Amazon on how to do so. When connected, run the following commands to obtain information about the host and network settings (perform a screen capture of the results and embed below):
9. What kind of account did you discover when you ran the whoami command? How do you know?
Week 1 Project Template Godfred Onnomah
191.255.255.254; Class C includes 192.0.1.1 – 223.255.255.254 (Computer Hope, 2019). Class D IP addresses are reserved for multicast groups and include the range 224.0.0.0 –
239.255.255.255 (Computer Hope, 2019). Finally, Class E addresses are reserved for future use, or research and development purposes and include the range Ubuntu virtual server, I received the IP address of 172.31.37.39. When I checked my own IP address on my laptop, I received and IP address of 192.168.0.24. Both of these IP addresses are private, but they are within different IP address classes. The Ubuntu server is within Class B and my computer is within Class C. IP addresses are used to identify the source and destination of any transmitted information within the Internet Protocol. Public IP addresses are assigned by an Internet Service Provider to mostly organizations and are globally unique within the internet. Private IP addresses are not connected to the internet which allows different private devices within different networks to maintain the same IP address. While public IP addresses can be accessed through the internet, private IP addresses cannot. Private IP addresses range from 10.0.0.0 to 10.255.255.255, 172.16.0.0 to 172.31.255.255, and 192.168.0.0 to 192.168.255.255. The other IP addresses can be used for public IP’s. Public IP addresses are also managed by an organization called the Internet Assigned Numbers Authority which ensures that no two public internet domains contain the same address. Private IP addresses to not have a central body of management, but are managed by the administrator of the assigned private network.the organization refreshing developer laptops and desktops, given the following information
and constraints.
| ○ |
|
|
|---|---|---|
|
||
laptop costs $48.60 to run for a year, and each desktop costs $289.50 to run for a year.● Consider all the aforementioned expenses the organization incurs when making your
recommendation and be sure to show your work.
an AWS Linux virtual machine.
● Using the , calculate the cost to meet the organizational
The electricity cost of 65 Desktops: $18,817.50
Miscellaneous (replacement parts, etc.): 10,000
Export/print your completed file as a PDF and upload to your LEO/Assignments folder.
Week 1 Project Template Godfred Onnomah
Type 1 hypervisors tend to be more secure than type 2 hypervisors. Type 2 hypervisors are basically treated like applications because they install on top of a server’s operating system which allows them to be exposed to any vulnerabilities that may exist on the operating system.
They also require a way to share folders and other user information between hosts and a guest operating system which increases the risk of hacking and spreading of malicious codes. On the other hand, type 1 hypervisors provide an abstract layer between hardware and virtual machines which allows for increased security because they do not have to deal with an underlying operating system. Bare-metal hypervisors tend to be much smaller than user-space hypervisors which makes them more manageable concerning vulnerabilities.