And business resumption planning auerbach publications
Commerce is blossoming on the Internet. Waiting until there is a revenue impact after a failure resigns an organization to be almost perpetually in the reactive mode of trying to keep up with the protection of a potentially business debilitating system. The alternative is to start now, while these systems are still relatively immature and design the protective systems in before the Internet becomes a fully functional business system.
Leo A. Wrobel is president and CEO of Premiere Network Services, Inc., in DeSoto, TX. An active author, national and international lecturer, and technical futurist, he has published 10 books and over 100 trade articles on a variety of technical subjects, including Writing Disaster Recovery Plans for Telecommunications and LANS (Artech House, 1993) and Business Resumption Planning (Auerbach Publications, 1997). His experience of nearly two decades includes assignments at AT&T, a major mortgage banking company, and a host of other firms engaged in banking, brokerage, heavy manufacturing, telecommunications services and government, as well as the design and regulatory approval of a LATA-wide OC-12/ATM network for a $10 billion manufacturing giant, the first of its kind. A three-term city councilman and previous mayor, Leo Wrobel is a knowledgeable and effective communi-cator known for his enwide variety of technical topics. For more information, contact his web site ator phone at (972) 228-8881.
Introduction
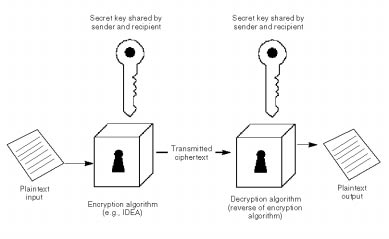
Users who rely on electronic mail for business or personal communications should beware. Messages sent over a network are subject to eavesdropping.If the messages are stored in a file, they are subject to perusal months or even years later. There is also the threat of impersonation and that a message may not be from the party it claims to be from.
· · · |
|
|---|
E-Mail Risks
PGP provides protection from the threat of eavesdropping. A message sent over the Internet can pass through a handful of mail forwarders and dozens of packet-switching nodes. A systems administrator or someone who has gained privileged access to any of these transfer points is in a position to read those messages.
Authenticity of messages poses another potential risk. It is not difficult to spoof the network into sending a message with an incorrect return address, enabling impersonation. It is also relatively easy to trap a message along its path, alter the contents, and then send it on its way.
For example, if a user is on a shared system, such as a UNIX system,
that hooks into the Internet, then the impersonator could be someone
with “superuser” privileges on the system. Such a person could divert
all incoming and outgoing traffic from an
unsuspecting mailbox to a special file. The impersonator could also have
access to a router, mail bridge, or other type of gateway through which
all traffic between the user and a correspondent must pass. Such
impersonators could use their privileged status on the gateway to
intercept mail and to create and send mail with a fraudulent return
address.
· Integrating these algorithms into a general-purpose application that is independent of the operating system and processor and that is based on a small set of easy-to-use commands.
· Making the package and its documentation, including the source code, free and widely available.
© 2004 by CRC Press LLC
A new release of PGP, known as version 2.6, which was developed at MIT with the supervision of Phil Zimmermann, has patent approval from the RSA patent holders. Like the original PGP, this version has also made its way onto bulletin boards and Internet sites outside the US. In addition, a compatible non-US version 2.6was created outside the US. As long as a user chooses any of the flavors of version 2.6, there is no infringement on any patents.
| · · · · · |
|
|---|
cipher: phhw ph diwhu wkh wrjd sduwb
The alphabet is wrapped around so that the letter following Z is A. The decryption algorithm simply takes the ciphertext and replaces each letter with the letter standing three places earlier on in the alphabet. A general Caesar cipher involves a shift of k letters, where k ranges from 1 through 25. In this case, k is the secret key to the algorithm.
© 2004 by CRC Press LLC





