2.2 how to control potential threats and vulnerabilities
Security Policy Development for Appliance Online
Name of the Student:
Table of Contents
2. Information security policies 3
1. Introduction
2. Information security policies
2.1 How to develop information security policies
Information security policies play a crucial role in securing the organizational data and confidential information within the organization. It is essential to keep secure all the reliable information about the organization and its employees for minimizing the risk factors due to the lack of a proper security system. Some security policies should be implemented in the organization Appliance online for minimizing the risk factors in the organization.
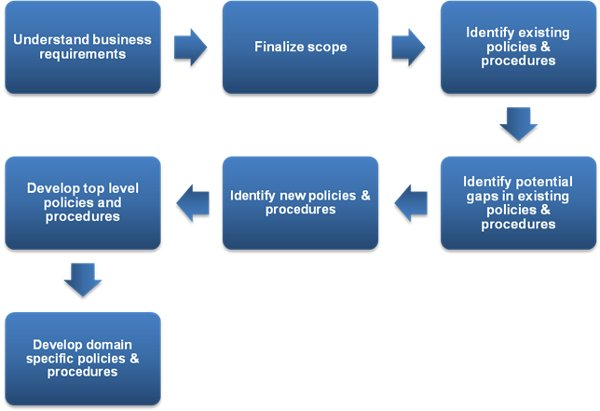
Identifying the policies and procedures: The existing policies and procedures of the organization should be identified by the security policies for developing the quality of the business. The lacking factors would also be detected through this identification process, and required security tools would be implemented in Appliance online company for having a better result. New security policies would meet all the criteria of the business in terms of achieving a remarkable position in the global market.
Identifying potential gaps in the existing policies and procedures: After identifying the existing policies and procedures, the company Appliance online would be able to detect the lacking factors. The factors that were responsible for potential gaps in the security system. After that, the organization Appliance online could take action against the gaps and implement some new policies for developing the quality of the business.
2.2 How to control potential threats and vulnerabilities
(Source:Safa& Von Solms, 2016, pp-75)
The first step of controlling potential threats and vulnerabilities in an organization is to identify the risks factors that can harm the security policies of the organization. On the other hand, vulnerabilities indicate to the imperfection of the security system within the organization. Loss or harm could result for the vulnerabilities in the security system. Threat factors are the computing systems that contain the potential risk factors for the loss of the organization (Flowerday&Tuyikeze, 2016). The company Appliance online can think about monitoring the organizational activities to identify the harmful risk factors. Some strategies can be followed to minimize the potential threat factors within the organization:
Update the required tools: A healthy security system needs a regular update of the technological tools for developing the security department of the organization (Moody, Siponen&Pahnila, 2018). Appliance online company would require to detect the faults of the existing tools and update them as per the requirements. The devices would be secured with authentication for confirming the security of the organization. Vulnerability in a security system means the lack of proper technological support in the security system. Updating the required tools would fulfil the criteria of the security purpose of Appliance online (Moody, Siponen&Pahnila, 2018).
2.3 Plan for business continuity with technological change
Business continuity plan includes the process of creating a technical system that would protect the secured data and reduce the potential threat factors to the organization named Appliance online (Peltier, 2016). The method determines the protection and security of the online functions and activities of an organization. Technology has been improved day by day, and it had a practical positive impact on the business continuation process. IBM cloud data recovery process can be implemented by the management authority of the Appliance online (Hsu, Shih, Hung & Lowry, 2015).
Information security policy: Information security policy would secure the confidential data of Appliance online in terms of continuing the business. Required updates of the existing versions of the security systems would be done by the information security policies of the organization (Safa, Von Solms&Furnell, 2016).
3. Information systems for Ethical and Legal Compliance Framework
Ethical and Legal variables provide a significant role in making adjustments in the midst of business processes within the organisation-appliance Online. These specific elements are to be considered with resource planning priorities and appropriate management in order to overcome the unfavourable circumstances that generally arise suddenly. Proper consideration of ethical and legal issues gets adequate solutions in this specific subject of debating. Within the mentioned sub and distended evaluation get given for the identified points listed concerning the two different kinds of the account needed to comprehend the circumstances that may arise. It is optimistic that, developing policy for the risk mitigation of the chosen organisation – Appliance Online.
After a period of a vast regulation, different kinds of organisations have seen to face the rapid growth regarding the recent laws. The standards and rules are considered for increasing complexity. As a result, an enormous effect on the way of conducting their daily legal ethics and includes the non-similar changes in the chosen organisation along with their governance structures. The other factors, such as software systems and communication flow, would implement its corporate culture and organisational authority (Anderson, Christ, Dekker &Sedatole, 2015).
Figure 5: Framework of Information Systems for Legal Compliances
4. Conclusion
5. Recommendations
Analysing the Ethical and legal Framework, it can be said that the specific solutions are needed in the areas of some ethical issues. These problems are linked to the application of an information system within the chosen organisation. The recommendations are as follows:
The major ethical issue is connected with the not proper transaction of the financial department of the organisation –‘Appliances online’. Improper prohibition based on the consumer side stimulates the service of the commercial department. As a solution, it can be recommended that hiring the individual security experts and the 'Information Technology Management' would make a digital implication (Safa, Von Solms&Furnell, 2016). It is optimistic that the hierarchal authority would be beneficial regarding the business procedures of the 'Appliances Online'.
References
Journal Articles
Badwan, J. J., Al Shobaki, M. J., Naser, S. S. A., &Amuna, Y. M. A.(2017). Adopting technology for customer relationship management in higher educational institutions. International Journal of Engineering and Information Systems (IJEAIS), 1(1), 20-28. https://hal.archives-ouvertes.fr/hal-01500365
Hsu, J. S. C., Shih, S. P., Hung, Y. W., & Lowry, P. B. (2015). The role of extra-role behaviors and social controls in information security policy effectiveness. Information Systems Research, 26(2), 282-300.
Yazdanmehr, A., & Wang, J. (2016). Employees' information security policy compliance: A norm activation perspective. Decision Support Systems, 92, 36-46.
Wang, M., Zhu, L., & Zhang, Z. (2016). Risk-aware intermediate dataset backup strategy in cloud-based data intensive workflows. Future Generation Computer Systems, 55, 524-533.
Darwazeh, N. S., Al-Qassas, R. S., &AlDosari, F. (2015). A secure cloud computing model based on data classification. Procedia Computer Science, 52, 1153-1158.
Lehnert, K., Craft, J., Singh, N., & Park, Y. H. (2016). The human experience of ethics: A review of a decade of qualitative ethical decision‐making research. Business ethics: A European Review, 25(4), 498-537. https://doi.org/10.1111/beer.12129





