Digital Forensic
MN 624 Part 1B
Section 1: Data Preparation:
Excel file:
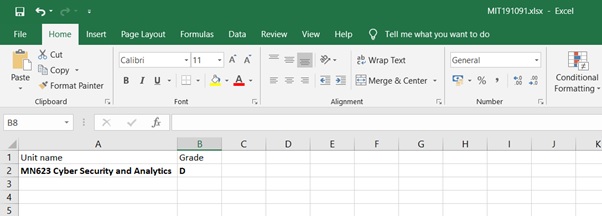
Files in USB:
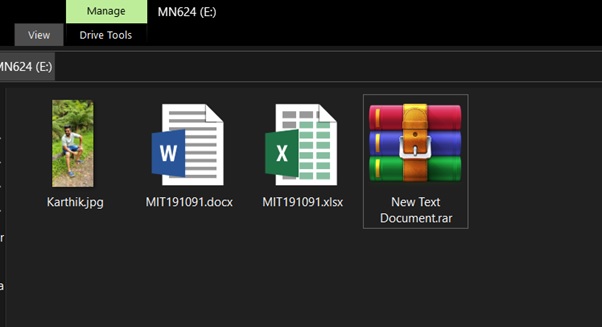
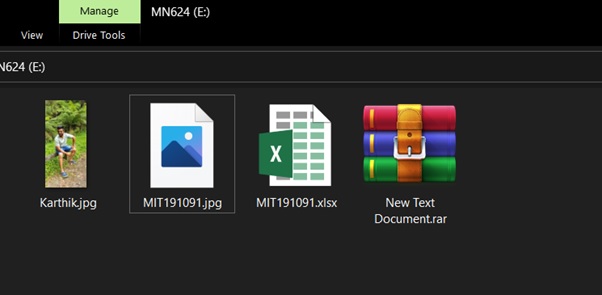
Changing extension of doc file:
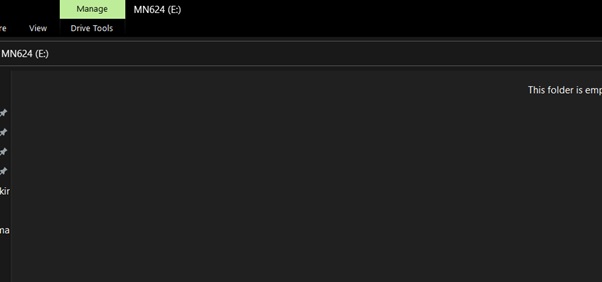
All files deleted:
Section 2: Data Acquisition:
The USB drive will be acquired in this part. For acquiring the drive Bit stream copy will be used. Bit stream copy in digital forensics can be defined as a bit by bit copy of the original storage medium that seems as an exact duplication of the original disc. It has difference to a simple backup copy as the files that can be copied after backups, are stored in a folder or a known file type. There is a file by which the bit stream copy of all the data on a disk or disk partition can be contained. A bit-stream image consists actually a set of files that can be used for creating an exact copy of a hard drive as well as to preserve all latent data in addition to the files and directory structures.
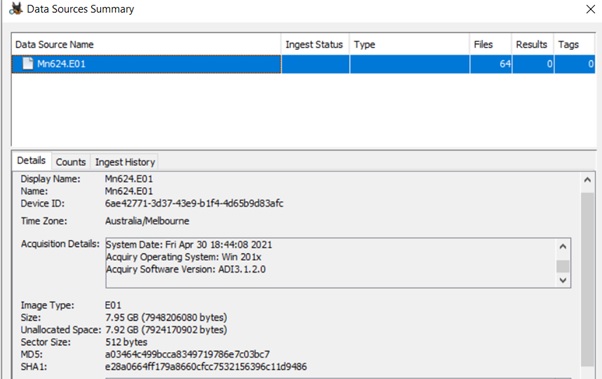
Acquiring the USB drive using FTK:
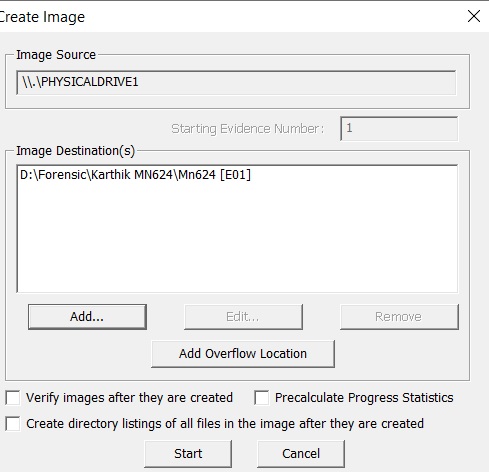
USB has been acquired:
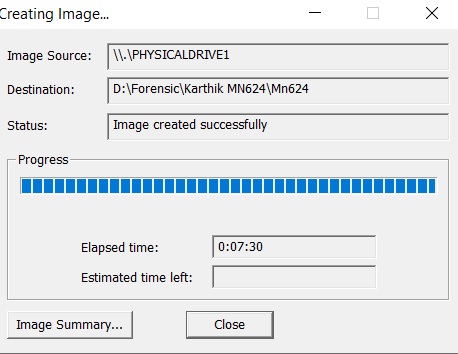
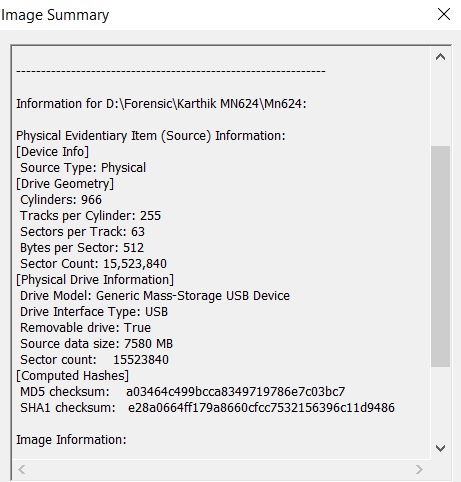
Hash value:]
Section 3: Data Recovery:
Data recovery is basically a technique to recover the data from any digital device is being damaged of effected. If any device is damaged like the hard disk is badly damaged because of fire or water and a compact disk surfaces got as scratched or a USB port might be physically damaged then the data recovery process can help but in that cases the process might it expensive some times. Most of the time the media which is not assemble or the damaged part repair of a media is recovered by the data recovery process. The irretrievable data (might happen because of data corruption) can be retrieve by the data recovery technique. By data recovery technique the software failure like software corruption, damage or corruption of any configuration, any issues with the Microsoft server or in SQL can be solved very easily and use as a evidence in court. Recovering a valid data is very help for a complex case because it can give an actual conclusion to the case and help in prosecutions. Forensics data recovery can be a forensic process by which the data is extracted from the damaged or corrupted evidence sources by using a forensically sound manner. This method of recovering data has the meaning that is what any evidence resulting from it can later be relied on in a court of law. This recovery process seems quite expensive. The disassembly of the media in which hard drives in special “clean rooms, is included that can be involved by the process of data recovery from damaged media and repairing of damaged parts is done. Sometimes, the data has be damaged or corrupted and that data has become irretrievable by the user that can also be found as well as retrieved by the experts of the data recovery. Data recovery in digital forensics has some importance as it requires for the identification of the exact digital material that could be destroyed or comprised during the time of incident. Now a days the process of data recovery has become an important part. It has come into its existence in the scenarios like the data storage devices could be destroyed or damaged by the convict or the data can be deleted or formatted or inaccessible.
Creating new case in Autopsy:
Adding evidence Item:
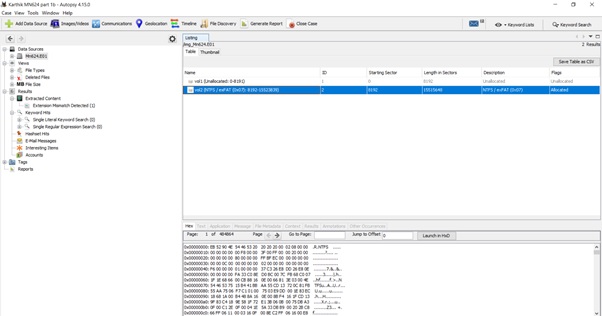
Deleted files recovered:
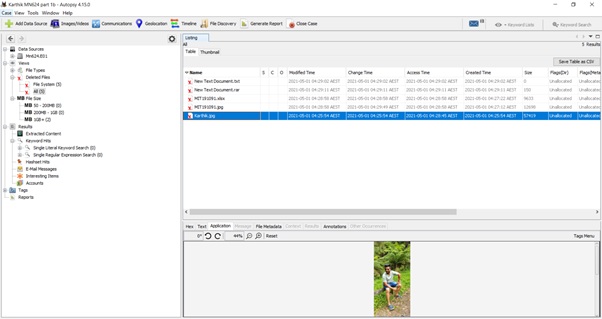
Section 4: Data Analysis:
Data analysis can be considered as an analysis process of data in digital forensic by which structured data with regard to incidents of financial crime is examined. The mail purpose of this process is to discover and analyze patterns of fraudulent activities. The analysis team performs the analysis of large volumes of data in a separate database by using a typical manner.
Forensic digital analysis can be considered as the in-depth analysis and examination of electronically stored information (ESI), that has the purpose behind it, is to work for identifying information by which the matters in a civil or criminal investigation and court proceeding may be supported or contested. The forensic analysis has the ultimate goal that it is imperative that the evidence that is electronically stored can be treated with great care. All these evidences should have to be preserved and there is nothing to be done as a result that may have the chance to alter the ESI while the analysis process is going on. This is the reason behind it is that the best legal result will be obtained by analyzing a forensic image or copy of the device.
From the hash value it can be seen that the extension was changed:
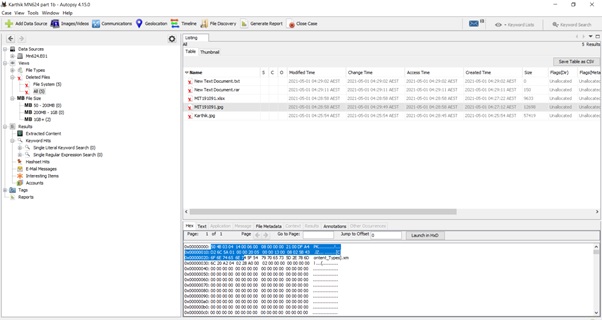
Encryption detected:
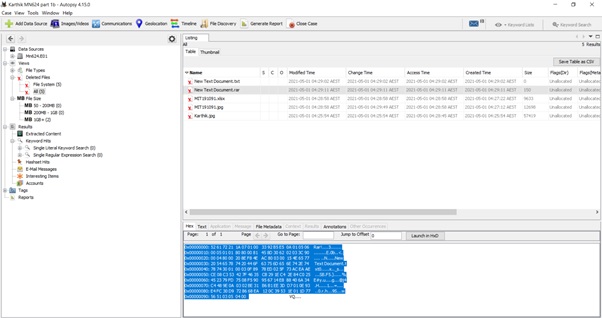
Section 5: Data Validation:
Before presenting any data in the court it is important to check the data integrity. Mainly forensic tools offer hashing of image files as an example after loading any image file in Pro-Discover it calculates the hash of the first acquired original image and then compare it with the hash value which it runs.
By using hexadecimal editors an actual data can be found. An original evidence can be hidden in the internet or in the device with an anonymous name so then by hashing the specific file or sector the actual valid data can be found and can be present in the court as a valid evidence. So, by calculating hash value the actual data can be founded. A data validation is the conformation which an examiner got after examine the evidence by using appropriate tools, technique and procedure to check if the evidence is reliable or not and if the data is not correct or valid then it will not be accepted in the court.
Hash value of the Image file is matched with the acquired data:
Section 4: Comparison of the digital forensics tools:
FTK is a forensic toolkit which is made by Access data basically a computer forensic software. It can retrieve the delete mails, also by scanning the disk it can get the text string and which can be use as a password dictionary to decode an encryption.
SLEUTH KIT autopsy is a combination of data which are extracting from any disk drives and many other storages and this all must be based on library and Unix and windows collection. By using command line the sleuth kit can be use, or as a library file which can be combined with the digital forensic tool separately.
Autopsy sleuth kit can be considered as a graphical interface by which keyword searching, case management and image integrity and other automated operations can be provided where as FTK (Forensics Tool Kit) can be considered as a computer forensics software by which a hard drive is scanned in order to look for various information.
References:
- Amerini, Irene, Chang-Tsun Li, Nasir Memon, and Jiwu Huang. "IEEE Access Special Section: Digital Forensics Through Multimedia Source Inference." IEEE Access8 (2020): 209657-209659.
- Caviglione, Luca, Steffen Wendzel, and Wojciech Mazurczyk. "The future of digital forensics: Challenges and the road ahead." IEEE Security & Privacy15, no. 6 (2017): 12-17.
- Al-Jadir, Ibraheem, Kok Wai Wong, Chun Che Fung, and Hong Xie. "Enhancing digital forensic analysis using memetic algorithm feature selection method for document clustering." In 2018 IEEE International Conference on Systems, Man, and Cybernetics (SMC), pp. 3673-3678. IEEE, 2018.
- Al-Jadir, Ibraheem, Kok Wai Wong, Chun Che Fung, and Hong Xie. "Enhancing digital forensic analysis using memetic algorithm feature selection method for document clustering." In 2018 IEEE International Conference on Systems, Man, and Cybernetics (SMC), pp. 3673-3678. IEEE, 2018.
- Babiker, Mohammed, Enis Karaarslan, and Yasar Hoscan. "Web application attack detection and forensics: A survey." In 2018 6th International Symposium on Digital Forensic and Security (ISDFS), pp. 1-6. IEEE, 2018.
- Gill, Navpreet Kaur, Ruhi Garg, and Er Amit Doegar. "A review paper on digital image forgery detection techniques." In 2017 8th International Conference on Computing, Communication and Networking Technologies (ICCCNT), pp. 1-7. IEEE, 2017.
- Kwon, Sungmoon, Jaehan Jeong, and Taeshik Shon. "Digital Forensic Readiness for Financial Network." In 2019 International Conference on Platform Technology and Service (PlatCon), pp. 1-4. IEEE, 2019.
- Naqvi, Syed, Peter Sommer, and Mark Josephs. "A Research-Led Practice-Driven Digital Forensic Curriculum to Train Next Generation of Cyber Firefighters." In 2019 IEEE Global Engineering Education Conference (EDUCON), pp. 1204-1211. IEEE, 2019.


