Cyberspace and Cybercrime Sample Assignment
Introduction
A recent study introduced by Norton presented some staggering statistics on cybercrime. Almost 65% of the users of internet all over the world fall prey to this crime. The major crimes that web surfers are suffering from are computer viruses, identity theft, credit card frauds etc. In the list of victimized countries, china ranks first with 83% share followed by India and Brazil with 76% and America on third rank with 73%.
Cyber-crime can be defined as the crimes that are committed through internet with the use of computer as a tool or as a victim (PARODI, 2013). It has been realized by the governments and police departments of the world that cyber-crime has a great potential to cause huge damage to the society so they have started to respond. There are several forms of cyber-crime today such as crime caused to individual, against personal property, crime damage to society or groups. The consequences have to be tolerated by the society, despite of any form of the crime. This paper highlights and investigate the scenario of cyber-crime, its impact on society and individual lives, different types of crime with real case studies along with the challenges it pose in preventing cybercrime. Developments in the area of information technology and innovations have given rise to the concept of cybercrime, thus, giving IT the major role in preventing the effects of such crimes. The research will discuss few techniques developed in order to prevent cyber-crimes (Leukfeldt, Lavorgna and Kleemans, 2016). Today, it has become an issue of global concern due to the quantum of harm it can cause; ways are being found out to regulate such crimes effectively.
The internet arena has become a world parallel to the present living. Today life is not possible without the use of internet. It has become a necessity. It has benefitted the human kind with making us capable of communicating through websites and emails and applications. We cannot deny the importance of virtual space we have been using but on the other side we cannot even question the threats and side effects of the same. It is correctly mentioned that benefit comes with an expense. Crime today stays vague but hides behind the face of innovation. Cybercrime affects social life of the population with huge negative impact. This report compiles the explanation on each type of cybercrime and its evolution since long (Grabosky, 2014). This crime scene has recently affected many businesses, government sectors, individual identities to a large extent that has caused them huge losses of money and personal loss. Earlier it was not easy to categorize the cybercrimes into specific fashion because a variety of crimes took place every day. Now, as many studies have been carried out, we can now categorize them. Statistics present the scenario of 21st century crime which has increased at an alarming rate due to the innovations of IT.
Cyberspace and Cybercrime
Today internet users and connections have increased so fast that anyone can never imagine. Cybercrime is getting more opportunities to venture inside the society as more people endure to step into cyberspace for conducting their professional and personal activities online. These crimes consist of many new kinds of crimes and ways of committing the traditional offences such as frauds, identity thefts or property crimes. Further, the gravity of cyberspace has allowed various terrorist groups to recruit, organize, raise the funds and spread their propaganda through these digital methods. These online offences are affecting millions of people around the world every day (Broadhurst, 2017). It has converted to one of the threatening and tough issues for the law bodies and judicial system to resolve.
The investigation of cybercrime has led to the discussion of the medium of this virtual crime – cyberspace. The term cyberspace was found by William Gibson, the science literature novelist in his novel named Neuromancer in 1984. Gibson defined cyberspace to be ‘a hallucination which is experienced by many authentic operators daily, in every country.’ Further, Gibson (2000) mentioned that cyberspace had no semantic meaning as yet but has become a buzzword in the world. The word then entered the public arena, meaningful or not, and became a synonym for the term Internet (CONSTANTIN, 2013). In media, the term is used to describe a feeling of social setup which exists only within a space or communication…which prevails completely within a computer space but segregated around complex networks as stated by Slater (2002)’. John Barlow (1990) in his essay mentioned about cyberspace that all the things in this space become a matter of words only. One can see the conversation of neighbours but cannot see their physical environment either. Further, Benedikt (1991) explains cyberspace to be ‘a different universe, which is parallel created by the computer and communication networks of the world. It is a world wherein there is global intellect, indicators, secrets and measurements as forms.’
The term cybercrime does not have a universally accepted meaning. Thomas and Loader (2000) defined cybercrime as, ‘the set of activities which are mediated by computers which may be either illegal or is regarded to be illicit by the parties and can be done through electronic channels’. Further, McQuade (2006) has defined it as ‘the usage of computers and other devices operated through electronic mode via information technology to assist illegal acts.’ It is a set of crimes which are conducted by networks of technology as mentioned by Wall (2007). Although the term is defined differently by various authors, all of them agree on the role of technology and network in facilitating this criminal act. The definition given by Thomas is the broadest one as compared to others. It also includes the illicit acts along with the illegal ones.
Further, different authors and experts have segregated the forms of cybercrime differently. It is not possible to discuss all of them. But we will discuss the theories given by some experts on cybercrime types. Wall (2007) has stated that there exist three separate generations of cyber-crime, all are different from each other. The differences can be explained through the scope of criminal activity of that generation. The first generation consists of traditional criminal offences done with the help of computer. These took place inside distinct computer systems and were majorly attributed by the criminal offences of workstation computers and the working systems (Wall 2011). Frauds of money or harm to the controlled information are examples of first generation crime. Further, example may include the Salami fraud in which the criminals acquire someone’s money by altering the arithmetic operations with fraud. These sometimes use the internet but mostly only the usage of computers as traditional crimes.
For the offences involved in the second generation of cybercrimes, networks are utilized as the medium. These may be categorized as ‘hybrid’. For example, world business of pornography can be included in this as internet has given avenues to such new prospects around the global networks in advanced form of traditional crimes. Governance procedures are required to prevent such types of cybercrimes which may be now available appropriately and makes it difficult to deal with such generation of cybercrimes. The trade in porn material all over the world is a perfect example of this generation of cybercrime as different nations have separate standards of legality to deal with pornographic material as mentioned by Wall (2001).
Real time cybercrimes that are also known as the third generation are the only product of prospects given by the internet which means that these acts would diminish if there was no internet facility. For e.g. spamming this is done only through the source of internet (Wall 2011). This generation of activities include various internet related crimes. Some of the acts might have clear status in terms of crime, whereas some are under the scanner of legal debates and many are already given the illegal status by individuals. The example of spamming can be categorised as a deviant activity in the process of becoming an illegal activity, in various jurisdictions such as US and UK. Carey and Wall (2001) explains one type of third generation crime i.e. illegal downloads of music and movies which gives rise to examination in the making of such laws. This also establishes that technological changes make an impact on the determination and alteration in laws of the nation. Further, there are some cyber-crime activities which do not have any criminal status as per law and are on the extreme levels of such acts. These enactments break the association between space as well as time by separating it through the global network and embed them in virtual reference of communities on online channels which pose a challenge to the traditional terminology of community. These acts are performed through text or other digital ways and include acts such as flaming debates on digital sites and boards established by Joinson (2003), virtual vandalism also mentioned by Williams (2006), cyber rape etc. Cyber communities describe them to be deviant but only few have a status of crime in legality.
Now in general terms as explained by Hinduja (2007), those crimes which take place in the physical space are known as traditional cybercrimes but also engage technology like stealing a system of computer or any mobile device having internet technology. True sense cyber offences are those which can be implemented only in the virtual space like phishing and spamming (Ubale and Isyaku, 2017). Many forms of traditional offences are being facilitated and implemented through the usage of computer networks and such negative things which were not even imagined before have occurred due to the capacities of information technology and supported devices. Further described are hybrid cyber offences consist of those crimes which may or may not include the internet but are enhanced in extremity via usage of computer systems and technology such as child pornography, cyber terrorism etc. (Hassan, Lass, & Makinde, 2012). Increased number of mobile phones and technologies has given rise to increase in such activities. Today, cybercrime is a growing problem worldwide which costs many nations billions of amounts.
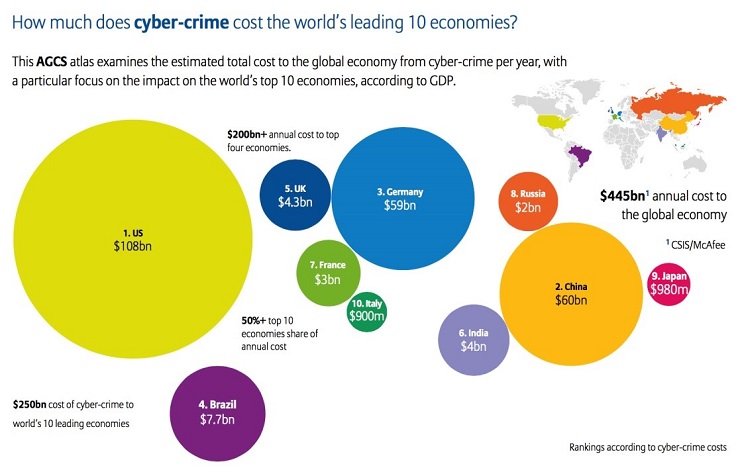
Figure:1 Cost of Cybercrime to world’s leading economies
Cyber-crime has resulted in disaster for individuals, business firms and public at large causing harm to finance, physical and sometimes emotional injury. Further studied, like many other crimes, cyber offences can result from high percentage of unemployment and negative economic conditions. When there is lack of constructive employment amongst youth, it gives them opportunity to utilize that time and knowledge in designing and implementing such criminal acts. Even certain parents today transfer the criminal morals and acceptance of non-acceptable behaviour to their kids. According to the current penetration of such offences in the global culture and younger generations, if anything not done seriously, it may affect the future values of our generation and they might not see anything wrong in such offensive acts (Hassan et al. 2012). It is difficult to estimate the existence and expenses of such computer related offences. Researches have presented that it is the most growing problem in the world from which no nation is safe. It is believed that the statistics on such cyber-crime activities do not reflect correct picture of the amount of crimes done because in reality the amount of cybercrime is way more than on paper and is intentionally underreported.
It is common sense that no crime exists in vacuum. It has grown with the changing times. There are many formal references in the literature about organized cyber offences. It becomes tough to study such topics because of various terms used synonymously like cybercrime, computer crime, digital offence, high tech offences, IT crime etc. McCuster (2006) therefore, suggest that it is difficult to investigate the comparative impact of such crimes in the society. The word cyber-crime is being used in generic terms for any kind of deviant activities conducted online in spite of their differences of relevance and complexity. Recently, IBM conducted a survey on cyber offences but did not mention the definition of the same and still managed to get the information from the participant businesses from different continents on the effect of these crimes. The ultimate effect of these surveys results into a belief that cybercrime prevails and grows but the statistics of cybercrime is not shown due to the fancies of public unawareness.
There are a variety of motives and self-interest of the criminals involved in cybercrime such as profit earning, notoriety, breaking social norms, etc. which are derived from activities like hacking, pornography trade, cyber stalking etc. (Singhal et al. 2013). The research confirms that the most driving force behind these offences is money. It in itself is a satisfying feeling that one can impact whole system. There always exists some motivational force which is worth to note along with the technical ability to implement such types of computer induced crimes and that is called the rational challenge of expertise in complex networks as noted by Grabosky (2000). All these motivations behind committing crimes exist since long; the only factor of newness is the capability of technology which assists in implement these motives. Many a times, intrinsic as well as extrinsic both kinds of motivations drive the behavior of individual involved in cybercrimes. Philosophy is one of the essential components which lead the norms of cyber offenders. Many people conduct cyber attacks in order to fight for their ideology. Political purposes are behind those who hack the websites driven through ideology beliefs as stated by Kshetri, (2005). Examples of such groups of ideological believers and hackers are Cyberjihad hackings and Islamic activists existing in Indonesia. They fulfill their ideological purposes through the new avenues provided by technology rather than physically.
Certain scholars have worked in this context and provided the reasons for people behaving in these patterns and committing crimes such as biological, sociological, psychological and sociopsychological. Motivations for different people are different varying on the type of crime, some examples being greed, challenge, revenge, adventure or lust. These theories are relevant mostly to the description of violent crimes but few of them might also apply to non-violent activities. Hence, this theory can be utilized to understand cybercrime by characterizing the supply of two factors i.e. offenders who are motivated to conduct and targets for harassment to a growing number of internet users and adaptation to computer technology. Cybercrime rate is growing at an alarming pace and experts are still in the working mode on the subject to understand and investigate such offences, there exists a deficiency of calibration and theoretical structure to monitor those who are working in this area. It is found in majority of the studies that the factor of anonymity involved in the internet channel reduces the shyness or embarrassment of criminal behavior which also includes bullying. It is further suggested by Mason (2008) that internet has created a new arena for social communication which has different norms. Due to these factors, social identity has taken place of individual ones, and social norms take control of the behavior and acts (Cesaroni, Downing, & Alvi, 2012). The feeling of individual accountability and personal association is reduced in the minds of the online users because of the anonymity involved in cyberspace, thereby, contributing to the increased inclination towards committing crimes through online medium which they might not ever conduct in person.
Here, we will discuss certain cybercrimes with case examples such as cyber terrorism, fraud, phishing, cyber bullying, hacking, stalking, online intrusion, gambling, phishing and drug trafficking. One of the highest seen crimes is of Identity theft online. It is growing at a very fast pace. It consists of the misuse of the personal information on an individual without their permission and knowledge for the uses for implementing fraud or some theft (kamal et al. 2012). The frauds generally steal important documents such as bank documents, bills or passports for the purpose. Individual’s credibility can be damaged by identity theft or even lead to lawsuits which would take long time to compensate for. Another major offence is known as ‘Phishing’ which is the deed of sending such electronic mails which are fake to some innocent users, which seem to be from authentic enterprise, is also a way of identity theft. The sender acts to be an authorized firm, like some online dealer, bank or a finance institute, with a purpose to get the personal data of the user for e.g. passwords or bank account details. According to Hoar (2005), phishing resulted in a loss of approx. $1.2 billion to the banks and institutes in 2003 United States. Further, Gartner Inc. reported that almost 30 million of the internet users who are adult felt that they have been cheated through phishing. Next comes the term Online Intrusion which consists of the usage of internet to damage or harm or infect other internet user’s computer programs, system, online space or networks (Henson et al. 2011). Malicious software or malware are the most dangerous of all which are downloaded on the victim’s system through an email or an attachment or some hyperlink. It then spreads viruses, worms or Trojans which are designated to crop their personal and confidential information. The largest case of this type of cybercrime took place in May, 2017 when about 2.5 lac victims were affected across 150 countries by a malware named as WannaCry. It was an international cyberattack where the most affected was NHS. It demanded a ransom in order to unlock the system of the victim (Reyns, Henson and Fisher, 2015). The ransom was demanded in cryptocurrency bitcoin through 28 languages by the hackers. This attach was carried on through phishing mails and the systems which were not updated with security measures.
Another form of deviated offence is Online Piracy which involves sharing or thieving the intellectual property by fraud and it is multiplied through file sharing procedure which propagates the illegally made and copied information or material further in the society (Hassan, Lass, & Makinde, 2012). It is a fact that a single infected computer system can send out approx. 26,000 spam messages in an hour as stated by Keizer, (2009). The virus named Trojan horse is also a method for making a mechanized form of system abuse which acquires financial information. Internet fraud is the one that takes place online. It is not something new, it has been existing since long in the history but the character of the same have become complex with the association of internet and electronic means. These two crimes i.e. fraud and identity theft have been the largest constitution of cybercrimes because of the motive of economic profits behind the two (Gul & Terkesli, 2012). Any potential victim can be caused damage very smoothly and quickly due to the real time operations of the Internet (Koong, Liu, & Wei, 2012).
Spam permits sending unwanted bulk messages to a wide range of audience via internet platforms, junk mails, instant messages, social network sites, file sharing systems etc. Spamming is economically affordable as it does not cost any operating charges to the senders above the managing of their mail lists and contacts and it is very tough to catch hold of the senders for such mass mailing operation (Hassan et al., 2012). The reason for increase in spamming acts is the evolution of cheap internet services and electronic gadgets. Further, the challenges in entering the market are very few, hence, spammers have increased in numbers and the quantity of unsolicited messages has risen drastically. All these offences do not only contribute to the financial properties, but the victims of cybercrime also suffer from various psychological issues for being offended such as loss of important time in order to lodge complaints and requests for refund, loss of confidential information, loss of credibility and reputation, goodwill etc. It was found out by the Federal Commission of Trade that those victims who faced the problem of identity theft in reference to credit cards of their names, 31% of them needed around 40 hours to change the credit challenges and suffered from many damages such as nuisance from creditors suffered by 48%, rejections of loans from institutes faced by 25%, criminal cases and investigations suffered by 12%. It can be said that such frauds do not just harm the users but also weaken their confidence in the authenticity of e-commerce and Internet facilities which cause such damages. It was found that in 2004, electronic websites had to bear a loss of $3 billion due to such cyber fraud cases. Hacking or Intrusion to the system can be defined as illegal access to a system or computer or storage device. This is done in order to get some information of one’s device or business. Cyber-attacks may be categorized into two forms: targeted and planned attacks & opportunistic or devious attacks as mentioned by Kshetri (2005). Particular tools and processes are utilized against some particular cyber victim after a planning phase in the targeted attack. And an opportunistic one encompasses of spreading viruses or worms extensively without any discrimination over the internet. The amount of targeted crimes is increasing very quickly. People behind target attacks are skilled and able hackers, companies having rivalry, terrorist groups, ideological haters or government firms.
One of the major shocking crimes to occur on the cyberspace is Child Pornography. It has been estimated that the business of child pornography earns about $5 billion yearly and is asked for about 126,000 times average daily via peer-to-peer programs of file sharing and is extended on about 1 lac adult websites. It is proven that this collection of deviant materials do not occur by accident, though, it is done intentionally with planned choice by individuals to make such materials online (Es, van, 2016). Such child porn has been in the import market at a lightning speed across the world. The only reason behind is sexually explicit desires to be fulfilled and profit making out of such monstrous act. The age group of children who are being exploited for these films and pictures are seven to seventeen approximately. Such sexual slayers create groups with like-minded people and victimize such innocent children even in the safety of their families due to the access through internet. One of the largest networks conducting child pornography which was caught in 2013 was known as Dreamland. They promoted pedophilia and distributed pictures of child sexual abuse through the internet and were the largest group in US history. 72 individuals have been prosecuted with the charges. They used to communicate with aliases and not their real names. The content that was issued on Dreamboard used to be encoded with a security password which only members knew. This was the largest prosecution of online cybercrime group in the history of US.
Hate crimes are not connected with internet technology and social networking sites are being utilized as the channel to delineate hate as studied by Jaishankar (2008). Websites such as Facebook, Twitter, Instagram have been used to spread such hate messages and bullies. Cyber Bullying is a process where the children and youth try to hurt each other increasingly. This offence has been established from personal hurting remarks in person to electronic interaction via different sources to hurt the sentiments of others (Hendricks, Lumadue, & Waller, 2012). Cyber Bullying is affecting all the regions and races and has become a challenge worldwide (Cesaroni et al., 2012). Parents and schools have been growing their voices against such peer harrassments through online mediums (Jones, Mitchell, & Finkelhor, 2013). The reasons for such bullying are generally related to dislike regarding somebody’s color, body structure and size, sexual likes or dislikes etc (Besag, 2010). A rumor spreads in a social circle within few seconds even before anyone could notice (Hendricks et al., 2012). Such words are considered to be real as compared to spoken things. Victims have no control over such acts and hence, feel bullied over this powerlessness. Victims generally suffer from emotional pain and psychological disturbances due to the feelings of shame, isolation or embarrassment from such acts (Hendricks et al., 2012). Cyber Stalking does not pose a threat of life to the victim but includes stalking victim’s activities on internet medium in order to collect information and give threat intimidation. Every move of the victim is observed and his privacy is endangered. Generally women and children face cyber stalking cased due to adult predators or some personal revenge. It has become more common due to use of internet. It may also cause actual stalking along with psychological or emotional damage to the victim. It can be done through emails, internet activities or computer stalking.
Conclusion
More people will continue to have online access as the internet service is expanding and cyber-crimes will continue to perpetuate through terrorist groups or other criminals across the world. It is almost impossible to eliminate the cybercrime completely but it can be reduced and prevented. It might be unrealistic to ‘tug the plug’, but steps can be taken to reduce the threats. Here, we can conclude from the study that the challenge exists in managing the risk which comes along the new technological developments while reducing the future threats posed by cybercrime (Burns and Roberts, 2013). Individuals, industries, law bodies, governments and business organizations should make collective efforts to mitigate the risks of these types of crimes. Victims and people need to raise their awareness on such kinds of crimes and need to be more educated on the ways to protect themselves from such frauds. Such trainings should be incorporated in universities and colleges to create more awareness about the same.
It is very important to first understand the behaviors exhibited by the producers and languages used by the offenders to make further corrective actions to stop severe crimes such as child pornography. There should be a law for compulsory reporting of cases on child pornography to get success in reducing it. There should be global penalties in case of such people who continue to make and distribute child porn. Law and legislations should be updated with time to address latest types of cybercrimes.
It has been noted that majority of the companies and individuals have adopted a reactive behavior rather than an approach of proactiveness to information security. These explained cybercrimes not only cost the society in terms of money but it highly costs on psychological and social impact. Lives have changes with the increased usage of internet and with the crimes on rise; it has devastated the cyberspace and individual mental state. People should adapt to information security measures in order to prevent its loss. Children should be taught about using the internet responsibly and securely. Further, special security attention should be given by young people (Buono, 2014). There has been less research on cybercrime as compared to traditional crime scenes because of the newness of the concept and issue of data availability. Hence the results available are constrained to the quality of the data available which gives rise to the need of improvements in cybercrime research on a priority. Thus, data that is standardized and reported will enhance the information availability and establish reliability of the data. Further, researches should be conducted on comparison between the attributes of online as well as offline criminals to build on the difference on these groups. This data will help in further making policies and strategies to combat cybercrime.
References
Besag, V. (2010). Cyber Bullying: Bullying in the Digital Age. Child and Adolescent Mental Health, 15(2), pp.127-127.
Broadhurst, R. (2017). Cybercrime: Thieves, Swindlers, Bandits and Privateers in Cyberspace. SSRN Electronic Journal, 1(2).
Buono, L. (2014). Fighting cybercrime through prevention, outreach and awareness raising. ERA Forum, 15(1), pp.1-8.
Burns, S. and Roberts, L. (2013). Applying the Theory of Planned Behaviour to predicting online safety behaviour. Crime Prevention and Community Safety, 15(1), pp.48-64.
Cesaroni, C., Downing, S. and Alvi, S. (2012). Bullying Enters the 21st Century? Turning a Critical Eye to Cyber-bullying Research. Youth Justice, 12(3), pp.199-211.
CONSTANTIN, A. (2013). Cybercrime and National Security in the Context of Globalization. International Journal of Information Security and Cybercrime, 2(1), pp.43-48.
Es, van, L. (2016). Virtual child pornography as potential remedy against child sexual abuse. MaRBLe, 6(2).
Grabosky, P. (2014). The Evolution of Cybercrime, 2004-2014. SSRN Electronic Journal.
Hassan, a., lass, f. and makinde, j. (2012). Cybercrime in Nigeria: Causes, Effects and the Way Out. ARPN journal of science and technology, 2(7).
Hendricks, L., Lumadue, R. and Waller, L. (2012). The Evolution of Bullying to Cyber Bullying: An Overview of the Best Methods for Implementing a Cyber Bullying Prevention Program. NATIONAL FORUM JOURNAL OF COUNSELING AND ADDICTION, 1(1).
Henson, B., Reyns, B. and Fisher, B. (2013). Fear of Crime Online? Examining the Effect of Risk, Previous Victimization, and Exposure on Fear of Online Interpersonal Victimization. Journal of Contemporary Criminal Justice, 29(4), pp.475-497.
Jones, L. M., Mitchell, K. J., & Finkelhor, D. (2013). Online harassment in context: Trends from three Youth Internet Safety Surveys (2000, 2005, 2010). Psychology of Violence, 3(1), 53-69
Koong, K., Liu, L., Bai, S. and Wei, J. (2012). Occurrences of internet fraud in the USA. International Journal of Services and Standards, 4(1), p.33.
Leukfeldt, E., Lavorgna, A. and Kleemans, E. (2016). Organised Cybercrime or Cybercrime that is Organised? An Assessment of the Conceptualisation of Financial Cybercrime as Organised Crime. European Journal on Criminal Policy and Research, 23(3), pp.287-300.
Mostufa Kamal, M., Chowdhury, I., Haque, N., Chowdhury, M. and Islam, M. (2012). Natur of Cyber Crime and Its Impacts on Young People: A Case from Bangladesh. Asian Social Science, 8(15).
PARODI, F. (2013). The Concept of Cybercrime and Online Threats Analysis. International Journal of Information Security and Cybercrime, 2(1), pp.59-66.
Reyns, B., Henson, B. and Fisher, B. (2015). Guardians of the Cyber Galaxy. Journal of Contemporary Criminal Justice, 32(2), pp.148-168.
Singhal, A., Monaco, S., Kaufman, L. and Culham, J. (2013). Human fMRI Reveals That Delayed Action Re-Recruits Visual Perception. PLoS ONE, 8(9), p.e73629.
Ubale, M. and Isyaku, S. (2017). A Situation Analysis on Cybercrime and its Economic Impact in Nigeria. International Journal of Computer Applications, 169(7), pp.19-29.
Wall, D. (2011). Cybercrime. Cambridge [u.a.]: Polity Press.


