Communications and Network Security Part 1
{`
Kelly School of Business
Indiana University
Information Systems Graduate Programs
`}
Part 1 – Introduction
Introduction
- Network security is often described as the cornerstone of IT security
- Security used to focus much on perimeter defense, but this is inadequate
- As the ‘traditional’ network boundaries disappear, resiliency of the internal network becomes equally important
- Tools without effective processes may be ineffective
- Availability of a network is its key business value
Role of the Network in IT Security
- Network as the target of attack
- Network as an enabler or a channel of attack
- Network as a channel is of greater concern and is more common
- Network as a bastion of defense
- The network is possibly the most valuable strategic asset in IT security
Network Security Objectives
- Foundations (CIA/ACI)
- Availability
- Confidentiality
- Integrity
- Access control
- Accountability
- Auditability
Methodology of an Attack
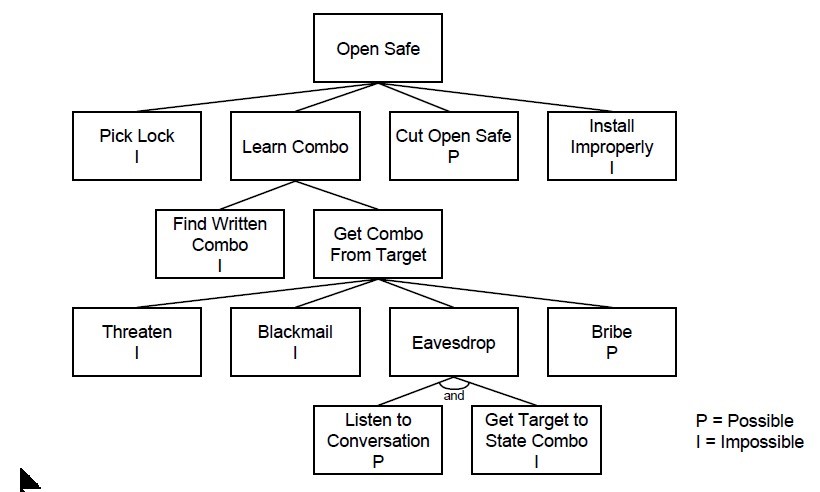
The attack tree model (A defenders view of an attack)
Source: http://www.schneier.com/paper-attacktrees-ddj-ft.html
The Attackers Methodology
- Target Acquisition
- Target Analysis
- Target Access
- Target Appropriation
- Sustain Control
Proactive Defense
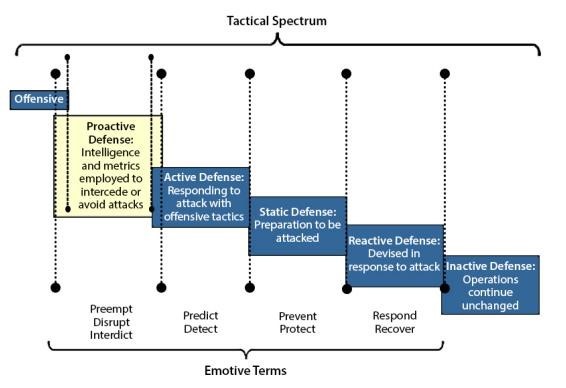
Source: Official (ISC)2 Guide to the CISSP CBK, Fourth Edition ISC2 Press
Defense in Depth
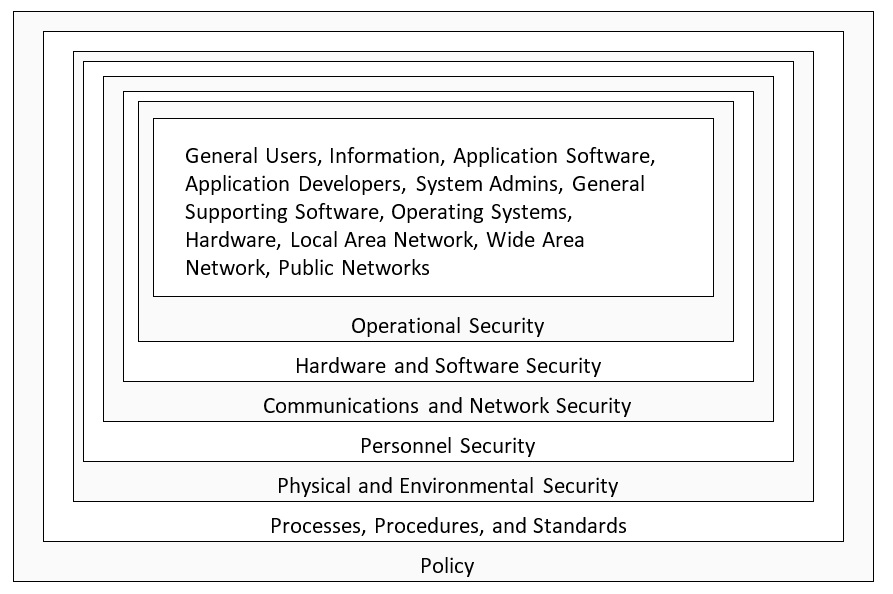
Source: Official (ISC)2 Guide to the CISSP CBK, Fourth Edition ISC2 Press
Network Architecture
- Security Perimeter
- First line of protection; generally includes firewalls, proxies, and IDS
- Network Partitioning
- Segmenting networks into isolated domains of trust
- Dual-Homed Hosts
- Have two NICs, each on a separate Network Partitioning network
Network Architecture
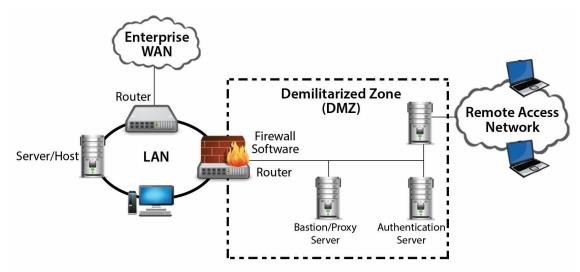
- Bastion Host
- Gateway between trusted and untrusted network that gives limited authorized access to untrusted hosts
- Demilitarized Zone (DMZ)
- Isolated subnet that allows an organization to give external hosts limited access to public resources,
without granting them to internal DMZ network
- Intrusion Detection Systems (IDS)
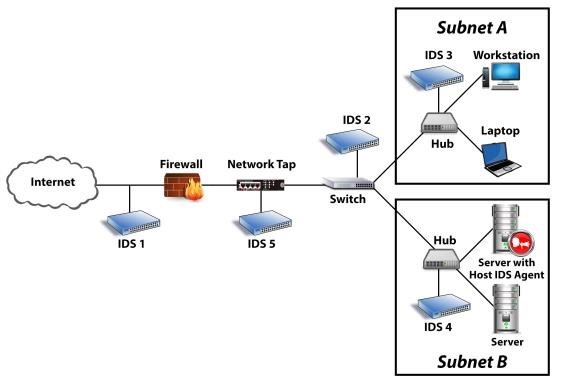
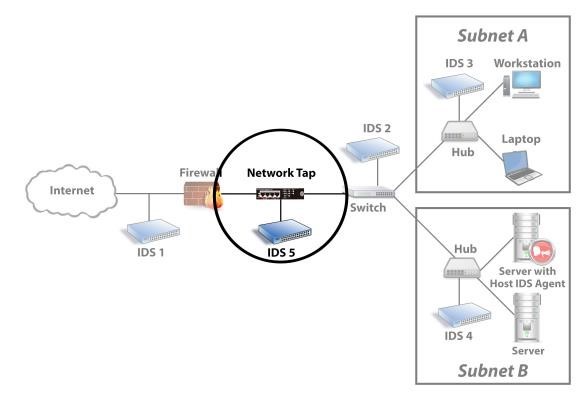
- Network Taps (Intrusion Preventions Systems)
- Scanners
- Discovery scanning
- Compliance scanning
- Vulnerability scanning
- Scanning tools
- Nessus: A vulnerability scanner
- Nmap: A discovery scanner
Reference
- Official (ISC)2 Guide to the CISSP CBK, Fourth Edition ISC2 Press


