Cryptography Part 3 Integrity, Certificates, Management and Threats
{`
Kelly School of Business
Indiana University
Information Systems Graduate Programs
`}
Integrity and Identification
Message Integrity Controls
- Provides assurance that a message has not been modified
- Checksums
- Hash functions
Hash Functions
- A hash function accepts an input message of any length and generates a fixed length output
- Message Digest Algorithm (MD5)
- Developed by Ron Rivest and the most widely used hashing algorithm
- Generates a 128-bit output digest from an input of any length
- In the last couple of years several successful attacks against MD5 have been developed
- HAVAL
- Combines variable length output with variable rounds of operation on 1024 bit input blocks
Hash Functions
- Secure Hash Algorithm (SHA)
- Developed by NIST based on MD4
- Revised version issued as SHA-1 based on MD5
- Considerably stronger than MD5
- However, several attacks have been described
- RIPEMD-160
- Developed in Europe in response to vulnerabilities in MD4 and MD5
- 160 bit output with twice the processing of SHA-1
- SHA-3
- Currently being developed under the aegis of NIST
Message Authentication Code (MAC)
- Also known as cryptographic checksum
- Small block of data generated with a secret key and appended to the message
- When the message is received, the recipient can generate MAC using the secret key and compare it to the original MAC attached to the message
- Characteristics
- Smaller than the message (typically)
- Given the MAC, you cannot compute the message
- Given the MAC and the message, it is impractical to find another message that generates the same MAC
- Usually created using DES
Hashed-MAC
- MACs are slow compared to hash functions
- HMAC uses a freely available hash function (such as MD5 or SHA-1) as a component
Attacks on Hashing Algorithms and Message Authentication Codes
- Brute force attacks
- Cryptanalysis
- The birthday paradox
- The likelihood of finding a collision for two messages and their hash value is high
Digital Signatures
- A digital signature provides assurance that
- Message comes from the person that claims to have sent it
- It has not been altered
- Both parties have a copy of the same document
- The person sending the document cannot claim that it has not been sent
- Includes a time and date as well as third party verification
Digital Signatures
- A digital signature is a block of bits generated based on the contents of the message sent and encrypted with the senders private key
- Must contain some unique value that links it with the sender of the message that can be easily verified by the receiver as well as a third party
- Must be difficult to forge and/or create a new message with same signature
Digital Signature Standard (DSS)
- Current digital signature algorithms are based on RSA and elliptic curve cryptography
- Based on public key encryption and does not provide for confidentiality and is not used for key exchange
- Two methods for creating digital signatures: RSA method and DSS method
- Both methods first create a hash of the message
- RSA approach then encrypts hash with private key of sender to create digital signature
- DSS Approach signs the hash using the Digital Signature Algorithm (DSA)
Digital Signatures in Action
- In most cases the digital signature is created by encrypting the hash of the message with the senders private key
- The resulting bits (digest) is appended to the message
- The recipient decrypts the signature with the public key of the sender
- Verifies that message has not been altered can establish nonrepudiation of origin
Certificates
- How do you know that the owner of the private key used to digitally sign is who he/she/it claims to be?
- A certificate is an electronic document used to identify an individual, a server, a company, or any other entity and to associate that identity with a public key
- Have the public key signed by a third party – the Certificate Authority (CA)
- The CA issues a digital certificate which includes the public key
- The CA verifies identity before issuing a certificate
Types of Certificates
- Client SSL certificates
- Used to identify clients to servers via SSL Server SSL certificates
- Used to identify servers to clients via SSL
- S/MIME certificates
- Used for signed and encrypted email
- Object-Signing certificates
- Used to identify signers of program code, scripts, or other signed files
- CA certificates
- Used to identify CAs
Encryption Management
- Key Management
- Key Recovery
- Key Distribution Centers
- Standards for financial institutions
- Public Key Infrastructure
- How do we know that the public key we are using actually belongs to the person who claims it is his/hers?
- Certificate authorities provide this service
- Revocation of certificates
- Cross-certification
- Legal Issues
Protocols and Standards
- Pretty Good Privacy (PGP)
- S/MIME
- Internet and Network Security
- IPSec
- SSL/TLS
Key Management Processes
- Kerchoff’s law
- “A cryptosystem should be secure even if everything about the system, except the key, is public knowledge.”
- Claude Shannon “The enemy knows the system”
- Loss of key = loss of data
Public Key Infrastructure
- A Public Key Infrastructure (PKI) is the key management environment for public key information of a public key cryptographic system
- Public key infrastructure is the combination of software, encryption technologies, and services that enables enterprises to protect the security of their communications and business transactions on networks
- Three primary purposes
- Publish primary keys/certificates
- Certify that a key is tied to an individual
- Provide verification of the validity of a public key
PKI
- PKI integrates digital certificates, public key cryptography, and certification authorities into a complete enterprise-wide network security architecture
- A typical enterprise’s PKI encompasses the issuance of digital certificates to individual users and servers; end-user enrollment software; integration with certificate directories; tools for managing, renewing, and revoking certificates; and related services and support
Source: NIST SP800-32
PKI Components
- Functional elements of a public key infrastructure include certification authorities, registration authorities, repositories, and archives
Source: NIST SP800-32
Certification Authority (CA)
- The CA confirms the identities of parties sending and receiving electronic payments or other communications
- Authentication is a necessary element of many formal communications between parties, including payment transactions
- The CA ‘signs’ or issues a public key certificate for each identity, confirming that the identity has the appropriate credentials
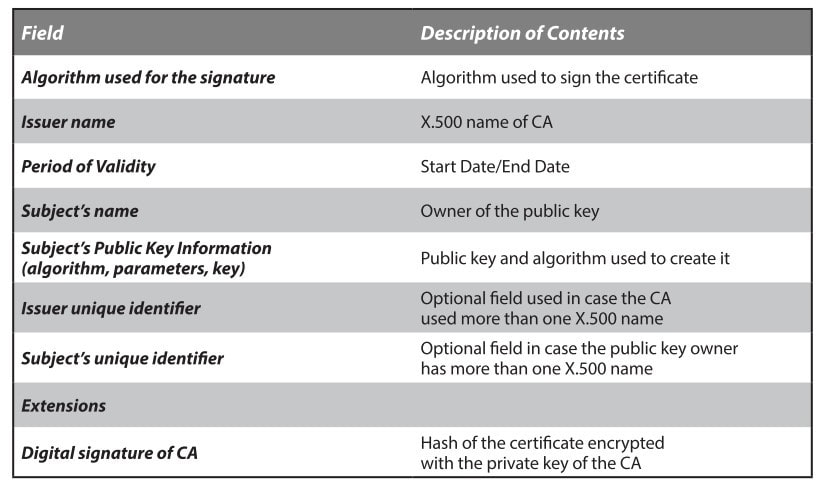
- A digital certificate typically includes the public key, information about the identity of the party holding the corresponding private key, the operational period for the certificate, and the CA’s own digital signature
- CAs must also issue and process certificate revocation lists (CRLs), which are lists of certificates that have been revoked
Source: NIST SP800-32
Registration Authority (RA)
- A registration authority (RA) is an entity that is trusted by the CA to register or vouch for the identity of users to a CA
- An RA acts as a front end to a CA by receiving end entity requests, authenticating them, and forwarding them to the CA
Repository
- A repository is a database of active digital certificates for a CA system
- The main business of the repository is to provide data that allows users to confirm the status of digital certificates for individuals and businesses that receive digitally signed messages
- These message recipients are called relying parties
- CAs post certificates and CRLs to repositories
Archive
- An archive is a database of information to be used in settling future disputes
- The business of the archive is to store and protect sufficient information to determine if a digital signature on an “old” document should be trusted
PKI Architectures
- In general, there are three basic PKI architectures based on the number of Certificate Authorities (CAs) in the PKI, where users of the PKI place their trust (known as a user’s trust point), and the trust relationships between CAs within a multi-CA PKI
- The most basic PKI architecture is one that contains a single CA that provides the PKI services (certificates, certificate status information, etc.) for all the users of the PKI
- Multiple CA PKIs can be constructed using one of two architectures based on the trust relationship between the CAs. A PKI constructed with superiorsubordinate CA relationships is called a hierarchical PKI architecture
- Alternatively, a PKI constructed of peer-to-peer CA relationships is called a mesh PKI architecture
Source: http://csrc.nist.gov/groups/ST/crypto_apps_infra/pki/pkiresearch.html
Directory Architectures
- In general, all PKI users interface to the directory infrastructure using the Lightweight Directory Access Protocol (LDAP) regardless of how the directory infrastructure is navigated
Source: http://csrc.nist.gov/groups/ST/crypto_apps_infra/pki/pkiresearch.html
XKMS: XML Key Management Specification
- XKMS allows easy management of the PKI by abstracting the complexity of managing the PKI from client applications to a trusted third party.
- XKMS defines protocols for distributing and registering public keys
- Used in XML Digital Signatures
- XML Encryption
- XKMS is implemented as a web service that allows a client application to access PKI features, thereby reducing the client application’s complexity
- The client application need not be concerned about the syntax of the underlying PKI
Source: http://www.ibm.com/developerworks/xml/library/x-seclay3
ANSI X9.17
- Addresses the need of financial institutions to transmit securities and funds through an electronic medium
- Based on hierarchy of keys
- Data keys (DKs)
- Bottom of the hierarchy
- Distributed electronically and used to encrypt and decrypt messages
- Master key-encrypting keys (KKMs)
- Top of the hierarchy
- Distributed manually and used to encrypt the DKs
Segregation of Duties
- Who has control over cryptographic keys?
- Dual Control and Split Knowledge are both required. The determination of any part of a key must require the collusion of two or more individuals with each supplying unique cryptographic materials that must be joined together to access the protected key
- Dual Control
- Two or more persons must come together to complete a process. So, each person would need to supply a key needed by a business process
- Split Knowledge
- Two or more persons have to combine their knowledge to gain access to an object
Creation and Distribution of Keys
- Creation of keys
- Automated key generation
- Randomness
- Truly random: high level of randomness of the bits that make up a key.
- Pseudo random: bits approximate the qualities of random numbers.
- Special purpose random number generators (RNG) are required.
Key Length
- The security of an algorithm cannot exceed its effective key length
- Asymmetric key length
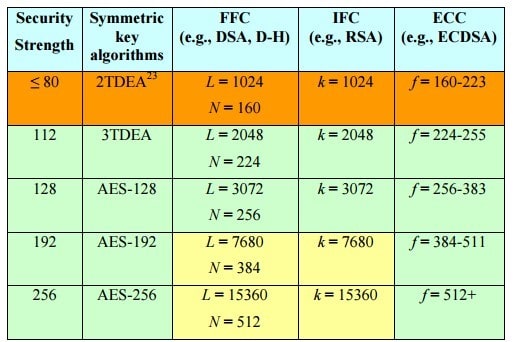
- According to RSA, 1024 bit RSA key is equivalent in strength to 80-bit symmetric key
- 2048 bit RSA keys are claimed to be sufficient until the year 2030
- 15,360 bit RSA asymmetric keys are equivalent in strength to 256 bit symmetric keys
- Elliptic curve cryptographic keys must be twice the length of the symmetric key for equivalent strength
Key Distribution
- Asymmetric Key Encryption
- Handled using PKI key server
- Symmetric Key Encryption
- Uses Key Distribution Center (KDC)
- Master keys are used between each user and KDC. Each user has a master key which is used to encrypt traffic between user and KDC
- Session key is created as needed and used for a single session. Session keys are created by KDC and sent to the two parties communicating using their respective master keys
Key Storage and Destruction
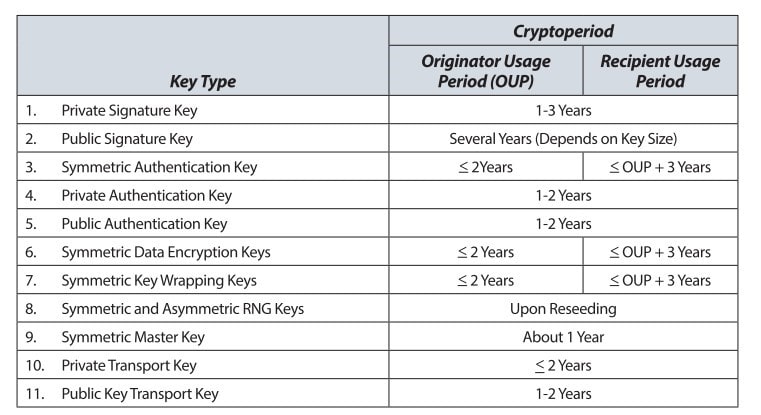
- Keys must have a validity period
- Keys must be replaced with new longer keys every few years
- All centrally stored data related to keys should be signed or have a MAC applied to it for integrity and encrypted for confidentiality
- Backup copies of central/root keys must be maintained
- Key recovery capabilities must be provided
- Archive keys for a sufficiently long time
Key Recovery
- Common trusted directories
- Multiparty key recovery
- Steganography
- Key escrow
Cryptanalysis
Cryptanalysis and Attacks
- Ciphertext only attack
- Known plaintext attack
- Chosen plaintext attack
- Chosen ciphertext attack
- Social engineering
- Brute force
- Differential power analysis
- Frequency analysis
Cryptanalysis and Attacks
- Birthday attack/Rainbow table
- Dictionary attack Replay attack
- Factoring attacks
- Reverse engineering
- Attacking random number generators
- Temporary files
Summary
References
- NIST SP 800-57 - Recommendation for Key Management – Part 1: General
- FIPS - Digital Signature Standard (DSS)
Appendix
A X.509 Certificate
Recommended Crypto Periods
Comparable Strengths