Cryptography Part 1 – Introduction and Concepts
{`
Kelly School of Business
Indiana University
Information Systems Graduate Programs
`}
Part 1 – Introduction and Concepts
Introduction
- Cryptography is used to hide data – to render data unintelligible through its transformation into an unreadable state - and to ensure that data has not been altered in transit. It can also be used to ensure the authenticity of the data as well as the authenticity of the data source.
- Cryptography supports confidentiality, integrity and authenticity
- It does not support availability
Cryptography concepts
- Plaintext or Cleartext
- The original message
- Readable by attacker
- Ciphertext or cryptogram
- Altered message that is unreadable to anyone except the intended recipients Unreadable by attacker
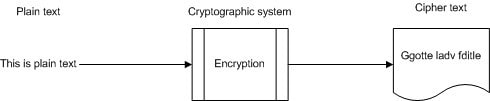
- Encryption / enciphering
- The process of converting plaintext to ciphertext
- Decryption / deciphering
- The reverse of encryption – going from ciphertext to plaintext using the cryptographic algorithm and the key
- Algorithm
- Mathematical function used in the encryption and decryption process
Figure 3.1 The cryptographic process
- Key or Cryptovariable
- The sequence that controls the operation of the cryptographic algorithm
- Determines behavior of algorithm and permits reliable encryption and decryption of the message
- Keys can be private (secret) or public
- Nonrepudiation
- A security service by which evidence is maintained so that the sender and the receiver of data cannot deny having participated in the communication
- Non-repudiation is associated with digital signature keys and digital certificates
- Non repudiation of origin
- Non repudiation of receipt
- Cryoptosystem
- The entire cryptographic operation
- Includes the algorithm, the key and key management functions
- Cryptanalysis
- Study of techniques for defeating cryptographic techniques and by extension security services
- Cryptology
- Science that deals with hidden, disguised or encrypted communications
- Includes communications security and communications intelligence
- Collision
- Occurs when a hash function generates the same output for different inputs
- Key space
- The total number of possible values of keys in a cryptographic algorithm or other security mechanism (such as password; numbers generated by smart cards).
- Key space = 2n where n = length of key in bits
- Work factor
- Time and effort required to break a protective measure
- Initialization Vector (IV)
- Non-secret binary vector (block of bits) used as the initializing input for the encryption of a plaintext sequence
- Increases security by introducing additional cryptographic variance to create unique ciphertext using the same key
- Also used to synchronize cryptographic equipment
- IV must be known to the recipient to decrypt message
- Encoding
- Action of changing a message to another format through the use of a code.
- Usually used for transmission or storage
- Used for message integrity as opposed to confidentiality
- Decoding
- Reverse of encoding: converting encoded message into its plaintext format
- Transposition or permutation
- Reordering plaintext to hide the message
- Substitution
- The process of exchanging one letter (or byte) for another
- SP-Network
- Substitution and Permutation
- Adds confusion and diffusion to the process
- Confusion
- Provided by mixing/changing the key values used during the repeated rounds of encryption
- Key is changed for each round of encryption
- Makes it very hard to find the key even if we have a large amount of plaintext/ciphertext pairs encrypted using the same key
- Diffusion
- Mixing up the location of the plaintext throughout the ciphertext
- Location of first character of plaintext may change several times during the encryption process due to transposition
- Good diffusion means that if one bit of the plaintext is changed, then the ciphertext should change completely
- Avalanche Effect
- Designing algorithms where a minor change in either the key or the plaintext will have a significant change in the resulting ciphertext
- A feature of a strong hashing function
Protecting Data
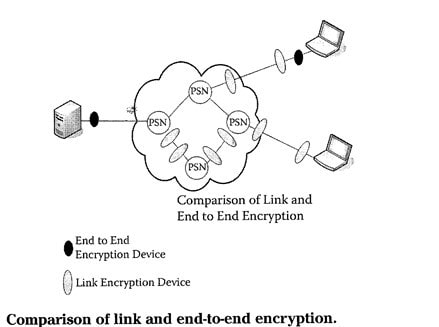
- Data Storage
- Data Transmission
- Link encryption vs. end to end encryption
Methods of Cryptography
- Methods of encrypting data
- Stream
- Encrypts data one bit at a time
- Block
- Encrypts data one block at a time
Exclusive OR (XOR)
- XOR is a Boolean function very commonly used in cryptographic operations
- A binary operation that adds two binary values together
- If the values added are the same, output is 0
- If the values added are different, output is 1
{`
Plain text 0101001
Encryption keystream 01110011
Cipher text 00100010
`}
Stream Based Cipher
- A stream based cipher mixes (XOR) the plaintext with a keystream that is generated by the cryptosystem
- Stream-based ciphers work primarily on substitution
- Keystream must be strong (long) enough to be not easily guessed because the keystream will repeat after a while
- The strength of the cipher depends on specific implementation
- Key management processes must be secure
Block Ciphers
- Operates on blocks of plaintext
- Blocks sizes are usually multiples of 8
- Most block ciphers use a combination of substitution and transposition to perform their operations
- This makes them relatively stronger than most stream based ciphers
- Also makes them computationally intensive and expensive to implement
- Stream-based ciphers are usually implemented in hardware and block ciphers are usually implemented in software
Encryption Systems
- Substitution ciphers
- Substitutes one letter for another based on cryptovariable
- Transposition ciphers
- Monoalphabetic and polyalphabetic ciphers
- Modular mathematics
- Represents each letter by the modulus of its numerical place in the alphabet modified by a key
- Running key cipher
- Key is repeated for the same length as the plaintext input
Encryption Systems
- One-time Pads
- Steganography
- Hides a message inside another medium
- Watermarking
- Code words
Summary


