Network security and cryptography assignment
Scenario
You are a member of the online security team in a financial services organisation, the UK National Internet Bank PLC (UKNIB). UKNIB offers a variety of financial services, and has no high street branches. Access to all accounts is through the Internet.
Given the reliance on internet-based services, the issue of cyber-security is extremely important to UKNIB. As a result, the Board of Directors have stated that their objective is to offer maximum security for their customers. Recently, UKNIB has announced that it will start to use a customer's mobile telephone as an authentication second factor (2FA). The following diagram shows the logical network architecture. The company employs approximately 90 staff in all functions, located at its head office in London. The head office network has a small data centre to support development work. There is a perimeter firewall.
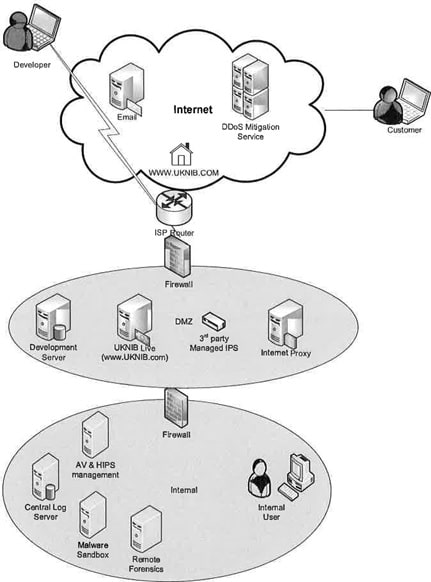
The UKNIB uses a distributed model for application development. Developers (employees) work remotely and connect to the head office development server through the Internet. Developers have administrative rights to their computers for their work. Their PCs have security defences including Antivirus (AV) and Host Intrusion Detection System (HIDS).
Customers access their accounts using a mobile application or via a browser on a PC. The accounts are all hosted in a remote data centre. The UKNIB 'in-house' security team are responsible for overall security. However, the following aspects are provided by specialist external IT contractors: (1) DDoS Mitigation Service; (2) Cloud Email Service; (3) Firewalls; and (4) IDS/IPS.
The UKNIB 'in-house' security team provide a number of functions, which include: (1 ) Internet Browsing Proxy; (2) Desktop AV with HIPs; (3) Remote forensics management capability; (4) Malware Sandboxing; and (5) Central logging in a Big Data solution.
You are also a member of the UK Cyber-security Information Sharing Partnership (CiSP). This is where network and host Indicators of Compromise (IOC) are shared and questions can be asked anonymously to the community. For further information regarding CiSP, please see: https://www.cert.gov.uk/cisp/
Task 1 — Risk Assessment (10 Marks)
- Analyse the scenario and identify FIVE (5) important information assets relating to UKNIB.
- Create a table (see below) which lists the assets. For each asset identify the main security threats that you think could affect its confidentiality (C), integrity (l) or availability (A). Remember, threats can be accidents as well as malicious. There are likely to be multiple threats for each asset and the same threats are likely for several assets.
|
Asset |
Threat |
CIA? |
Likelihood |
Impact |
Risk |
|
E.g. personal data |
Server failure |
A |
Low |
Medium |
Low |
|
Employee theft |
C |
Low |
Medium |
- Complete the columns of the table by assessing the likelihood of the threat being successful and the impact that it would have on UKNIB. In this scenario you should consider Low/Medium and High definitions as follows:
|
Likelihood |
Impact | |
|
Low |
Less than once per year |
Inconvenience may affect operation for a day or two |
|
Medium |
Once per year to once er week |
Operation may be impacted for over a week, loss of clients. |
|
Several times a week |
College may not survive — lost reputation and clients |
- Now complete the Risk column by using the following Risk matrix.
|
Impact | ||||
|
Likelihood |
Low |
Medium | ||
|
Low |
Ve Low |
Low |
Medium | |
|
Medium |
Low |
Medium | ||
|
Medium |
Very High | |||
A completed table will look like:
|
Asset |
Threat |
CIA? |
Likelihood |
Impact |
Risk |
|
E.g. personal data |
Server failure |
A |
Low |
Medium |
Low |
|
Employee theft |
C |
Low |
Medium | ||
Task 2 — Explaining Risk Control (45 Marks)
Once you have identified the highest risks, you need to make recommendations of how to control those risks, i.e. what security technology helps to reduce the risks.
- Discuss each of the threats you have identified and explain what security you recommend to put in place to reduce the risk. A good answer should discuss a range of security measures to combat a threat and then provide a justification of your choice. You should also explain technical terms in your answer.
- Where you use encryption, explain why and the protocol you recommend. There should also be a short critical discussion of any alternatives. This section of the report should be approximately 750 words
Task 3 — The attack (25 Marks)
The attack is planned by a professional cyber-criminal gang using a bespoke information stealing Trojan. It is used to gain access to the computers of members of the bank and access as much information as possible. The following events refer to Figure 2:
1 . The gang target remote developers with spear-phishing emails and one email is opened, resulting in the Trojan being installed.
- The Trojan makes successful command and control connection via developer's home broadband link.
- The gang can then obtain unauthorised access to UKNlB's development environment, resulting in the exfiltration of a subset of live customer data used for Live Proving.
- Customer data is then used in spear phishing campaign to harvest credentials via a phishing page using a Zeus Trojan.
- There is subsequently fraud against customer accounts, being transferred to accounts in multiple banks in countries outside the UK.
The security team know is that there is a high volume of alerts for a Backdoor Trojan traffic block from the HIDS on the computer of a remote developer. This has been reported through the SIEM system. The Trojan is attempting to contact its command and control (C2) parent and withdraw data. As a result, fraud teams report that multiple accounts are being debited.
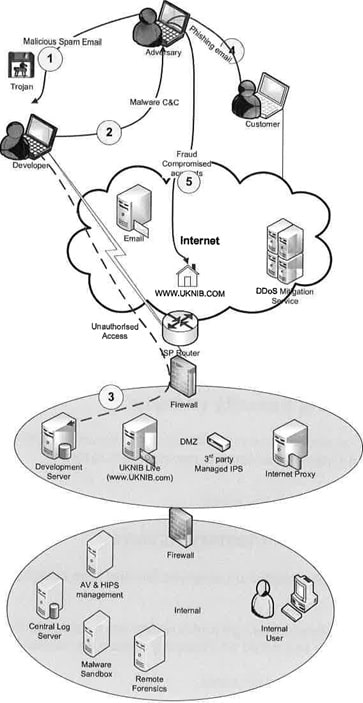
Figure 2: The attack sequence Analyse the attack description and answer the following questions. You should fully explain technical terms to demonstrate your understanding.
- Briefly explain what is meant by a bespoke Trojan and why the Anti-Virus did not pick it up.
- Outline how the attackers used the Trojan to obtain customer data and briefly explain why the Firewall didn't stop this.
- A subset of customer data was kept on the development machine for live testing. Briefly explain the significance of this in the attack and outline what you would do to reduce risk.
- The term 'Spear Phishing' is used in the description. Briefly explain what is meant by Spear Phishing and discuss how to reduce the risk of a target 'being caught'.
- What are the main characteristics of a Zeus Trojan? Please note that there are many hundreds of variants of Zeus. Consequently, please do not use any Wikipedia references in your answer.
- What actions would you take to reduce the risk of such a security breach happening again?
This section of the report should be approximately 550 words.
Task 4 — Maintaining Security (10 Marks)
Explain any actions you would recommend for ensuring security in UKNIB and monitoring the effectiveness of the Information security management system.
This task requires approximately 100 words.
Task 5 — Reflective commentary (10 Marks)
You should use this section to reflect on what you learned from completing the assignment.
- Explain any problems you had and how you went about solving them.
- Explain anything you would do differently if you were to start it again.
This task requires approximately 100 words
