Kelly School of Business
Communications and Network Security Part 2
{`
Kelly School of Business
Indiana University
Information Systems Graduate Programs
`}
Part 2: Network Protocols and Security
Network Protocols and Security
- Fast access, not secure access is the driving force behind the design of most network protocols
- Many protocols do not provide authentication – An application cannot rely on the security or authenticity of the underlying protocols
- Security is often provided by directory services and/or servers
- The big problem here is that security is applied after the network is accessed
Network Communication Models
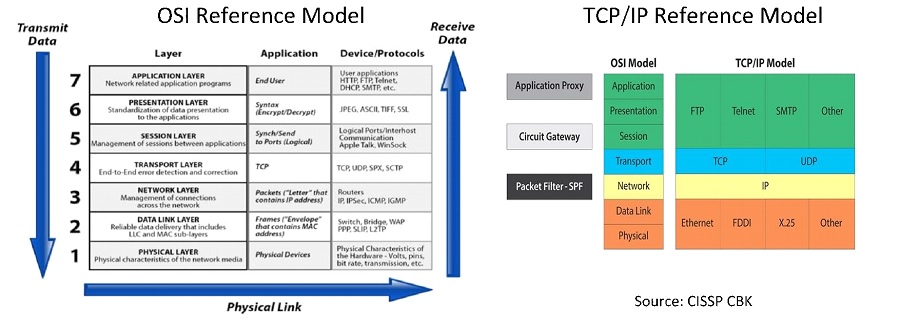
Source: CISSP CBK
We will focus on OSI model as it is the one that security professionals need understand as a baseline
1. Physical Layer
- Analog vs. Digital communications
- Network topologies
- Bus, Tree, Mesh and Star
- Cabling
- UTP/STP Wiring
- Fiber Optic
- Wireless transmission
- Mobile Telephony
2. Data Link Layer
- Ethernet
- Hubs
- Repeaters
- Bridges
- Switches
- VLAN
- Wireless LANs
VLAN Attacks
- MAC Flooding Attack
- When the MAC table of a switch becomes full, the subsequent traffic will be permanently flooded within the VLAN. An attacker can exploit this by turning the switch into a dumb hub and sniff the flooded traffic
- VLAN Leaking
- Uses tagging attacks to get unauthorized access from one VLAN to another
- ARP Poisoning
- Involves poisoning of the ARP cache of two devices by sending false MAC address information, and intercepting the communication between those two devices
Wireless Authentication/ Encryption
- WEP (IEEE 802.11)
- Two methods
- Open System Authentication
- Provides identification based on wireless adapter's MAC address only; not authentication
- Shared Key Authentication
- Uses standard challenge and response mechanism and shared secret key
- Flawed technique: Intercepting the challenge and response can be used to recover the key stream
- Considered insecure and deprecated
- WPA (WiFi Protected Access)
- Uses Temporal Key Identity Protocol (TKIP) for data encryption that provides higher level of assurance than WEP
- Vulnerability: Small packets can be decrypted and arbitrary data can be injected
Wireless Authentication/ Encryption
- WPA2 (IEEE 802.11i)
- Allows only authorized users to access a wireless network and supports stronger cryptography and authentication control like Extensible Authentication protocol (EAP)
- Two types
- WPA2 Personal - uses pre-shared key (PSK) where every user is given the same passphrase
- WPA2 Enterprise – uses 802.1X authentication server which distributes different keys to each user
- WPA2 with AES encryption is currently the preferred encryption mode
Wireless Security Issues
- ‘Parking lot’ attack
- SSID Flaw
- Denial of Service (DoS) attack on target access points
- Man-in-the-middle de-authentication attacks through soft access points
- Hotspots
Bluetooth
- Short-range wireless communications
- Very vulnerable
- Blue jacking
- Buffer overflow
- Blue bug attack
- SNARF Attack
Additional Reading: http://www.thebunker.net/resources/bluetooth
3. Network Layer - IP
- IP is an unreliable protocol – it does not guarantee packets arrive error free or in the correct order
- Reliability is left to higher layers
- IPv6 improvements
- Improved security - IPSec is required: communicating partners can authenticate with each other
- More concise header – faster processing of packets
- IPSec is a suite of protocols for communicating securely with IP by providing mechanisms for authentication and encryption
- Mandatory with IPv6; optional in IPv4
Problems with IPv4
- Address Exhaustion
- Even with the use of CIDR, routing tables, primarily in the IP backbone routers, are growing too large to be manageable
- Traffic priority, or class of service, is vaguely defined, scarcely used, and not at all enforced in IPv4, but highly desirable for modern real-time applications
- The number of mobile data applications and devices grow quickly; IPv4 has difficulty in managing forwarding addresses and in realizing visitor-location network authentication
- There is no direct security support in IPv4. Various open and proprietary security solutions cause interoperability concerns. As the internet becomes the fabric of every life in the new cyber space, security enhancement to the infrastructure should be placed in the basic IP protocol
Reference: IBM Redbook section 9.1.1
IP Risks and Attacks
- IP Address Spoofing
- Packets are sent with an incorrect source IP address forcing victim to send response to another host
- g. SYN attack
- Source Routing Exploitation
- IP allows the sender to specify the routing instead of leaving it to the router
- Can use multi-homed systems to make packets move from one network to another without authorization
IP Risks and Attacks
- SMURF Attack
- Uses ICMP Echo requests to create DoS attacks
- Send an ICMP echo request with spoofed source IP (IP of victim) to networks’ broadcast address which will forward packet to every host on the network
- Victim will be overwhelmed with responses
- Fraggle attack
- Uses UDP instead of ICMP
- Sends UDP packet on port 7 with spoofed IP address of victim to broadcast address of network
- Victim will be overwhelmed with responses
IPv6
- IPv6 offers the following significant features:
- A dramatically larger address space, which is said to be sufficient for at least the next 30 years
- Globally unique and hierarchical addressing, based on prefixes rather than address classes, to keep routing tables small and backbone routing efficient
- A mechanism for the auto-configuration of network interfaces
- Support for encapsulation of itself and other protocols Class of service that distinguishes types of data Improved multicast routing support (in preference to broadcasting)
- Built-in authentication and encryption
- Transition methods to migrate from IPv4 Compatibility methods to coexist and communicate with IPv4
IPv6 Addressing
- IPv6 uses 128 bit addresses
- 2 x 1038 addresses: a very large number
- It allows multilevel sub-netting and allocation from a global backbone to an individual subnet within an organization
- The large IPv6 address space is organized into a hierarchical structure to reduce the size of backbone routing tables
- IPv6 addresses are represented in the form of eight hexadecimal numbers divided by colons, for example:
- FE80:0000:0000:0000:0001:0800:23E:F5DB
- To shorten the notation of addresses, leading zeroes in any of the groups can be omitted for example:
- FE80:0:0:0:1:800:23E7:F5DB
- Finally, a group of all zeroes, or consecutive groups of all zeroes, can be substituted by a double colon, for example:
- FE80::1:800:23E7:F5DB
IPv6 Security
- There are two optional headers defined for security purposes:
- Authentication Header (AH)
- Encapsulated Security Payload (ESP)
- AH and ESP in IPv6 support authentication, data integrity, and optionally confidentiality.
- AH conveys the authentication information in an IP package, while ESP carries the encrypted data of the IP package.
Firewalls
- Software or hardware that filter incoming traffic and then either blocks it or allows it to pass through, based on a set of rules
- Filtering is generally done based on the address and/or the service (port)
- They should be placed between entities that have different trust domains
Proxy server
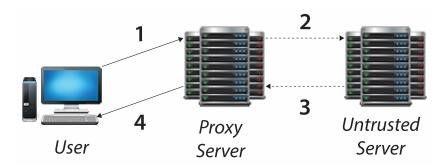
- A proxy server mediates communications between untrusted end points
(servers/hosts/ clients) and trusted end points (servers/hosts/clients)
- A proxy may forward traffic from internal client machines to untrusted hosts on the Internet, creating the illusion for the untrusted host that the traffic originated from the proxy server, thus hiding the trusted internal client from potential attacker
Secure Shell (SSH)
- Allows users to login to a remote computer over an encrypted tunnel
- The SSH tunnel protects integrity of communications preventing session hijacking
- Provides for strong authentication
Virtual Private Network (VPN)
- VPN is an encrypted tunnel between two hosts that allows them to securely communicate over an untrusted network
- Uses IPSec for Authentication and Confidentiality
- Once connected, the user has all privileges as though s/he were physically on the network to which the connection is made
- So, if VPN access is compromised, attacker will have full access to network
Tunneling
- VPN uses Point to Point Tunneling Protocol (PPTP) running over other protocols (IPSec or SSL/TLS) to build the tunnel between end points
- PPTP derives its encryption key from the user password and is thus weak
- PPTPv2 addresses some of the issues
- However, it is still susceptible to password guessing attacks
- Layer 2 Tunneling Protocol (L2TP)
- Used with dial-up connections. Does not prove encryption – depends on IPSec to do that
- RADIUS is an authentication protocol used for services requiring single sign-on for layer 3 network access
SSL/TLS VPN
- Traditional VPN cannot work with proxy servers
- Uses SSL/TLS to create a tunnel to organization network
- Remote users use a web browser to access applications on the organization network
- SSL VPNs have several advantages over IPSec
- The use of a proxy server allows restrictions on user access based on security policies
- Does not require VPN client software to be installed on client system
ICMP
- Internet Control Message Protocol
- Used for exchange of control messages between hosts and gateways and is used by commands such as ping and tracert
- Exploits
- Ping of Death
- ICMP redirect Attacks
- Ping scanning
- Traceroute exploitation to map network
ICMPv6
- ICMPv6 performs error reporting, route discovery, and diagnostics as well as conveying multicast group membership information and ARP
- IGMP and ARP are thus not separate protocols/functions in IPv6
- Neighbor discovery
- Neighbor discovery is an ICMPv6 function that enables a node to identify other hosts and routers on its links
VRRP
- Virtual Router Redundancy Protocol
- If you want five 9 availability, critical routers cannot be single point of failures
- VRRP is a protocol that allows automatic failover for routers
- A virtual router is configured and presented to the network
- The virtual router will have one primary router and at least one secondary router
- The primary router performs all of the routing on behalf of the virtual router
- If primary router fails, secondary router takes over
- Primary and secondary routers are often in separate data centers
4. Transport Layer
- Links the session layer to the network layer
- Performs Packetization and Reassembly
- Establishes connection (virtual)
- Connection Oriented
- Connectionless
- Quality of Service (QoS)
- TCP and UDP map data connections using port numbers
- Well known ports – Ports 0 to 1023 assigned by IANA (Internet Assigned Numbers Authority)
- Registered ports – Ports 1024 to 49151 can be registered by application developers with the IANA
- Dynamic or private ports – Ports 49152 to 65535 can be freely used by applications
Transmission Control Protocol (TCP)
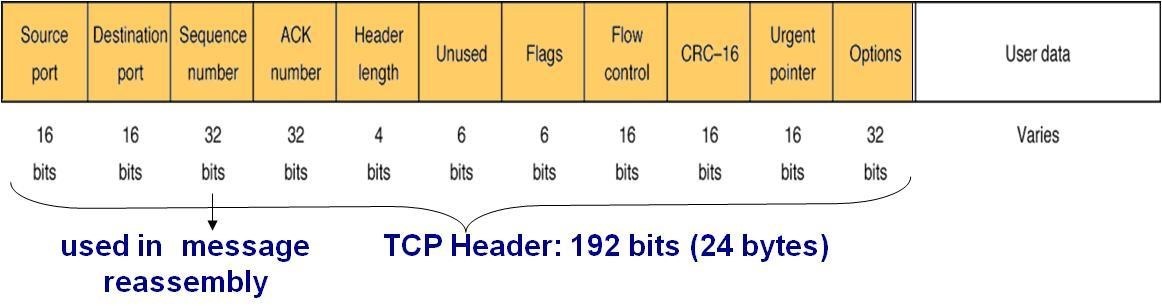
- Links the session layer to the network layer
- Performs packetization and reassembly
- Breaking up a large message into smaller packets
- Numbering the packets and
- Reassembling them at the destination end
- Ensures reliable delivery of packets
Packetization and Reassembly
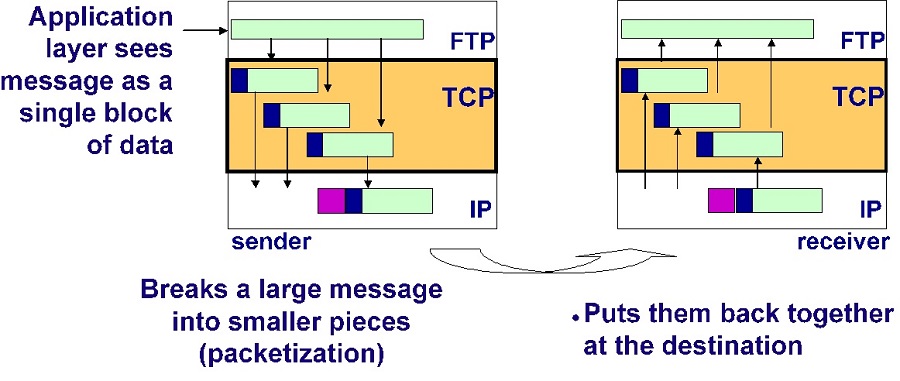
(reassembly)
What size packet to • Delivers incoming packets use? Done through as they arrive (e.g., Web pages) or negotiations to wait until entire message arrives (e.g., e-mail)
Transport Layer Addressing
- TCP may serve several Application Layer protocols at the same time
- Problem: Which application layer program to send a message to?
- Solution: Port numbers located in TCP header fields; 2-byte each (source, destination)
- Standard port numbers
- Usual practice numbers
- Nonstandard port numbers
- Possible, but requires configuration of TCP
- 16 bit numbers (range from 0 to 65535)
Setting up Virtual Connections
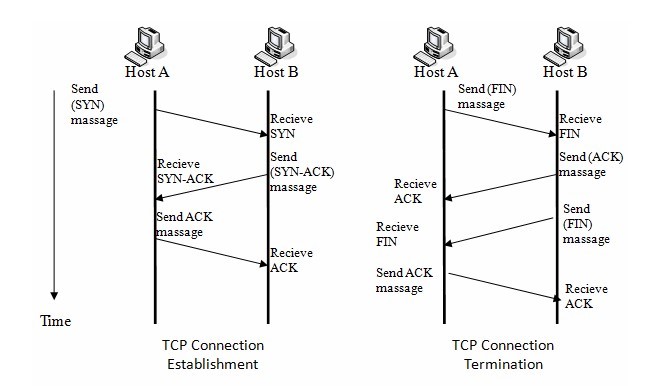
- Scanning techniques
- Port scanning: probing for TCP services on a machine
- FIN Scanning: send a request to close a connection to a specific port. If there is no application at that port, there is no response. If there is an app, it will respond
- Null and XMAS scanning are variants
- SYN Scanning: Only the initial steps of the TCP handshake is performed.
Makes the scan harder to detect
- TCP Sequence number attacks: Introduce fake packets into TCP data stream by finding out sequence numbers through eavesdropping. Used for session hijacking
- Session hijacking: Unauthorized insertion of packets into data stream
- IP Spoofing: Insert packets with a fake sender IP and guessed sequence number. Attacker will not see response to any inserted commands
- Man-in-the-middle attacks
- Attacker sniffs or intercepts packets and replaces them with his own
- Both sides of the communication would now be communicating with the attacker
- Countermeasures have to be executed at layer 3
- Denial of Service
- SYN flooding
5. Session Layer
- Responsible for creating, managing, and tearing down sessions between peer hosts
- Transmission modes
- Simplex
- Half duplex
- Full duplex
5. Session Layer
- Directory Services
- DNS
- DNS is a popular target of attack. By manipulating DNS it is possible to divert intercept or prevent end user communication without having to attack any end devices
- DNS does not enforce data consistency and integrity
- Has weak authentication mechanisms
- Management of the globally distributed DNS infrastructure is difficult
Domain Name Service (DNS)
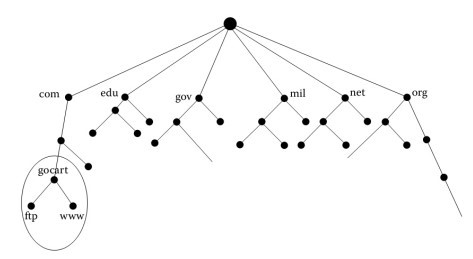
- Recursive DNS resolution
- When a client cannot translate a domain name itself, it sends a DNS request to its local DNS server using UDP
- The DNS server either responds by sending a UDP packet back to the client or, if it still doesn’t know the IP address, it sends another UDP packet to the next highest name server in the DNS hierarchy
- The higher level is usually the DNS server at the top level domain (such as the DNS server for all .edu domains)
Dynamic DNS
- The Dynamic Domain Name System (DDNS) is a protocol that defines extensions to the Domain Name System to enable DNS servers to accept requests to add, update, and delete entries in the DNS database dynamically
- DDNS is currently available in a non-secure and a secure flavor, defined in
RFC 2136 and RFC 3007, respectively
- Rather than allowing any host to update its DNS records, the secure version of DDNS uses public key security and digital signatures to authenticate update requests from DDNS hosts
- Without client authentication, another host could impersonate an unsuspecting host by remapping the address entry for the unsuspecting host to that of its own. After the remapping occurs, important data, such as logon passwords and mail intended for the host would, unfortunately, be sent to the impersonating host instead
Vulnerabilities in DNS
- A DNS server can respond to a recursive query with information that was not requested
- DNS server does not authenticate information received
- There is no fully successful solution to these vulnerabilities
- New versions of DNS servers ignore responses that are not the result of a query
- Efforts to introduce stronger authentication into DNS have not been very successful
- So, higher level layers will have to take care of these issues
DNS Attacks
- DNS Spoofing
- An attacker tries to poison DNS server’s cache
- First send out a query to DNS for resolution
- If attacker controls primary name server for the domain, s/he will use it to respond to the query with additional information than was originally requested. This information is now stored in the cache
- If attacker does not have control of the primary DNS server, s/he will respond to the original request using IP spoofing before the legitimate DNS server can respond
Lightweight Directory Access Protocol (LDAP)
- Usually a front end to a directory service like Active Directory
- LDAP uses weak authentication based on host name resolution
- LDAP communication is transferred in clear text
- Solution: Use LDAP over SSL
DHCP
- Used to issue IP addresses in a dynamic fashion
- There is no authentication
- User can plug computer into network and get an IP address
- Intruder can give out IP address and other credentials (including DNS address) by masquerading as a DHCP server on the network
- However, DHCP makes network administration easy and is hence popular
FTP (File Transfer Protocol)
- FTP is a stateful (server remembers communication with client) protocol
- FTP uses simple login/password authentication in cleartext
- Additional protocols
- Secure FTP with TLS is an extension to the FTP standard that incorporates encryption of the session
- SFTP /SSH FTP is file transfer using SSH and is not related to FTP; encrypts command and data
- FTP over SSH tunnels normal FTP over encrypted SSH session
- Active and Passive transfer modes. In active mode, server initiates connection. In passive mode, client initiates connection
- Anonymous FTP accepts any email as userID
- TFTP (Trivial FTP) used usually in LANs for pulling packages
HTTP
- Originally conceived as a stateless protocol and does not support encryption
- Uses a simple authentication mechanism
- Latest version supports stateful connections
- Transmits data in cleartext
- HTTP Proxying: Anonymizes HTTP packets
- Open Proxy servers
- HTTP proxy is used as a mechanism to implement content filtering.
- HTTP Tunneling: Encapsulates outgoing traffic from an application in an HTTP response to an HTTP request in incoming traffic. This will bypass user policy restrictions
Simple Mail Transfer Protocol
- Used to send email messages on the Internet
- Lacks authentication and encryption
- Email spoofing is frequently used as a means to obfuscate the identity of a sender in spamming and in social engineering attacks
- S/MIME is used to digitally sign and encrypt the email messages; provides non-repudiation
6. Presentation layer
- Services
- Character code translation Compression
- Encryption and decryption
- Transport Layer Security (TLS)
- Based on SSL (Secure Sockets Layer)
- Provides for a secure authenticated channel between hosts on the internet
- Mutual authentication of server and client
- Encrypted connections based on algorithms implemented at both client and server
- Actually a transport layer protocol, but implemented between transport layer and app layer in TCP/IP model
7. Application layer
- It is the application’s portal to network-based services
- When an application transmits or receives data over a network, it uses the services from this layer
- See material on a variety on protocols in CISSP book
- We will examine the application layer security protocols when we cover encryption
Appendix
Example of TCP Port Scan
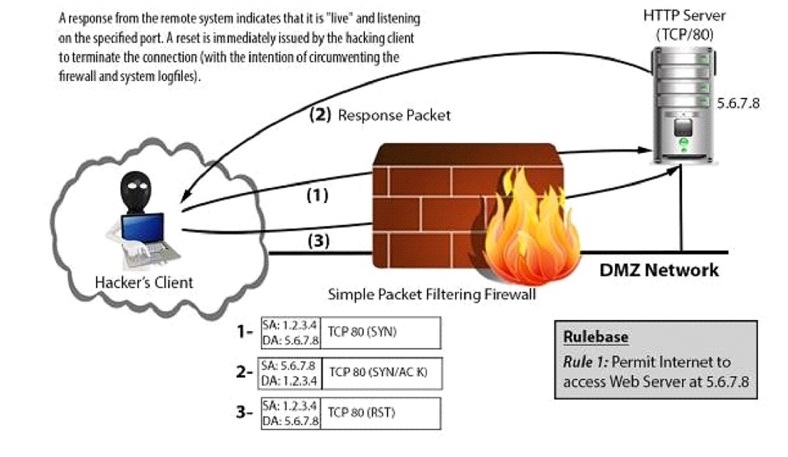
Architecture of a Botnet
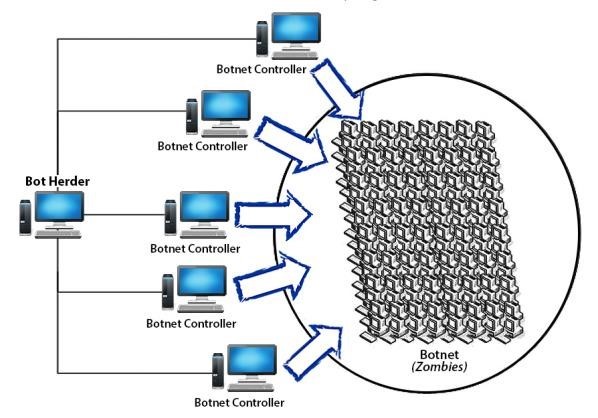
A DoS Attack
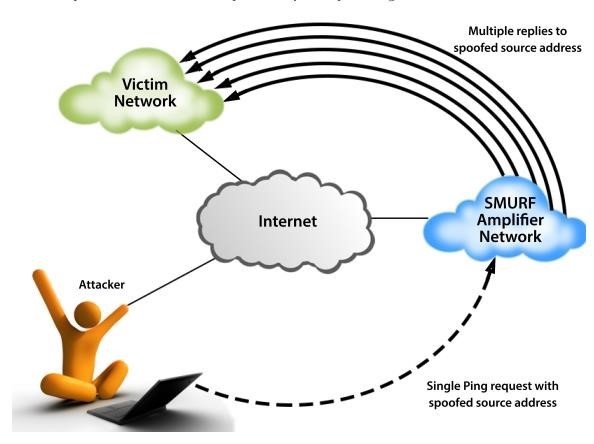
- The attacker uses spoofed PING packets to floor a network by using a vulnerable intermediary network


