Security Engineering
{`
Kelly School of Business
Indiana University
Information Systems Graduate Programs
`}
Engineering Lifecycle
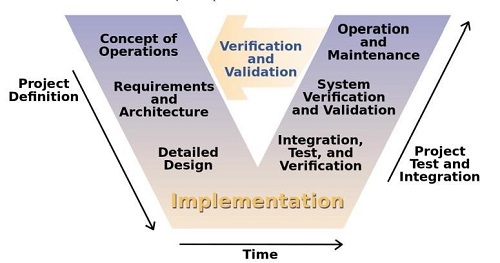
- Key system engineering technical processes
- Requirements Definition
- Requirements Analysis
- Architectural Design
- Implementation
- Integration
- Verification
- Validation
- Transition
Security Architecture
- High-level and detailed processes, concepts, principles, structures and standards used to define, design, implement, monitor and secure operating systems, applications, equipment, and networks
- A security practitioner needs to identify the key issues and concerns that the engineering lifecycle must address for the enterprise
- Once these issues are agreed upon by the stakeholders, security design principles can be used by the architect to ensure that all known and identified threats, vulnerabilities, and risks have been addressed as part of the security architecture being included in the lifecycle
- Enterprise level vs. system level
- Need to know both!
Enterprise Security Architecture
- Primary purpose is to establish a strategic design of security infrastructure and services across the entire organization
- Focuses on -
- the design and implementation of common security services, and
- the enforcement of security zones of control
Common Security Services
- Boundary Control Services
- Concerned with how and whether information is allowed to flow from one set of systems to another, or from one state to another
- Firewalls, border routers, proxies
- Access Control Services
- Focus on the identification, authentication, and authorization of subject entities
- IAM, user authentication, SSO
- Integrity Services
- Focus on the maintenance of high- integrity systems and data through automated checking to detect and correct corruption.
- Antivirus, whitelisting, intrusion prevention systems (IPS)
Security Zones of Control
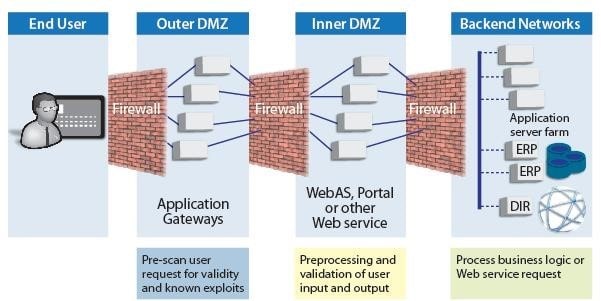
- A security zone of control is an area or grouping within which a defined set of security policies and measures are applied to achieve a specific level of security
- Zones are used to group together those entities with similar security requirements and levels of risk and ensure Source: wiki.scn.sap each zone is adequately segregated from another zone
Security Architecture Design Components
- Processors
- Memory and Storage
- Input/output Devices
- OS
- Software
- Middleware/SOA
- Embedded systems
- Client platforms – desktops, mobile devices
- Server platform
- Databases and Data systems
- Distributed Systems
- Industrial and other Control Systems
- Cryptographic Systems
- Remote Computing
- Cloud Computing
- Infrastructure and Facility
Security Architecture Framework - SABSA
- Sherwood Applied Business Security Architecture
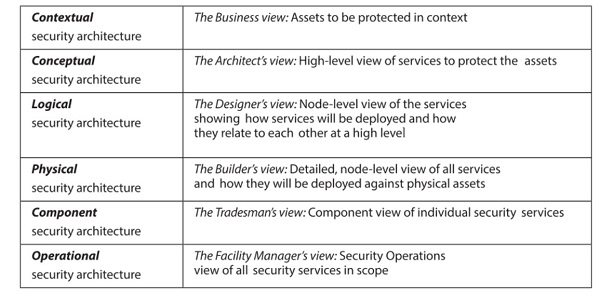
Security Frameworks
- The Orange Book
- Department Of Defense Trusted Computer System Evaluation , Criteria, December L985
- ISO/IEC 17799:2005 Code of practice for information security management
- Details individual controls for implementation
- ISO/IEC 27002:2013
- Information technology -- Security techniques -- Code of practice for information security controls
- ISO/IEC 27003:2010
- Information technology -- Security techniques -- Information security management system implementation guidance
- ISO/IEC 27005:2011
- Information technology -- Security techniques -- Information security risk management
- NIST SP800-14
- Generally Accepted Principles and Practices for Securing Information Technology Systems
Security Capabilities of IS
- Access Control Mechanisms
- Secure Memory Management
- Cryptographic Protections
- Intrusion Prevention Systems and Firewalls
- Audit and Monitoring Controls
Security Architecture Concepts
Reference Monitor
- An orange book concept that refers to an abstract machine that mediates all access to objects by subjects
- It is an auditable access control mechanism that must always be invoked
Trusted Computer Base
- Combination of all hardware, firmware and software responsible for enforcing the security policy
- Defined by the Orange Book (DoD Trusted computing system evaluation criteria)
Processor States
- Processors have atleast two states that can be used to distinguish between more and less privileged instructions
- Supervisor state (kernel mode)
- Processor is operating at the highest privilege level on the system,
- Allows the process running in supervisor state to access any system resource (data and hardware) and execute both privileged and non-privileged instructions.
- Problem state (user mode)
- The processor limits the access to system data and hardware granted to the running process
- Ideally, access to supervisor state is limited only to core OS functions that are abstracted from end-user interaction
Layering
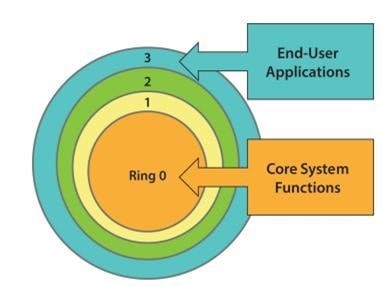
- Layering is the organization of programming into separate functional components, with each layer usually having an interface only to the layer above it and the layer below it
- Layers/rings are used to control interactions between different
execution domains with different Ring protection levels of privilege
Process Isolation
- Process isolation is used to prevent individual processes from interacting with each other, even when they are assigned to the same ring when ring protection is used
- This is done through –
- Providing distinct address spaces for each process
- Virtual mapping
- Encapsulation of processes as objects
Data Hiding
- Data hiding maintains activities at different security levels to separate these levels from each other
- This assists in preventing data at one security level from being seen by processes operating at other security levels
Covert Channels
- The Orange book defines a covert channel as: "any communication channel that can be exploited by a process to transfer information in a manner that violates the systems security policy."
Security Architecture Models
Security Models
- A security model formally defines a security policy
- Focuses on defining allowed interactions between subjects and objects at a particular moment in time
- Types
- State Machine Model
- Lattice Model
- Non-interference Model Matrix-based Model
- Information Flow Model
State Machine Models
- State Machine Models capture the current security posture of an Automated IS
(AIS).
- A state machine stores the status of an entity at a given point in time. Events trigger changes in the state of an entity
- The AIS’s secure state can change only at distinct points in time such as when an event (or clock) triggers it
- When an AIS is started, it checks to see if it is in a secure state and it will ensure that it continues to be in a secure state every time it is accessed and that the access would be done only in accordance with security policies
- The system will transition only from one secure state to another secure state
Lattice Models
- Lattice-based access control is a mechanism for enforcing one-way information flow to ensure confidentiality or integrity
- Subjects (users) are assigned security clearances
- Data is classified
- Security labels are attached to each object (i.e. every object is assigned a security class)
- The system evaluates the clearance of the user with the classification of the data to determine access
Non-interference Models
- Non-interference is the idea that actions at one level or domain should not have an influence on another level or domain
- Ensures that high-level actions (inputs) do not determine what low level users (outputs) can see
- Maintains activities at different security levels
- Complete separation between security levels minimize leakages that may happen through covert channels
Matrix-based Models
- Organizes subjects and objects into a two-dimensional access control matrix
- The matrix represents what capabilities subjects need to have to access particular objects, and also the appropriate access levels (read, write, execute)
- Does not describe the relationship between subjects (eg. if one subject gave another subject access rights)
Information Flow Models
- Information flow models are used to determine if information is being properly protected throughout a process
- Generally used to identify potentially covert channels and unintended information flow between compartments in compartmented system
The Bell-LaPadula Model (Confidentiality model)
- The Bell-LaPadula model provides for security while maintaining data sensitivity
- It is a state machine model that ensures confidentiality of an Automated IS
- Uses Mandatory Access Control
- Labels objects with classifications and subjects with clearances
- The system (reference monitor) compares the level of classification with the level of clearance and only allows access if the level of clearance is equal to or higher then the classification
- System must also make a need to know decision as specified by the system owner
The Bell-LaPadula Model
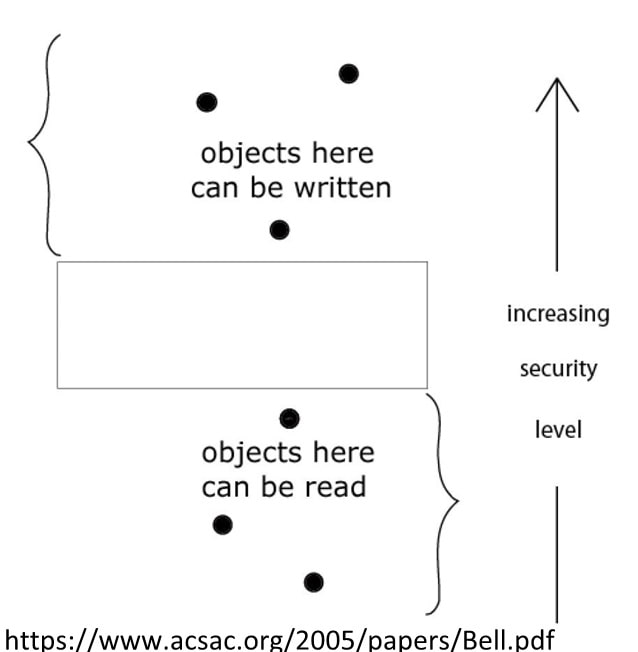
- Access modes can be of two types
- Simple security (read property) states that a subject of lower clearance cannot read an object of higher classification, but a subject of higher clearance can read down (an object of lower classification)
- The * property (write property) states that a high-level subject cannot send messages to a lower level object
- Summary: subjects can read down and objects can write or append up
Biba Integrity Model
- Ensures integrity and complements the Bell-LaPadula model
- Assigns integrity levels to subjects and objects
- Based on the premise that higher levels of integrity are more trusted than lower ones
- Access is controlled such that objects or subjects cannot have lower integrity as a result of read-write operations
Integrity Properties
- Simple integrity property (read): A subject may have read access to an object only if the security level of the subject is either lower or equal to the level of the object
- Integrity * property (write): A subject may have write access to an object only if the security level of the subject is equal or greater than that of the object
- No information can be passed by a subject to an object at a higher security level
Clark-Wilson Integrity Model
- Used for change controls in transaction systems
- Address three goals of integrity
- No changes by unauthorized subjects
- No unauthorized changes by authorized subjects
- Maintenance of internal and external consistency
- Establishes a system of subject-program-object bindings such that the subject does not have direct access to the object
Security Product Evaluation Methods and Criteria
- Standardized methods for ensuring that security products satisfy functional and assurance requirements of the organization
- Examples
- TSCEC (Orange Book)
- Trusted Network Interpretation (TNI) – Red Book
- IT Security Evaluation Criteria (ITSEC)
- Common Criteria (ISO 15408)
Please refer to Appendix for ITSEC Requirements
Common Criteria (ISO 15408)
- Evaluations are performed on information security products as well as systems
- Target Of Evaluation (TOE)
- Protection Profile (PP) - identifies security requirements relevant to a specific user for a particular purpose.
- Security Target (ST) - identifies the security properties of the TOE
Common Criteria (ISO 15408)
- The evaluation process attempts to establish a confidence level for a product's security capabilities
- Security Assurance Requirements (SARs) – examines measures taken during design, development and testing phases of a product to ensure it has the claimed security capabilities
- Evaluation Assurance Level (EAL) - A numerical rating for the depth/rigor of evaluation undertaken
- 7 levels: EAL 1 to EAL 7
Common Criteria Assurance Levels
- EAL1: Functionally Tested
- EAL2: Structurally Tested
- EAL3: Methodically Tested and Checked
- EAL4: Methodically Designed, Tested and Reviewed
- EAL5: Semi-formally Designed and Tested
- EAL6: Semi-formally Verified Design and Tested
- EAL7: Formally Verified Design and Tested
Validated product list: http://www.niap-ccevs.org/cc-scheme/vpl/
Summary
Appendix
ITSEC Requirements

PCI-DSS Requirements
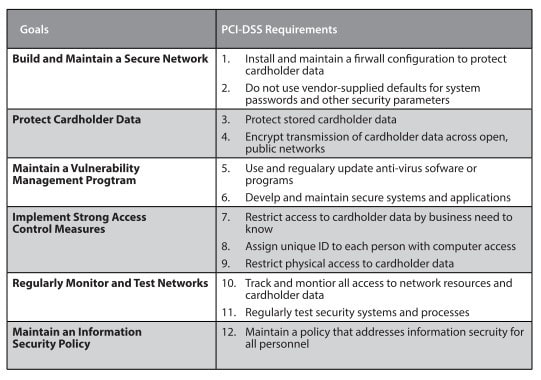
- PCI- DSS provides the security architect with a framework of specifications to ensure the safe processing, storing, and transmission of cardholder information


